SIEM is now a fundamental security component of modern enterprises.
The major reason is that each customer or tracker creates a virtual footprint in the log data of a network. SIEM systems leverage these log data to get knowledge into past incidents and events.
A SIEM system not only determines that an attack has occurred but also provides insight into how and why it occurred.
SIEM has become even more vital in recent years as organizations rebuild and upgrade to increasingly sophisticated IT infrastructures.
Despite popular belief, firewalls and antivirus software are insufficient to secure a whole network.
Zero-day cyberattacks can still breach a system’s security despite the presence of specific security measures.
SIEM (Security Information and Event Management) tools are essential to any information security strategy.
They consolidate all security events, records, and alarms into a single location, combine data, and analyze abnormal behaviors or potential threats.
A SIEM tool gives a bird’s-eye view to help discover these uncommon and frequently difficult-to-spot dangers.
In this article, we will examine the top 10 best SIEM tools.
These market leaders and pioneers in SIEM are continually enhancing and reinventing the SIEM rules.
What is SIEM?
SIEM (Security Information and Event Management) is a type of security software used to collect, analyze, and correlate security-related data from various sources within an organization’s network system.
The primary purpose of SIEM is to provide real-time visibility into security-related events and activities and help organizations detect and respond to potential threats and vulnerabilities.
SIEM typically includes two main components: security information management (SIM) and event management (SEM) systems.
The SIM component collects and stores security-related data from various sources, such as firewalls, intrusion detection systems, and antivirus software.
The SEM component is responsible for analyzing and correlating the data collected by the SIM component and for generating alerts and reports based on the information.
SIEM can help organizations to detect and respond to security threats in several ways, such as by providing real-time visibility into network activity, identifying and responding to suspicious activity, and tracking and reporting on security-related events.
SIEM can also be used to comply with regulatory requirements and industry standards related to security.
What is the Uses of SIEM ?
SIEM (Security Information and Event Management) is commonly used for several purposes, including
- Real-time monitoring and threat detection and hunting: SIEM is designed to provide real-time visibility into security-related events and activities. It can help organizations detect and respond to malware infections, network intrusion, and unauthorized access attempts.
- Compliance and regulatory requirements: SIEM can help organizations comply with various regulatory requirements and industry standards related to security, such as HIPPA, PCI-DSS, and SOX. It can provide the necessary data and reports to demonstrate compliance.
- Incident response: SIEM can help organizations quickly identify and respond to security incidents like data breaches or network intrusions. It can provide the necessary data and information to help organizations understand the scope and impact of an incident and take appropriate action.
- Log management and analysis: SIEM solutions can collect, store, and analyze log data from various sources, such as servers, network devices, and applications. This can help organizations identify and troubleshoot any issue and also detect any suspicious activity.
- Correlation of security events: SIEM solutions can correlate security events from multiple sources and identify patterns for suspicious or malicious activity. This can help organizations to detect advanced threats that might have gone unnoticed.
- Reporting and auditing: SIEM solutions can provide reporting and auditing capabilities for security-related activities. This can help organizations to identify trends, detect patterns of suspicious activity, and provide insight into the overall security posture of the organizations.
Table of Contents
What is SIEM?
What is the Uses of SIEM
10 Best SIEM Tools
1.Splunk Enterprise Security
2.AlienVault USM
3.McAfee Enterprise Security Manager
4.SolarWinds Security Event Manager
5.IBM QRadar
6.Paessler Security
7.LogRhythm NextGen SIEM Platform
8.ManageEngine Log360
9.Fortinet FortiSIEM
10.Rapid7 InsightIDR
Conclusion
Frequently Asked Questions
Also Read
10 Best SIEM Tools
- Splunk Enterprise Security
- AlienVault USM
- McAfee Enterprise Security Manager
- SolarWinds Security Event Manager
- IBM QRadar
- Paessler Security
- LogRhythm NextGen SIEM Platform
- ManageEngine Log360
- Fortinet FortiSIEM
- Rapid7 InsightIDR
SIEM (Security Information and Event Management) tools help organizations collect and analyze security-related data from various sources, such as network devices, servers, and applications.
