Google Researchers Detailed Tools Used by APT41 Hacker Group
Advanced persistent threat group APT41 launched an extended attack that successfully compromised a number of companies in the media and entertainment, IT, transportation and logistics, and automotive industries.
The campaign's target organizations came from a...
New InnoSetup Malware posing As MS Office Crack To Evade detection
A new malware strain disguised as cracks and commercial tools utilizes a just-in-time generation tactic, and upon a download request, a unique malware variant with the same functionalities is created for the user, which...
Moonstone Sleet New North Korean Hacker Group With Unique Tricks
Microsoft has identified a new North Korean threat actor, now tracked as Moonstone Sleet (formerly Storm-1789).
This actor uses a combination of many tried-and-true techniques used by other North Korean threat actors and unique attack...
Chinese Hackers Using ORB Proxy Networks For Stealthy Cyber Attacks
Researchers found that cyber espionage groups with ties to China are increasingly using complicated proxy networks called Operational Relay Box (ORB) networks.
These networks are made up of mesh networks made from hacked devices...
LATRODECTUS Loader Getting Popular Among Cybercriminals, Is It Replacing ICEDID!
Hackers use loaders to bypass security measures and run harmful code in a genuine process's memory themselves.
This makes it possible for malware payloads to be quietly loaded into the system without being discovered by...
How to Use Threat Intelligence Feeds for SOC/DFIR Teams
Threat intelligence feeds provide real-time updates on indicators of compromise (IOCs), such as malicious IPs and URLs.
Security researchers and organizations share IOCs with feed vendors, who then analyze and validate them before distributing...
Criminal IP and Quad9 Collaborate to Exchange Domain and IP Threat Intelligence
Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address...
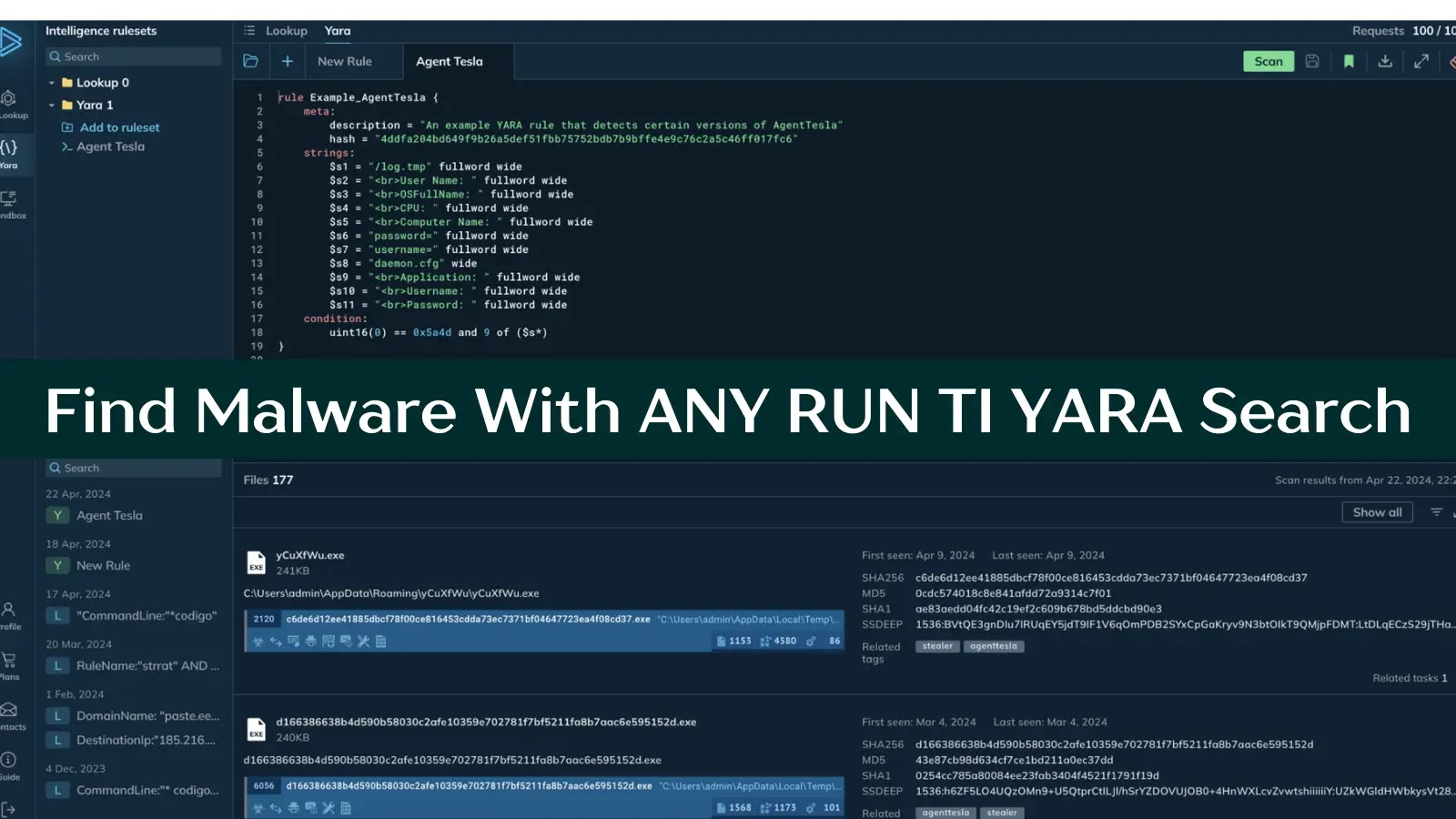
Find Malware With ANY RUN Threat Intelligence YARA Search by File Contents
YARA is a rule-based malware detection tool that utilizes regular expressions and textual/binary signatures to create descriptions (rules) for identifying malicious files.
Within ANY.RUN TI, YARA Search allows you to write, edit, test, download, and...
New Redline Stealer Variant Leverages Lua Bytecode For Stealthiness
Redline Stealer is a powerful information-stealing malware, and hackers often exploit this stealthy stealer to gain unauthorized access to a victim's sensitive data.
Threat actors can steal many sensitive and valuable data by exploiting the...
Cyber Security News Weekly Round-Up (Vulnerabilities, Cyber Attacks, Threats & New Stories)
Welcome to the Cyber Security News Weekly Round-Up. Each week, we will explore the latest cyber threats, vulnerabilities, and notable stories that have shaped the cybersecurity landscape.
From sophisticated malware attacks to innovative phishing schemes,...








%20(1).webp)




.webp)