Network security is paramount in today’s digital landscape, where organizations face increasingly sophisticated threats.
This guide presents a detailed Network Security checklist with examples to help you establish robust protection and minimize vulnerabilities.
Network Security Musts: The 7-Point Checklist – Download Free – E-Book

Network Security and Risks 2024
Network security is essential for digital data and system protection. Protecting networks and data against unauthorised access, abuse, and damage requires many steps. Network security is always changing, with new threats and difficulties. Key network security factors and risks:
Cyber Threats: Malware, ransomware, phishing, and DDoS assaults can target networks. These dangers can cause data breaches, financial losses, and brand harm.
Software and Hardware Vulnerabilities: Networks use vulnerable software and hardware. Attackers can leverage these vulnerabilities to obtain access or disrupt services. Regular updates and patches are needed to fix these vulnerabilities.
Insider threats: Organizational insider threats can potentially pose a security issue. Insiders with network access can purposefully or inadvertently violate security. Proper access restrictions and internal activity monitoring are crucial.
Emerging Technologies: Cloud computing, IoT, and AI provide new security risks. These technologies are increasingly incorporated into network infrastructures, making security essential.
Compliance and Regulatory Risks: Organizations must follow data privacy and cybersecurity rules. Legal sanctions and customer distrust might come from noncompliance.
Third-Party concerns: Third-party vendors and service providers can increase security concerns for organizations. These third parties must meet high security requirements.
Remote Work Security: Security of remote connections and equipment outside the workplace is crucial as remote work grows.
Social Engineering: It includes tricking people into disclosing private information or compromising network security. Employees need social engineering awareness and response training.
Zero-Day Exploits: These assaults target software or hardware vulnerabilities before the developer fixes them. They are difficult to guard against since they are unknown.
APTs: Long-term, targeted cyberattacks in which an attacker gets network access and goes undiscovered. Complex APTs demand sophisticated defenses.
Network Security Checklist With Ensuring Robust Protection
Network Infrastructure Security:
1.1 Firewall Configuration:
- Ensure that firewalls are correctly configured to restrict unauthorized access.
- Configure default deny rules and permit only necessary traffic.
- Regularly update firewall firmware and security policies.
1.2 Intrusion Detection and Prevention Systems (IDPS):
- Deploy IDPS to detect and prevent malicious activities.
- Continuously monitor network traffic for suspicious behavior and take immediate action.
1.3 Virtual Private Networks (VPNs):
- Employ VPNs to establish secure connections between remote locations.
- Encrypt data transmission to protect against eavesdropping.
1.4 Wireless Network Security:
- Change default passwords and implement robust encryption protocols (e.g., WPA2 or WPA3).
- Enable MAC to address filtering and disable SSID broadcasting.
- Regularly update firmware for wireless access points.
Access Control Measures:
2.1 User Authentication:
- Implement robust password policies (e.g., minimum length, complexity requirements, regular password changes).
- Enable multi-factor authentication (MFA) for added security.
- Disable default accounts and enforce account lockouts after failed login attempts
2.2 Privileged Account Management:
- Restrict access to privileged accounts.
- Regularly review and update access rights based on job roles and responsibilities.
- Implement session monitoring and logging for privileged accounts.
2.3 Role-Based Access Control (RBAC):
- Assign access rights based on job roles.
- Review and update access permissions regularly.
- Remove access rights promptly for terminated employees.
Data Protection and Encryption:
3.1 Data Classification:
- Classify data based on its sensitivity level (e.g., confidential, internal, public).
- Implement appropriate security controls based on classification.
3.2 Data Encryption:
- Encrypt sensitive data at rest and during transit.
- Utilize robust encryption algorithms (e.g., AES-256) and secure critical management practices.
3.3 Backup and Disaster Recovery:
- Regularly back up critical data and test restoration processes.
- Store backups offsite or in secure cloud environments.
- Develop and document a comprehensive disaster recovery plan.
Network Monitoring and Incident Response:
4.1 Log Management and Analysis:
- Enable logging for network devices and critical systems.
- Implement log analysis tools to identify security incidents promptly.
- Retain logs for an appropriate duration as per legal and compliance requirements.
4.2 Security Information and Event Management (SIEM):
- Deploy a SIEM solution for real-time monitoring and correlation of security events.
- Define alert thresholds and automated responses for efficient incident response.
4.3 Incident Response Plan:
- Develop a documented incident response plan that includes clear roles and responsibilities.
- Regularly test and update the plan to ensure effectiveness.
4.4 Security Awareness and Training:
- Conduct regular security awareness training for employees.
- Educate users about phishing attacks, social engineering, and safe browsing practices.
Network Security Policies
Define a Network Security Policy:
- The first step in securing your network is to define a network security policy.
- This policy should clearly state what is expected of all employees and the consequences for violating these policies.
- The policy should also outline the security measures that will be put in place to protect the network.
Examples of security policies include:
- Password Policy: This policy should outline the rules for creating and using passwords, such as minimum length, complexity requirements, and password expiration.