These SIEM tools are used to identify and respond to security threats and comply with regulatory requirements.
They typically include features such as real-time event correlation, incident response, and reporting.
10 Best SIEM Tools Features
| Best SIEM Tools | KeyFeatures | Services |
|---|---|---|
| 1. Splunk Enterprise Security | 1. Real-time network monitoring 2. Asset investigator 3. Historical analysis 4. Incident response orchestration 5. User and entity behavior analytics (UEBA) 6. Compliance management and reporting 7. Risk-based prioritization and remediation 8. Asset discovery and inventory 9. Vulnerability scanning and management 10. Identity and access management (IAM) | 1. Threat intelligence framework 2. Security operations center (SOC) 3. Incident response management 4. Security information and event management (SIEM) 5. User and entity behavior analytics (UEBA) 6. Advanced threat detection 7. Compliance management 8. Risk assessment and management 9. Vulnerability management 10. Identity and access management |
| 2. AlienVault USM | 1. Intrusion detection 2. Behavioral analysis 3. Open threat exchange 4. Log management and analysis 5. Network intrusion detection and prevention 6. Host-based intrusion detection and prevention 7. File integrity monitoring (FIM) 8. Vulnerability assessment and management 9. Behavioral monitoring and anomaly detection 10. Threat intelligence feeds and correlation | 1. Threat detection and response 2. Incident management 3. Compliance management 4 Vulnerability management 5. Asset discovery and inventory 6. Log management and analysis 7. Network security monitoring (NSM) 8. File integrity monitoring (FIM) 9. Behavioral monitoring and anomaly detection 10. Threat intelligence feeds and correlation |
| 3. McAfee Enterprise Security Manager | 1. Log consolidation 2. Live to monitor 3. Links to Active Directory 4. Threat intelligence feeds and correlation 5. Incident prioritization and response 6. Forensic analysis and reporting 7. User and entity behavior analytics (UEBA) 8. Compliance reporting and management 9. Advanced correlation and analytics 10. Log management and analysis | 1. Log collection and aggregation 2. Threat detection and response 3. Incident management and response 4. Compliance reporting and management 5. Advanced correlation and analytics 6. User and entity behavior analytics (UEBA) 7. Asset discovery and inventory 8. Vulnerability management 9. Network security monitoring (NSM) 10. File integrity monitoring (FIM) |
| 4. SolarWinds Security Event Manager | 1. Automated log searches for breaches 2. Live anomaly detection 3. Historical analysis 4. System alerts 5. 30-day free trial 4. Real-time event collection and correlation 5. Log management and analysis 6. Threat detection and response 7. User and entity behavior analytics (UEBA) 8. Compliance reporting and management 9. Asset discovery and inventory 10. Vulnerability scanning and management | 1. Log collection and analysis 2. Threat detection and response 3. Incident management and response 4. Compliance reporting and management 5. User and entity behavior analytics (UEBA) |
| 5. IBM QRadar | 1. Log management 2. Intrusion detection 3. Analytical functions 4. Log management and analysis 5. Network security monitoring (NSM) 6. Threat detection and response 7. Incident prioritization and response 8. User and entity behavior analytics (UEBA) 9. Asset discovery and inventory 10. Vulnerability scanning and management | 1. Log management and analysis 2. Network security monitoring (NSM) 3. Threat detection and response 4. Incident management and response 5. User and entity behavior analytics 6. Asset discovery and inventory Vulnerability scanning and management 7. File integrity monitoring 8. Host-based intrusion detection and prevention 9. Network intrusion detection and prevention 10. Compliance reporting and management |
| 6. Paessler Security | 1. Using maps and displays, illustrates the network. 2. Alerts that are adaptable when concerns are discovered. 3. Customizable instrument with custom inputs and HTTP API. 4. Utilize SNMP to monitor various devices. 5. Network monitoring and mapping 6. Real-time monitoring and alerts 7. Network traffic analysis 8. Application monitoring and performance management 9. Cloud monitoring 10. Virtualization monitoring | 1. Virtualization monitoring 2. SNMP monitoring 3. WMI monitoring 4. NetFlow monitoring 5. Bandwidth monitoring 6. Customizable dashboards and reports 7. API for integration with third-party systems 8. Remote probe functionality for distributed networks 9. Mobile app for monitoring on-the-go 10. Multi-user support with role-based access control |
