Metasploit provides a complete framework for building, testing, and carrying out attacks against sensitive systems, making it a must-have tool for any organization.
Rapid7’s Metasploit is a valuable penetration testing tool that is being used for detecting and exploiting vulnerabilities on target systems.
This article helps you understand the Metasploit program and its potential, regardless of whether you’ve been a beginner or an experienced professional.
Go ahead and walk with us into the world of Metasploit.
Table of Contents
- What is Metasploit?
- History
- Is Metasploit Written in Ruby?
- What database does Metasploit use?
- Is Metasploit a tool or framework?
- How many modules are there in Metasploit?
- What is a Metasploit used for?
- What are the tools of Metasploit?
- Does Metasploit use SSH?
- Benefits & Limitations
- Does Metasploit work without the Internet?
- Conclusion
What is Metasploit?
Metasploit is an Open Source Penetration Testing Framework created by Rapid7 that enables security professionals to simulate attacks against computer systems, networks, and applications.
It provides a range of tools and modules which can be utilized to check the security of the target system, identify vulnerabilities, and use them to get into the system.
Users can adjust their experiments to a certain environment or set of goals, expressing flexibility and adaptability.
Within this framework are several predefined vulnerabilities and payloads and the option to create unique exploits or programs.
Additionally, this tool includes a user-friendly interface that makes it possible to organize and carry out the testing even for people with little expertise doing penetration tests.
The tool performs various tasks, such as reconnaissance, exploitation, and scans.

Additionally included is a programming language that enables attackers to design their own unique attacks as well as a vulnerability database and exploits that can be used to find issues with the target system.
Security experts, ethical hackers, and businesses of all sizes test their systems for vulnerabilities with Metasploit so that they may be found before hostile actors exploit them.
This program is updated and maintained by the large developer community, assuring that it will remain a crucial tool in the long run.
History of Metasploit
- 2003, H. D. Moore, a security researcher at the time, came up with Metasploit.
- Moore established Metasploit L.L.C. in 2007 to provide services and marketing assistance.
- Rapid7 acquired the firm in 2009 and developed and executed the framework.
It occurred to Moore that there was no effective way of testing the security of computers and networks, so he created his own tool in order to meet this need.
Metasploit’s original version was a basic Perl script meant for the automated exploitation of vulnerabilities in target systems.
This script has been rewritten in Ruby, making the platform more appropriate and user-friendly for future growth.
The tool has evolved into one of the best-known and most used technologies for cyber security in recent years.
It is popular with security professionals and ethical hackers for its flexible architecture, comprehensive toolkit, and user-friendly interface.
The framework is always growing, with new exploits, payloads, and modules being released regularly.
The user and developer community contributing to its development and maintenance is likewise substantial and active.
Rapid7 produces commercial versions of the program, including Metasploit Pro, Express, and the open-source Metasploit Framework, which provide extra capabilities and support for business use cases.
Is Metasploit Written in Ruby?
Yes, Metasploit is written in the Ruby programming language. At the core of the Metasploit engine, the framework is an open-source project primarily written in Ruby.
The Metasploit Framework is available for download from the rapid7 website and provides a comprehensive set of tools for developing and performing exploits against vulnerable systems.
Ruby is a dynamic object-oriented programming language first published in 1995 by Yukihiro “Matz” Matsumoto.
It is a popular language for developing web applications, and its popularity has increased in recent years due to the development of the Ruby on Rails web framework.
One of the main advantages of using Ruby for Metasploit development is its flexibility and ease of use. Ruby is known for its readability and concise syntax, making writing and maintaining code easily.
Additionally, Ruby emphasizes developer productivity, providing features like garbage collection and dynamic typing that can help developers be more productive.
The usage of Ruby in Metasploit also makes it simple to modify and customize the program.
The Metasploit Framework has a rich API that lets developers design custom modules and plugins for use with the tool.
This has resulted in a thriving developer community contributing to the project by producing new modules and plugins, extending the tool’s capability.
