Xiid SealedTunnel: Unfazed by Yet Another Critical Firewall Vulnerability (CVE-2024-3400)
In the wake of the recent disclosure of a critical vulnerability (CVE-2024-3400) affecting a leading firewall solution, Xiid Corporation reminds organizations that Xiid SealedTunnel customers remain secure. This latest vulnerability, currently unpatched and rated...
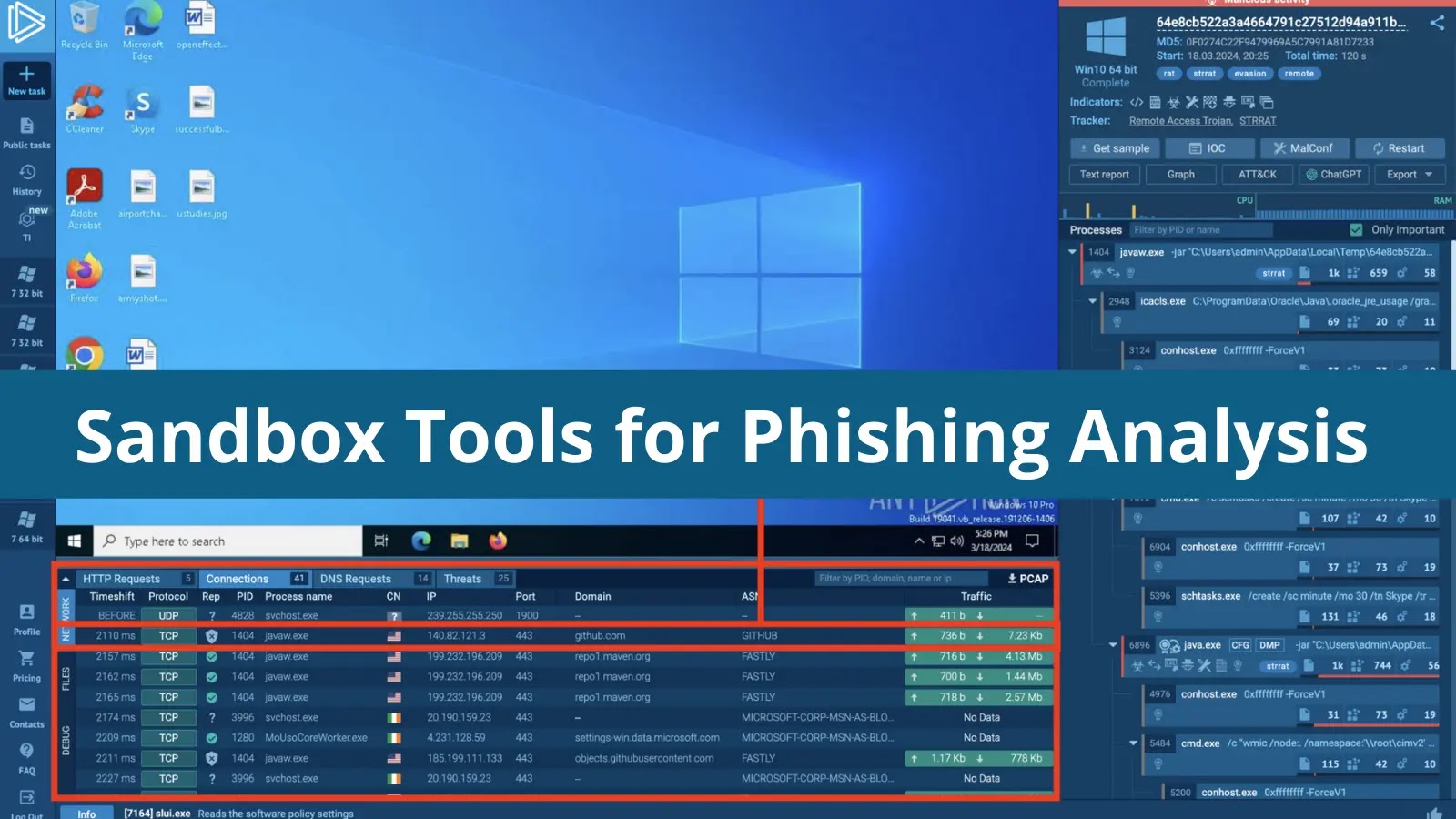
5 Sandbox Tools for Phishing Analysis in 2024
There is a wide variety of solutions one can use to investigate phishing attacks. Yet, in most cases, analysts can do with just one, a malware analysis sandbox. Thanks to its combination of static...
Tor Browser 13.0 Released: What’s New
Tor Browser 13.0.14 has been released, bringing essential security updates to the popular privacy-focused web browser.
This latest version includes updates to the underlying Firefox browser and several bug fixes and improvements.
Critical Updates in Tor...
“Mobile NotPetya”!! Surge in Zero-click Vulnerabilities, Conditions Favour
The cybersecurity community is sounding the alarm about the growing risk of a "mobile NotPetya" event - a self-propagating mobile malware outbreak that could have devastating consequences.
Over the past year, the alarming increase...
LeakyCLI: New Vulnerability Exposes Credentials In AWS, Azure & Google Cloud
Multiple Cloud Service providers like Google Cloud, AWS, and Azure have been discovered with a new vulnerability that has been termed "LeakyCLI."
As the name suggests, the Command line interfaces of Google Cloud (Gcloud CLI),...
How Secure Is Your Active Directory? 5 Critical Vulnerabilities to Watch Out For
Microsoft’s Active Directory (AD) serves as the central nervous system for your organization’s network. It guards company resources by ensuring that only authorized users have access to any given network and database sections.
A well-designed...
Alert! Oracle Releases Critical Patch Update 2024 – 372 Vulnerabilities are Fixed
Oracle has released its Critical Patch Update (CPU) for April 2024, addressing 372 vulnerabilities across multiple products.
The Critical Patch Update provides fixes for security flaws in widely-used Oracle products including Database Server, Fusion...
Hackers Exploiting TP-Link Archer Command Injection Vulnerability in the Wild
Cybersecurity researchers have uncovered widespread exploitation of a critical vulnerability in TP-Link Archer routers, which has led to the proliferation of botnet threats.
The vulnerability, CVE-2023-1389, allows attackers to execute arbitrary commands on affected devices,...
Critical PHP Vulnerabilities Let Attackers Inject Commands : Patch Now
Multiple vulnerabilities have been identified in PHP that are associated with Command Injection, Cookie Bypass, Account takeover, and Denial of Service.
The CVEs for these vulnerabilities have been given as CVE-2024-1874, CVE-2024-2756, CVE-2024-3096, and CVE-2024-2757....
NSA, CISA Released Guidance And Best Practices To Secure The AI
In an era where artificial intelligence (AI) systems are becoming increasingly integral to our daily lives, the National Security Agency’s Artificial Intelligence Security Center (NSA AISC) has taken a significant step forward in enhancing...



.webp)
.webp)



.webp)