| 7. LogRhythm NextGen SIEM Platform | 1. AI-based 2. Log file management 3. Guided analysis 4. SNMP monitoring 5. WMI monitoring 6. NetFlow monitoring 7. Bandwidth monitoring 8. Customizable dashboards and reports 9. API for integration with third-party systems 10. Remote probe functionality for distributed networks | 1. 24/7 technical support and customer service 2. Training and certification programs 3. Regular software updates and maintenance 4. Security operations center (SOC) services 5. Managed security services (MSS) 6. Threat intelligence services 7. Compliance management and reporting services 8. Security consulting and assessment services 9. Incident response and forensic services 10. Integration services with third-party solutions |
| 8. ManageEngine Log360 | 1. Logging from on-site and cloud systems 2. Sources of threat intelligence 3. Packaged alerts forwarded to the service desk 4. User and entity behavior analytics (UEBA) 5. Compliance management and reporting 6. Log source integration and management 7. Audit trail management 8. Log data retention and archiving 9. Customizable dashboards and reports 10. Active Directory auditing | 1. Real-time event correlation and alerts 2. Threat detection and response 3. User and entity behavior analytics (UEBA) 4. Compliance management and reporting 5. Log source integration and management 6. Audit trail management 7. Log data retention and archiving 8. Customizable dashboards and reports 9. Active Directory auditing 10. File integrity monitoring (FIM) |
| 9. Fortinet FortiSIEM | 1. Choice of data processing volumes 2. Includes attack responses 3. Compliance reporting 4. Event correlation and analysis 5. Threat detection and response 6. Centralized logging and reporting 7. Configuration and policy management 8. Threat intelligence and updates 9. Deception technology for detecting and responding to attacks 10. Network access control | 1. FortiSIEM 2. FortiAnalyzer 3. FortiManager 4. FortiGuard Security Services 5. FortiDeceptor 6. FortiNAC 7. FortiToken 8. FortiEDR 9. FortiClient |
| 10. Rapid7 InsightIDR | 1. The simple interface makes it simple for security professionals to obtain threat detection for incident response planning. 2. Integrated detection and response tools expedite the removal of threats by streamlining response operations. 3. Accessible threat investigations enable security teams to respond rapidly and take measures to prevent recurrences. 4. It is simple to deploy due to various pre-configured options 5. Network traffic analysis 6. Automated threat detection and response 7. Incident investigation and forensics 8. Compliance reporting and auditing 9. User activity monitoring 10. Integration with third-party security tools | 1. Log management and retention 2. User and entity behavior analytics (UEBA) 3. Endpoint detection and response (EDR) 4. Cloud infrastructure monitoring 5. Network traffic analysis 6. Automated threat detection and response 7. Incident investigation and forensics 8. Compliance reporting and auditing 9. User activity monitoring 10. Integration with third-party security tools |
1. Splunk Enterprise Security

For security operations center (SOC) tasks, Splunk is a popular SIEM tool.
Differentiating itself from competitors, it incorporates insights into its SIEM core.
As it scans for security flaws and flags suspicious behavior, the system can monitor data from networks and devices in real time.
Enterprise Security’s Notables feature allows users to customize notifications.
When combined with Splunk’s data analysis foundation package, Splunk Enterprise Security becomes a very versatile solution.
In addition to utilizing the included rules, you have the option to create your own analytic routines, automatic defense rules, and query sets for threat hunting.
Whatever kind of business you run, Splunk Enterprise Security can help.
Nevertheless, big companies are more likely to be interested in this bundle than small enterprises because of its price and power.
Splunk SIEM Software Features
- Splunk Enterprise Security combines network, endpoint, and application data to detect and respond to attacks in real time.
- The platform centralizes incident alerts, events, and resolution.
- Splunk Enterprise Security may link to third-party threat intelligence feeds for the latest threats and gaps.