- Access Control Policy: This policy should outline who has access to what information and resources and how that access is granted.
- Acceptable Use Policy: This policy should outline what is and is not allowed on the company network, such as personal use, downloading unauthorized software, and accessing inappropriate content.
Conduct Regular Security Audits:
Regular security audits are essential for identifying potential vulnerabilities in the network.
These audits should be conducted internally and externally, including reviewing all network devices and applications.
Examples of security audits include:
- Vulnerability Scans: These scans check for vulnerabilities in the network that hackers could exploit.
- Penetration Testing: This test involves simulating a real-world attack on the network to identify weaknesses.
- Security Assessment: This assessment provides an overview of the current state of the network’s security and identifies areas that need improvement.
Install and Configure Firewalls:
Firewalls are an essential component of network security. They are designed to monitor and filter incoming and outgoing traffic to prevent unauthorized access to the network.
Firewalls can be hardware or software-based and should be configured to block all unnecessary traffic. Examples of firewall configurations include:
- Port Blocking: This involves blocking traffic to specific ports that are not needed for the operation of the network.
- IP Address Blocking: This involves blocking traffic from specific IP addresses or ranges of IP addresses known to be malicious.
- Stateful Inspection: This involves monitoring the state of network connections to ensure that only authorized traffic is allowed.
Implement Intrusion Detection and Prevention Systems:
Intrusion Detection and Prevention Systems (IDPS) are designed to detect and prevent unauthorized access to the network.
They can be hardware or software-based and should be configured to alert administrators if suspicious activity is detected.
Examples of IDPS configurations include:
- Signature-Based Detection: This involves comparing network traffic to a database of known attack signatures.
- Anomaly-Based Detection: This involves comparing network traffic to a baseline of regular activity to detect any unusual behavior.
- Behavioral Analysis: This involves monitoring user behavior to identify potential insider threats.
Secure Wireless Networks:
Wireless networks are particularly vulnerable to attacks, as they are often left unsecured. To secure wireless networks, businesses should:
- Use WPA2 or WPA3 Encryption: This ensures that data transmitted over the network is encrypted and secure.
- Change Default Settings: Default settings on wireless devices are often insecure, so it is essential to change them to something more secure.
- Use Strong Passwords: Strong passwords should be used to prevent unauthorized access to the network.
Complete Network Security Checklist: Protecting Your Digital Infrastructure
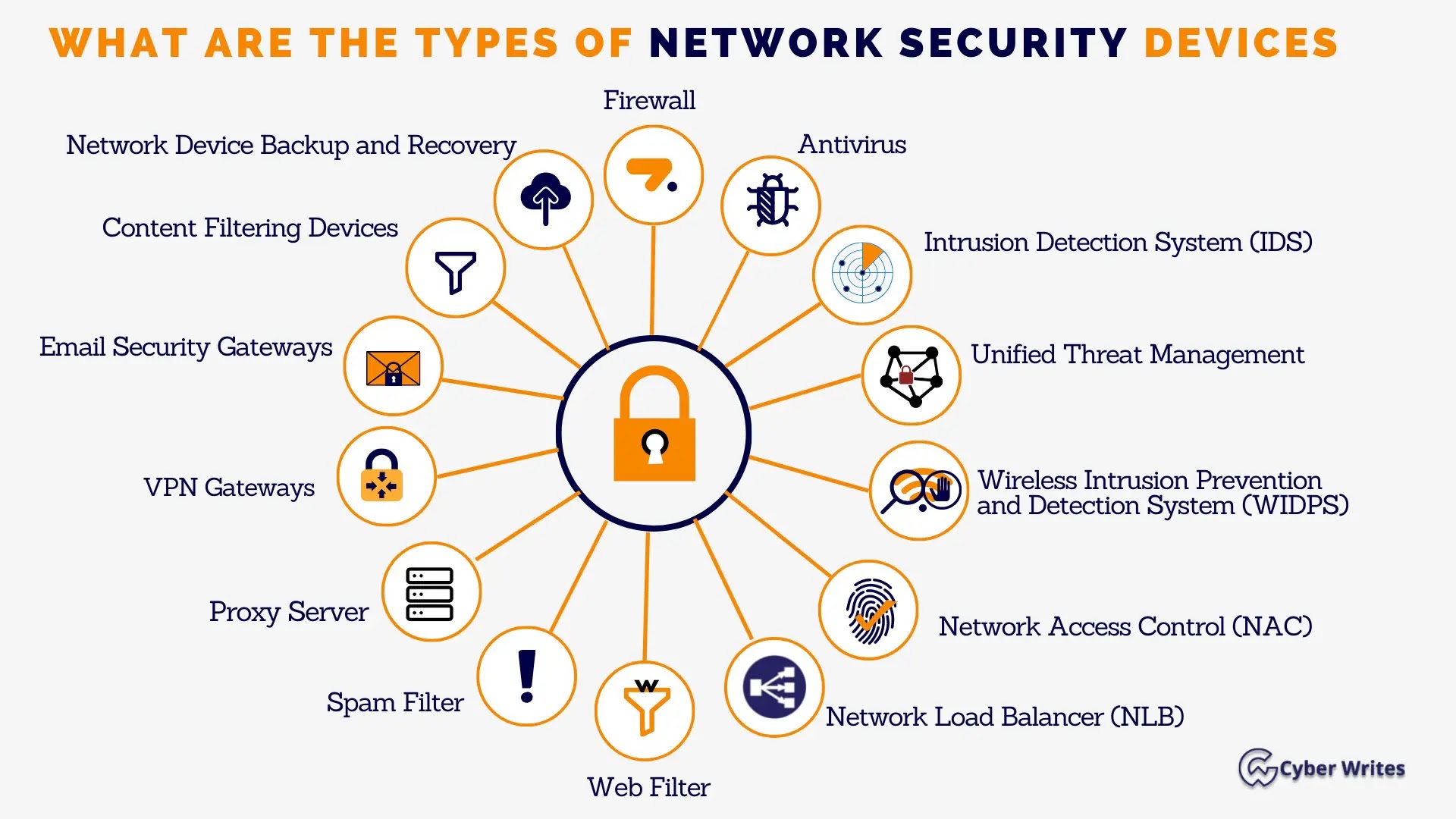
In today’s interconnected world, network security is crucial in safeguarding sensitive information and protecting digital assets.