Overall, Ruby’s adoption is critical to the success of the Metasploit project.
Its flexibility, ease of use, and strong development community have made it a popular tool for security professionals and ethical hackers looking to discover and exploit vulnerabilities in target systems.
What Database Does Metasploit Use?
The information about targets, exploits, and more concerning the security testing process is stored in a PostgreSQL database by Metasploit.
PostgreSQL is a relational database management system widely regarded as robust, reliable, and able to support more sophisticated features such as triggers, storage instances, or foreign keys.
Metasploit allows security experts, ethical hackers, and organizations of all sizes to evaluate their systems’ security for potential flaws before a bad actor exploits them.
It is constantly updated and maintained by a vast developer community, making it one of the most vital tools for the foreseeable future.
To follow the development of information after a certain period, it is essential to use the data set to store information on security reviews.
The PostgreSQL data set gives a reliable and versatile choice for this motivation and a well-known decision for associations to use Metasploit to perform security tests.
Is Metasploit a Tool or Framework?
Metasploit is a framework as well as a tool. The application has an easy-to-use interface that allows even people with modest penetration testing skills to organize and perform tests.
At its heart, it is a penetration testing tool that offers a predefined collection of exploits, payloads, and assistance modules that may be used to test the target system’s security.
The framework also enables the development of these bespoke exploits, payloads, and modules.
The framework offers developers a collection of APIs and libraries for creating modules that can be incorporated into Metasploit’s basic functionalities.
This implies that the tool may be customized for unique scenarios and goals while also staying up to speed on emerging risks and weaknesses.
As a result, rather than being primarily recognized as a tool, Metasploit is more correctly referred to as a framework that provides built-in capabilities and the flexibility to expand and customize these features as needed.
How Many Modules are there in Metasploit?
Metasploit is an integrated testing framework comprising a range of modules that can be exploited in various tasks relating to penetration testing and exploitation.
In Metasploit, more than 4800 modules are available. These modules shall include various exploits, payloads, backsets, and post-exploitation modules.
As the Metasploit framework continues to evolve and new modules are added regularly, the number of existing modules will continue to increase.
What is a Metasploit Used for?
The primary objective of Metasploit is to enable users to identify, exploit and fix vulnerabilities in the target system.
The framework contains many precompiled exploits, helper payloads, and modules that can be used for simulating attacks and testing systems and application security.
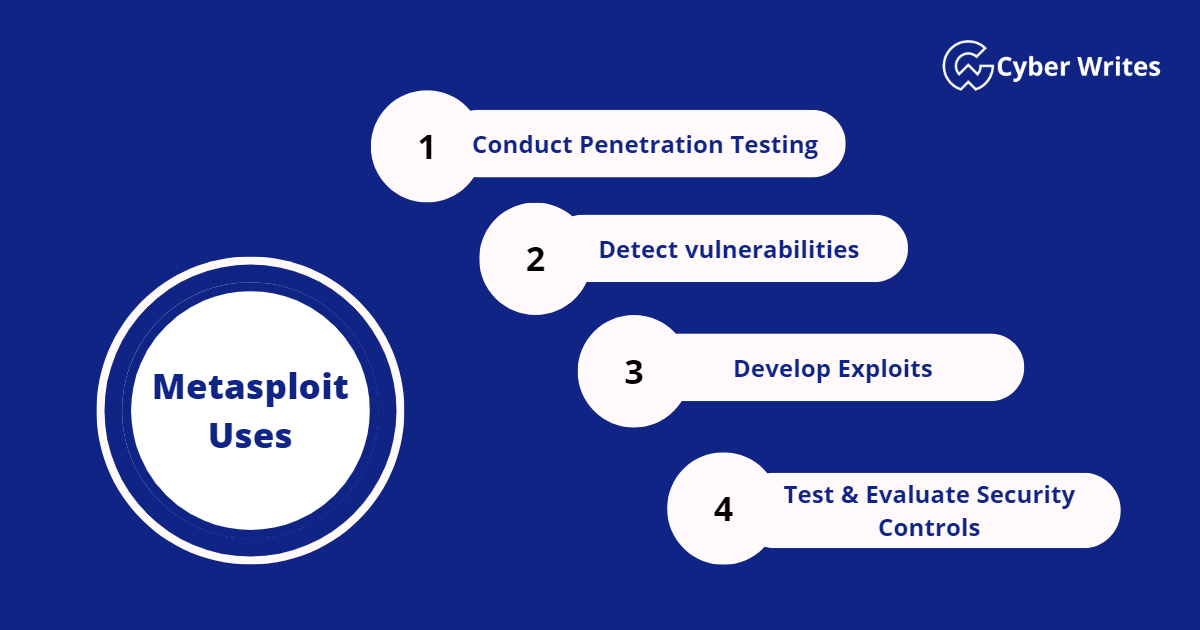
Metasploit is widely used by security professionals, penetration testers, and ethical hackers to:
Conduct Penetration Testing
- Penetration testing is a way to evaluate system security by simulating attacks and trying to take advantage of weaknesses.