- The software uses machine learning and advanced analytics to detect suspicious behavior.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Can use behavior analysis to identify threats that aren’t detected by logs. | 1. Pricing is not apparent; a quote from the vendor is required. |
| 2. Excellent user interface, highly attractive, and simple to modify | 2. More suitable for large organizations |
| 3. Event prioritization is simple. | 3. For queries, Search Processing Language (SPL) is used, which increases the learning curve. |
| 4. Enterprise-focused | |
| 5. Compatible with Linux and Windows |
Price
You can get a free trial and personalized demo from here.
2. AlienVault USM

Among the most reasonably priced SIEM solutions on this list, AlienVault (previously AT&T Cybersecurity) is an enticing choice.
With intrusion detection, activity monitoring, and vulnerability analysis included in, this is a typical best SIEM software.
As one would expect from a scalable platform, AlienVault has built-in analytics.
AlienVault is a great option because it is inexpensive, and it is very reliable cloud-based SIEM software.
Another attractive aspect of this danger detection system is Open danger Sharing, which is part of the alien Vault platform.
Features
- AlienVault USM effortlessly locates and lists all network assets, whether real, virtual, or cloud.
- The software evaluates assets for vulnerabilities and ranks them by risk.
- AlienVault USM detects and stops known and novel attacks in real time using threat intelligence and behavioral analysis.
- AlienVault USM stores and links log data from network devices, servers, and apps.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Scan log files and generate vulnerability assessment reports based on network-scanned devices and apps. | 1. Would there be a longer trial time |
| 2. A platform powered by users enables customers to contribute their threat data for system improvement. | 2. Logs may be more difficult to search and read. |
| 3. Utilizes artificial intelligence to assist administrators in detecting threats. | 3. Wish there were more choices for integration with other security systems |
Price
You can get a free trial and personalized demo from here.
3. McAfee Enterprise Security Manager

Among security information and event management (SIEM) programs, McAfee Enterprise Security Manager has a stellar reputation for its analytics.
The user can get various logs from numerous devices through the Active Directory infrastructure.
You should pay great attention whenever McAfee offers a suitable security solution because it is a powerful and reliable brand.
McAfee’s correlation engine simplifies the process of integrating many data sources.
Security event detection is made much easier by this. When it comes to support, users can access either McAfee Enterprise Technical Support or McAfee Business Technical Support.
Twice yearly, the user can request a visit from a Support Account Manager to their site.
Businesses of a medium to big size that are looking for an all-inclusive platform for managing safety events should consider the McAfee platform.
Features
- McAfee Enterprise Security Manager monitors events and sends real-time notifications to help businesses fix security issues.
- The platform can gather, store, and analyze log data from network devices, servers, and apps.
- McAfee Enterprise Security Manager detects and stops known and novel threats in real time using machine learning and powerful analytics.
- The platform includes PCI DSS, HIPAA, and GDPR compliance reports and templates.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Utilizes a robust correlation engine to discover and eliminate risks more quickly. | 1. Interface is frequently crowded and overwhelming |
| 2. Highly compatible with Active Directory environments | 2. A quote must be obtained from sales. |
| 3. Designed with massive networks in mind | 3. More integration options would be beneficial. |
| 4.Enterprise-scale scalability. |
Price
You can get a free trial and personalized demo from here.
4. SolarWinds Security Event Manager
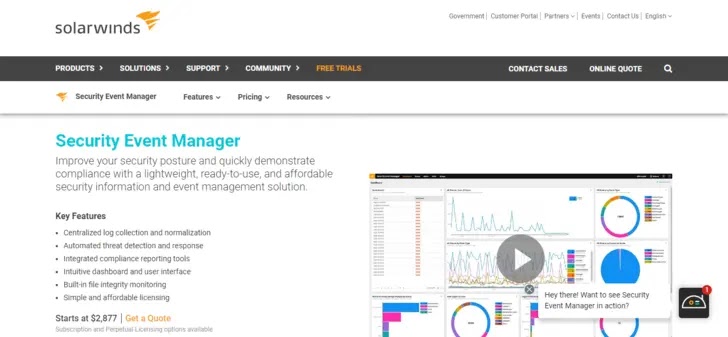
Among the many affordable security information and event management (SIEM) solutions available, SolarWinds Security Event Manager (SEM) stands out.