A comprehensive network security checklist is essential to ensure your network’s integrity, confidentiality, and availability.
This article will provide a detailed checklist of network security measures and relevant examples to help you fortify your digital infrastructure.
Access Control:
1.1 Implement robust user authentication mechanisms, such as multifactor authentication (MFA), to prevent unauthorized access. Example: Require employees to use a combination of passwords and biometric authentication (e.g., fingerprints or facial recognition) to access critical systems.
1.2 Enforce the principle of least privilege (PoLP), granting users only the necessary permissions to perform their tasks. Example: Limit user access to sensitive data by implementing role-based access control (RBAC), ensuring that each user has the minimum required privileges.
1.3 Regularly review and update access privileges, revoking access for employees who have changed roles or left the organization. Example: Conduct periodic audits to verify that former employees or contractors can no longer access critical systems.
Network Infrastructure Protection:
2.1 Keep network devices (routers, switches, firewalls) up to date with the latest firmware and security patches. Example: Regularly check for vendor updates and promptly apply them to address known vulnerabilities.
2.2 Implement network segmentation to isolate sensitive systems from less secure areas and limit the potential impact of a breach. Example: Separate the finance department’s network from the general employee network to reduce the risk of unauthorized access to financial data.
2.3 Deploy intrusion detection and prevention systems (IDS/IPS) to monitor network traffic and detect and block malicious activity. Example: Set up an IPS to detect and prevent known attack patterns, such as denial-of-service (DoS) attacks or SQL injections.
Data Protection:
3.1 Encrypt sensitive data at rest and in transit to prevent unauthorized access. Example: Use Secure Sockets Layer (SSL)/Transport Layer Security (TLS) certificates to encrypt data transmitted over the internet, such as login credentials or financial information.
3.2 Regularly back up critical data and verify the integrity of backups to ensure quick recovery in case of data loss or system compromise. Example: Perform daily or weekly backups of essential files to a secure offsite location and periodically test the restoration process.
3.3 Implement data loss prevention (DLP) mechanisms to monitor and control the movement of sensitive data. Example: Configure DLP software to detect and block the transmission of sensitive information, such as credit card numbers or social security numbers, via email or removable storage devices.
Endpoint Security:
4.1 Implement robust endpoint security software such as antivirus and anti-malware solutions on all endpoints (computers, laptops, mobile devices). Example: Install reputable antivirus software that regularly updates its virus definition database and performs real-time scanning to detect and remove malware.
4.2 Enforce strict patch management practices to keep operating systems and applications updated with the latest security patches. For example, configure systems to download and install security updates promptly and automatically address vulnerabilities.
4.3 Educate employees about social engineering attacks and phishing scams to minimize the risk of unauthorized access via compromised endpoints. Example: Conduct regular security awareness training sessions to teach employees to recognize and report suspicious emails or phone calls.
Monitoring and Incident Response:
5.1 Implement a security information and event management (SIEM) system to collect and analyze logs from various network devices and systems.
Example: Use a SIEM tool to correlate events from firewalls, intrusion detection systems, and servers, enabling early detection of security incidents.
Conclusion
Implementing a comprehensive network security checklist is crucial to protecting your organization’s network infrastructure and data from evolving threats.
By following the guidelines outlined above and adapting them to your specific environment, you can establish robust security measures and mitigate potential vulnerabilities.
Remember, network security is an ongoing process, requiring regular assessments, updates, and a proactive approach.
You can Download Perimeter81 Network Security Checklist 2024 for Free Here.