- A complete set of tools and modules to carry out penetration tests on a wide variety of systems and applications is available from Metasploit.
Detect vulnerabilities
- For the detection of vulnerabilities in target systems and applications, Metasploit can be used.
- The framework contains an extensive library of preconfigured and guided exploit modules that can scan the network, fingerprint systems, and gather information on potential vulnerabilities.
Develop Exploits
- You can create custom exploits with the Metasploit tool designed to exploit certain vulnerabilities.
- The framework provides users with a powerful scripting language that allows them to build and connect their exploits; they can use an extension API.
Test & Evaluate Security Controls
- The efficacy of several security systems, such as firewalls, intrusion detection systems, and antivirus software, can be evaluated using Metasploit.
- Several instruments and modules are part of the framework for testing the effectiveness of safety policies and identifying vulnerabilities that can be exploited.
In addition to the normal functionality, Metasploit offers users a range of additional capabilities, such as reporting and collaboration tools that enable them to share results, be able to follow their progress, or work on test projects experience.
In general, Metasploit is a strong and flexible architecture that consists of an extensive set of tools and modules to conduct penetration testing, vulnerability assessments, and the exploitation of buildings.
What are the Tools of Metasploit?
Metasploit is a modular exploitation framework that provides a wide range of tools and modules for penetration testing, vulnerability assessment, and exploit development.
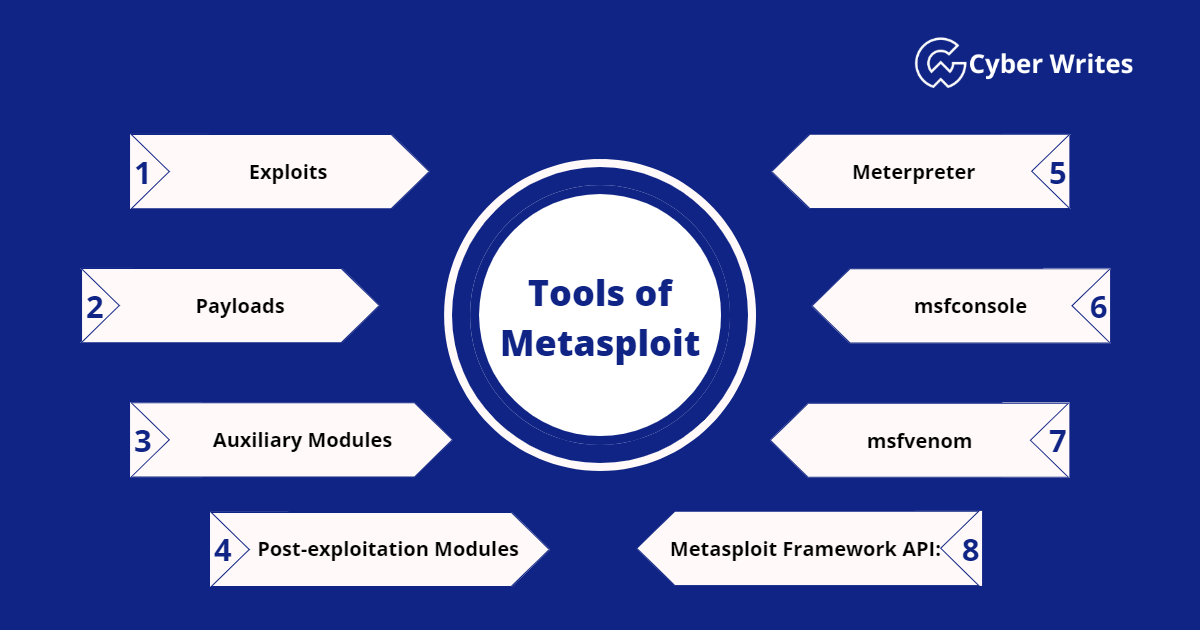
Some of the key tools and modules available in Metasploit include:
Exploits
- The Metasploit tool provides an enormous library of exploits for each operating system, application, and network device.