Sophisticated log management and reporting are just two of the many features included in the SEM that are typical of SIEM systems.
SolarWind is a great tool for businesses who want to protect their network infrastructure against future attacks by actively managing it using Windows event logs. It offers thorough real-time incident response.
An on-premises solution that can communicate with cloud services is SolarWinds Security Event Manager.
By utilizing this method, a single server may be used to keep tabs on several websites and cloud storage.
The intuitive and thorough design of SEM’s user interface is one of the program’s most notable characteristics.
Because the dashboards are so straightforward, it’s easy for the user to understand any discrepancies.
The organization’s round-the-clock support is a huge plus, so you can always call them for aid whenever you need it.
Features
- SolarWinds Security Event Manager’s real-time event tracking and alerting help businesses detect and resolve security incidents.
- The platform can gather, store, and analyze log data from network devices, servers, and apps.
- SolarWinds Security Event Manager uses advanced analytics and machine learning to detect and stop known and undiscovered attacks in real time.
- SolarWinds Security Event Manager centralizes security issues. It has process for investigating, containing, and fixing issues.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Enterprise-eccentric SIEM with a vast selection of integrations | 1. SEM is a complex SIEM platform designed for professionals that requires time to completely master. |
| 2. Log filtering without the need to learn a specific query language | 2.Some users report occasional performance difficulties. |
| 3.Multisystem log collecting and correlation. | |
Price
You can get a free trial and personalized demo from here.
5. IBM QRadar

IBM’s SIEM solution has been steadily rising in the rankings of the best products on the market for the last many years.
In order to keep mission-critical systems online, the platform offers a suite of features for managing logs, analytics, data collection, and intrusion detection.
The QRadar Log Manager centralizes all log management. When it comes to analytics, QRadar covers almost all bases.
Like the majority of the alternatives, IBM’s QRadar SIEM software is a top-notch log management system.
Our recommendation is based on the SIEM’s analytical capabilities, especially its attack simulation module.
In order to simulate potential threats, the system incorporates analytics for risk modeling.
A wide range of virtual and physical network configurations can be tracked by this. If you are looking for a versatile SIEM system, IBM QRadar is a great choice and one of the most complete options on our list.
Features
- IBM QRadar helps businesses detect and fix security issues by monitoring events and sending real-time notifications.
- The platform can gather, store, and analyze log data from network devices, servers, and apps.
- Machine learning and advanced analytics let IBM QRadar detect and stop known and unexpected threats in real time.
- IBM QRadar centralizes security occurrences for investigation, containment, and resolution.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Uses artificial intelligence to generate risk evaluations | 1. It does not integrate with other SOAR and SIEM platforms. |
| 2. Can evaluate the impact of simulated attacks on a network | 2. Need more effective flow analysis tools |
| 3. Has a straightforward but efficient interface | |
Price
You can get a free trial and personalized demo from here.
6. Paessler Security

Customers get access to all the tools necessary to monitor their whole IT infrastructure with Paessler PRTG SIEM tools. This includes all devices, traffic, apps, and more.
You may use this tool to see how much bandwidth various devices and apps use.
Additionally, the software allows for the monitoring of specific datasets using SQL queries and specifically designed PTRG sensors.
You can manage all of your programs and get detailed data for each one on your network using this software.
The real-time monitoring of all server types is another area where the platform really shines. It rates them according to how easily accessible, dependable, and trustworthy they are.
Features
- PRTG Network Monitor detects security issues by monitoring network devices, servers, and apps in real time.
- The platform’s SNMP tracking tools can detect security problems by collecting and analyzing network device data.
- PRTG Network Monitor packet sniffing allows you analyze network data for security threats.
- Secure notification distribution via encrypted pathways prevents essential alerts from being altered.
- Monitors without compromising security because it works with firewalls and provides firewall-friendly setups.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. The software is user-friendly, highly configurable, and packed with features. | 1. The security features are not as advanced as those of other dedicated security solutions. |
| 2. Its maps and interfaces enable you to understand the whole network infrastructure, making monitoring and management of all devices, apps, and traffic, among many other things, much simpler. | 2. May require additional resources and expertise to utilize all of its features fully. |
| 3. Optimal for Feature-dense network monitoring. | |
| 4. 30-day free trial |
Price
You can get a free trial and personalized demo from here.
7. LogRhythm NextGen SIEM Platform

LogRhythm is now widely recognized as a frontrunner among SIEM Tools. Behavioral analysis, log correlation, and AI for machine learning are all features of this platform.
A cloud-based product, LogRhythm NextGen SIEM is similar to Datadog, Logpoint, Exabeam, AlienVault, and QRadar.
We couldn’t leave this tool off the list of recommendations as it’s just as effective as the others.
With this system, you can connect to a wide variety of devices and log types. You can control most of your configuration settings with the Deployment Manager.
As an example, the Windows Host Wizard can be used to sort through Windows logs.
Features
- Companies can collect and store logs from many IT infrastructure sources using LogRhythm NextGen SIEM systems.
- Central log management lets users search, correlate, and assess log data in real time.
- The platform’s powerful analytics detect and stop security risks using AI and ML.
- Advanced incident reaction features on the LogRhythm NextGen SIEM Platform help enterprises swiftly and efficiently address security risks.
- The app’s threat intelligence tools display real-time security threats and weaknesses.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Utilizes simple wizards to configure log collection and other security chores, making it an easier-to-use tool for beginners. | 1. Wish there were a trial option |
| 2. Highly flexible and visually appealing UI. | 2. Cross-platform compatibility would be a great attribute. |
| 3. Utilizes artificial intelligence and machine learning to analyze behavior. |
Price
You can get a free trial and personalized demo from here.
8. ManageEngine Log360

On-premises users can take use of ManageEngine Log360, a package that includes agents for several operating systems and cloud services.
After collecting log messages, the agents send them to the server’s main body. The use of agents to collect data from more than 700 different apps.
They also handle notifications from Windows Event and Syslog. The log server collects all the log messages, sorts them, and puts them in a dashboard data viewer.
Details, such the response time, are shown in the application’s log messages as well. Among the many tools offered by ManageEngine, the EventLog Analyzer is part of ManageEngine Log360.
Features for managing logs and threats, keeping tabs on users, checking file integrity, and administering Active Directory are all part of the EventLog Analyzer suite.
Features
- The platform stores logs from various IT infrastructure components.
- ManageEngine Log360 detects real-time security threats using advanced analytics and machine learning.
- The platform’s advanced incident reaction features let firms respond to security issues swiftly.
- ManageEngine Log360 automates compliance reporting and monitoring to help firms satisfy several standards.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. File integrity surveillance | 1. Not compatible with Linux |
| 2. Windows Events and Syslog notifications are merged into a single format. | 2.Support and documentation may not cover all functions. |
| 3.Compliance reporting and auditing. | |
| 4.IT security tool and platform integration. |
Price
You can get a free trial and personalized demo from here.
9. Fortinet FortiSIEM
The Fortinet Security Fabric is an all-inclusive business protection system that can be built using Fortinet FortiSIEM or other Fortinet technologies.
With its custom-designed microchips for fast data processing, Fortinet hardware appliances enjoy an amazing reputation in the cybersecurity field.
It is possible to run FortiSIEM as a virtual appliance or install it on a physical device. This system is also available as a service through AWS.
For maximum security, use FortiSIEM in conjunction with the FortiGate firewall or a SASE system.
The FortiNetData safety rules often necessitate that systems like FortiSIEM collect and store log information. You may get reports that are compliant with PCI-DSS, HIPAA, GLBA, and SOX with FortiSIEM.
An additional crucial feature of this system is its ability to be set up to automatically respond and eradicate any threats it identifies.
Features
- Fortinet FortiSIEM provides centralized log management capabilities that enable organizations to collect, store, and analyze log data from various sources across their IT infrastructure.
- The platform uses advanced analytics and machine learning to detect potential security threats in real time.