- This exploit can be used to identify vulnerabilities in the target system and obtain unauthorized access.
Payloads
- Metasploit is full of different payloads that can be carried out on the target system after successful exploitation.
- These payloads can be used to gain remote access, upload or download files, and carry out surveys.
Auxiliary Modules
- Metasploit includes several helper modules that perform non-exploitation tasks, including Scanning, Fingerprinting, and Information Gathering.
Post-exploitation Modules
- Metasploit contains a range of post-exploitation modules that operate on your target system after an exploit has been successfully performed.
- Tasks such as escalation of privileges, lateral movement, or data erasure can be performed with these modules.
Meterpreter
- Meterpreter is a powerful spacecraft capable of deploying an operating command shell on the target system.
- The Meterpreter tool can take control of compromised systems and perform various tasks, such as executing commands, uploading and downloading files, or transferring them from one network system to another.
msfconsole
- The main Metasploit user interface is msfconsole. It makes it possible for users to interact with the framework and run various tools and modules by providing a command line interface.
msfvenom
- msfvenom is a command line tool from the Metasploit framework, which can be used to build various types of payloads for different purposes, such as shellcodes, executables, exploit modules, and so on, in order to access systems remotely or create backdoors.
- It is a powerful tool for the creation of custom payloads in specific exploitation scenarios used by penetration testers and security researchers.
Metasploit Framework API:
- Metasploit provides a comprehensive API for programmatically interacting with the Framework. You may use the API to perform automation tasks, integrate Metasploit with other applications and create your own exploits and modules.
- Overall, there are a number of highly effective and usual tools and modules available to perform penetration testing, vulnerability assessment, and development exploitation at Metasploit.
Does Metasploit use SSH?
Yes, the Metasploit Framework includes modules for exploiting SSH vulnerabilities and for establishing SSH connections to remote systems.
The SSH Secure Shell network protocol is used for secured remote access to the system. It enables the interaction of a secured communication channel between Safe Remote Access and Network Services.
However, vulnerabilities that an attacker would exploit if he could gain unauthorized access are present in SSH servers.
The Metasploit module will allow the exploitation of SSH vulnerabilities, e.g., authentication and vulnerability-dependent attacks.
For example, modules are available to exploit CVE-2010-5107 vulnerabilities in OpenSSH or use weak credentials on an SSH server.
These modules can be used for gaining access to SSH servers, performing code operations, or executing more malicious activities on the target computer.
The framework also offers an SSH login scanner module that may be used to determine authentic SSH server credentials.
This module can assist penetration testers in identifying weak or default credentials in SSH servers and assisting them in improving their security.
Besides its ability to attack SSH vulnerability, Metasploit can also be exploited for the construction of migration tunnels on a hacker’s network.
In other words, an attacker could have used the insecure host as a gateway to gain access to additional systems on the network that were not available.