- It can automatically identify and prioritize high-risk threats based on various factors, including threat severity, threat category, and potential impact.
- Fortinet FortiSIEM offers advanced incident response capabilities that can help organizations respond to potential security threats quickly and effectively.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Combines well with firewalls and traffic shaping services. | 1. The prices are among the highest on the market. |
| 2. Options for implementing virtual network security | 2.Some users report occasional performance difficulties. |
| 3. implements analytics for user and entity activity (UEBA) | |
| 4.Scalability for varied IT environments. |
Price
You can get a free trial and personalized demo from here.
10. Rapid7 InsightIDR

Startup Rapid7 specializes in cybersecurity with an emphasis on automation-based security enhancement solutions, intelligence, and monitoring.
Built on top of Rapid7’s Insight system, InsightIDR is a SIEM and XDR platform that integrates with the vendor’s advanced threat, orchestration and management, vulnerability assessments, application, and cloud security technologies.
If a customer purchases InsightIDR along with any of the other Insight products, they will only need to learn how to use one set of tools.
Features
- Due to its unified log management, InsightIDR can collect, store, and analyze log data from various IT infrastructure components.
- The software detects real-time security threats using advanced analytics and machine learning.
- It automatically finds and ranks high-risk threats by category, severity, and impact.
- Advanced incident reaction features in InsightIDR let firms respond swiftly to security risks.
- UBA features can help firms identify security concerns by analyzing user behavior throughout their IT infrastructure.
Demo Video
| What is Good ? | What Could Better ? |
|---|---|
| 1. Provide a comprehensive view of network activity, including user behavior and endpoint activity. | 1. It may be expensive for some organizations. |
| 2. Includes advanced threat detection capabilities, such as machine learning-based detection. | 2. It may require additional resources and expertise to utilize all of the features fully. |
| 3. Offers incident response tools, such as automated incident triage and forensic analysis. | |
| 4. Integrates with other security tools, such as vulnerability scanners and firewalls. |
Price
You can get a free trial and personalized demo from here.
Conclusion
It is essential to gradually deploy a SIEM solution, regardless of the Best SIEM tools you decide to implement.
There is no expedited method for implementing a SIEM system.
The most effective technique for integrating a SIEM platform into an IT environment is to do so gradually.
This entails implementing any solution separately. Aim for both real-time monitoring and log analysis capabilities.
This allows you to assess your IT infrastructure and enhance the implementation procedure.
Implementing a SIEM system gradually will allow you to determine if you’re compromising your organization to hostile attacks.
When implementing a SIEM system, a crystal-clear understanding of the objectives you hope to achieve is of utmost importance.
Frequently Asked Questions
The SIEM cost can vary widely depending on a number of factors, such as the size of the organization, the level of customization and support required, and the specific features and capabilities of the system.
Some SIEM solutions are available as a service, with costs based on the number of events or log data that are processed. In contrast, others are sold as on-premises software with costs based on the number of servers or devices that are being monitored.
On average, a basic SIEM solution can cost anywhere from a few thousand dollars per year to several hundred dollars per year or more for a large organization.
There are many different Security Information and Event Management (SIEM) solutions available on the market. Still, some of the most popular and widely used include:
Splunk Enterprise Security
AlienVault USM
McAfee Enterprise Security Manager
SolarWinds Security Event Manager
IBM QRadar
Paessler Security
LogRhythm NextGen SIEM Platform
ManageEngine Log360
Fortinet FortiSIEM
Rapid7 InsightIDR
These are some of the most popular SIEMs tools available in the market, but there are many other options available as well.
The choice of BEST SIEM tools will depend on the specific needs of the organizations, and it is important to evaluate the features and capabilities of each tool in order to choose the one that best meets the organization’s requirements
Also Read
10 Best Advanced Endpoint Security Tools
Top 10 Best Free Penetration Testing Tools
Top 10 Dangerous DNS Attacks Types and The Prevention Measures
Top 10 AWS Security Tools to Protect Your Environment and Accounts
Top 10 SMTP Test Tools to Detect Server Issues & To Test Email Security
10 Best Free Forensic Investigation Tools


.webp)