As a result, Metasploit employs SSH and includes a number of modules for exploiting SSH vulnerabilities and establishing SSH connections.
What are the Benefits of Metasploit?
Metasploit is a powerful open-source framework that provides a wide range of benefits for security professionals, penetration testers, and ethical hackers. Here are some of the key benefits of Metasploit:

Standardized Methodology
- In the field of penetration tests and ethical hacking, Metasploit provides a standardized approach.
- It set out a structure for planning and conducting penetration testing operations, such as vulnerability surveys, network reconnaissance, or the creation of new networks.
- It is thus important to ensure that testing takes place in a coherent and systematic way, which may assist in identifying and mitigating security concerns.
Wide range of exploit modules
- A standardized method for testing breaches and ethical hacking was provided by Metasploit.
- This structure sets up the framework for organizing and carrying out penetration testing activities such as vulnerability assessments, network monitoring, and creation exploitation.
- It will contribute to ensuring that tests are carried out on a regular and systematic basis, making it more efficient in identifying and mitigating security risks.
Ease of use
- The Metasploit user interface, which is simple and understandable for technically proficient users as well as nontechnological users, was designed in order to simplify the application.
- In order to facilitate vulnerability detection and mitigation, this framework shall contain a number of instruments and procedures that can be implemented automatically.
- This will help the penetration test process to be completed more quickly while reducing the possibility of misunderstandings.
Flexibility
- The Metasploit is a very flexible instrument that can be tailored to specific testing conditions.
- It allows users, for use with any other security instrument or framework, the creation of special attack modules, payloads, and post-exploitation scripts.
- This way, security and penetration testing could be set up with ease in a variety of environments and applications.
Collaboration
- The initiative brings together experts in the field of security, as well as Ethical Hacking to collaborate and share knowledge.
- The tools available to users through this framework enable them to exchange information, modules, and search results with other members of the Community.
- The development of the Community’s knowledge base contributes to this and ensures that security testing results become more complete and efficient.
Cost-effective:
- Metasploit is a free and open-source framework, it offers an affordable alternative for security testing and ethical hacking.
- This is especially useful for small and medium-sized organizations that may lack the capacity to invest in costly commercial security products.
In short, the Metasploit platform is robust and comprehensive in terms of security tests as well as ethical hacking.
It offers a number of benefits to experts in the field of security and ethical hackers who are able to identify and mitigate safety risks, improve test methods or work with other members of the community.
Does Metasploit Work Without the Internet?
The Metasploit framework does not rely on an internet connection for the creation and operation of exploits.
When you download and install Metasploit, you can use it on target computers without an Internet connection for the purpose of programming, testing, or launching an exploit.
However, an Internet connection is needed to work effectively on some of the modules.
For instance, if you want to access the most recent definitions of vulnerabilities in a vulnerability database which is available for download from www.NVD.nist.gov, you will need an Internet connection when using this module on vulnerability scanning.
What are the Limitations of Metasploit?
It is a powerful and versatile tool for penetration testing, but like any other tool, it has limitations. Here are some of the limitations of Metasploit:
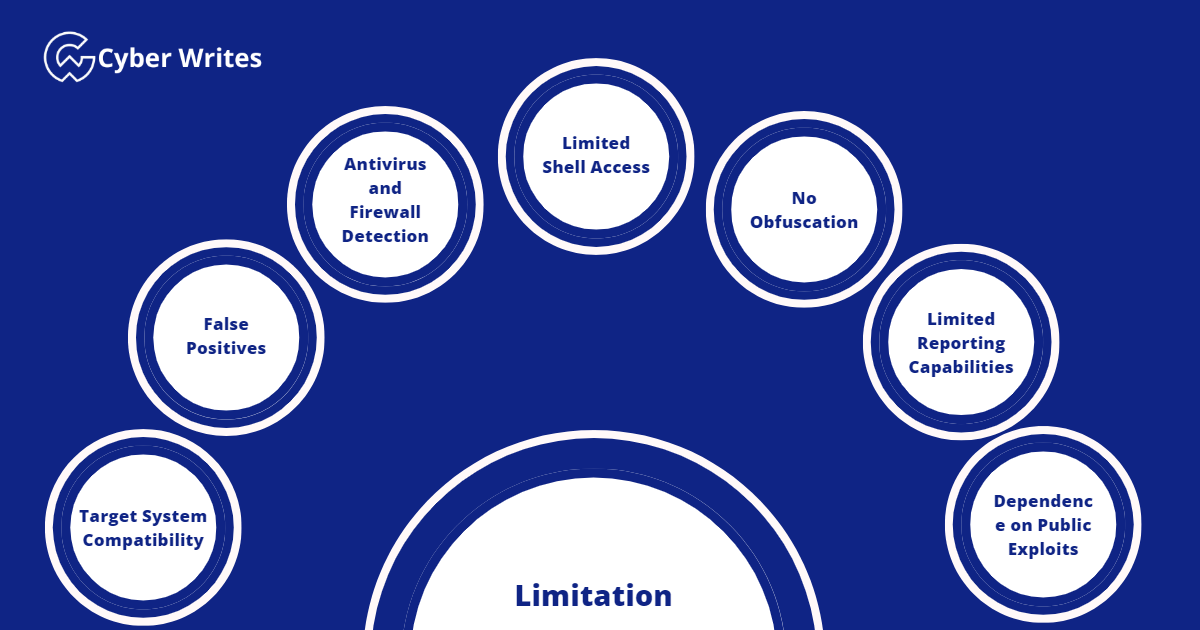
Target System Compatibility
- Metasploit can only be utilized on target systems that support its exploits.
- This implies that if a target machine is patched or has the most recent software version, the Metasploit exploit may fail.
False Positives
- Metasploit’s not perfect, and there might be flaws in it. If Metasploit detects a vulnerability that does not exist in the target system, it will result in false positives.
- If this occurs, it would lead to unnecessary cleanup attempts or a waste of time.
Antivirus and Firewall Detection:
- Security software such as antivirus and firewall may detect and block the exploits of Metasploit.
- It can reduce the efficacy of Metasploit, making it harder for an attack to succeed.
Limited Shell Access:
- You can gain limited shell access to the target system, which is not sufficient for some penetration testing situations.
- For example, you may have to use other tools than Metasploit in order to undertake a large number of remedial actions following exploitation.
No Obfuscation:
- The exploits are not disguised, security software and the administrator of the target system can find them quickly.
- The effectiveness of Metasploit can therefore be reduced and it becomes more difficult to attack successfully.
Limited Reporting Capabilities:
- The reporting capabilities of Metasploit are restricted and may not give the degree of information required for some businesses’ compliance needs.
Dependence on Public Exploits:
- Metasploit relies on publicly available exploits, and there is no guarantee that they will always function. As a result, Metasploit may not discover all vulnerabilities in the target system.
To summarise, while Metasploit is a strong penetration testing tool, it has limits that must be addressed while planning and carrying out penetration testing operations.
Conclusion
In conclusion, it is a versatile and powerful tool for performing penetration testing or vulnerability assessment that is becoming increasingly popular in the cybersecurity industry.
This will provide organizations with an essential tool to assess their security posture by providing a comprehensive framework for forming and executing attacks on vulnerable systems.
We looked at the fundamentals of Metasploit, including its structure, function, and limitations. Metasploit is a very powerful tool, but it has some limitations.
For example, you may not be able to use it on all target machines, and any AV or firewall program can find its exploit.
Metasploit should be managed with other security devices and used with caution to reduce the risk of unintended consequences.
Overall, for any organization wishing to improve its security posture and ward off cyber attacks, Metasploit is an indispensable tool.
In the detection and mitigation of vulnerabilities on networks and systems, security professionals may use Metasploit in a successful manner by becoming familiar with its capabilities and limitations.


