One security measure that can be used to entice attackers is a honeypot, which creates a virtual trap. An attacker can take advantage of the system’s weaknesses since it is purposefully vulnerable.
You need to put in the time and effort to enhance your security policies. Software, file servers, routers, and other resource-intensive systems can be tested in a honeypot environment.
It is also one type of deception technology that will make you understand the behavioral pattern of the attacker. Usually, that security team uses the honeypots to investigate the cybersecurity breaches and how they collect intel for cybercriminals operations. By doing this operation, you can reduce the risk of false things compared with the cybersecurity measures.
Honeypot mainly depends on the deployment and design. Everything looks vulnerable and legitimate to attract cyber criminals.
Table of Contents:
FAQ
Type of Honeypot Deployment:
What are Honeypots Used for?
Spam Trap: An Email Honeypot:
Benefits of Honeypots:
Honeynet
Final thoughts
FAQ
1.What is a honeypot in network security?
A network security honeypot is a fake system or server that attracts cyberattackers. Its main goal is to detect, deflect, or research hacking attempts and understand hackers to improve security.
Honeypots replicate genuine systems with valuable data and resources, such as databases or file servers, but are separated and monitored.
Since honeypots should not draw legitimate traffic, any interaction with one is suspicious. This lets security teams study intrusion strategies, find weaknesses, and improve network security without risking resources.
2.Why is a honeynet useful?
Honeynets provide controlled research of attacker behavior and tactics in an advanced and interactive environment. Cybercriminals find honeynets more appealing than single honeypots because they have a network of decoy systems.
Security professionals can better understand attack patterns, methods, and lateral movement in a network due to its complexity.
Honeynets acquire intelligence by capturing a wider spectrum of threats, from automated worms to sophisticated targeted attacks, by closely emulating a genuine network’s design.
This intelligence aids proactive security and research by improving attack detection and prevention, cybersecurity threat understanding, and security policy and technology development.
3.What is the role of a proxy?
A proxy connects a person to the internet, adding security and functionality. Users that connect to the internet through a proxy server send their requests to the proxy, which relays them to the web server.
Web server replies are sent to the proxy and subsequently the user. This process anonymizes the user’s IP address, improves privacy, filters and monitors internet traffic for security, blocks malicious sites and inappropriate content, and caches web pages to speed up frequently accessed resources and reduce bandwidth usage.
Proxy servers manage, secure, and optimize internet connections for individuals and corporations by acting as gateways.
Type of Honeypot Deployment:
There are a total of three types of honeypot deployment available. Those are discussed below:
- Pure honeypots: This takes care of a complete production system that gets an attack through bug taps then it will get connected with the honeypot. They are very unsophisticated.
- Low-interaction honeypots: They imitate the service and system, which mainly attracts criminal attention. That time Honeypot will collect the data from blind attackers like worms, malware, botnets, etc.
- High-interaction honeypots: This is a very complex setup that looks like the real production of infrastructure. They do not restrict the activity level, which provides extensive cybersecurity. Honeypot also has higher maintenance and expertise in additional technology, including virtual machines. This ensures that the attacker will not be able to access the real system.
What are Honeypots Used for?
Any network can benefit from using honeypots, which record data from unwanted users who are misled into thinking they are a legitimate component of the network.
These traps are rarely used by security teams as part of their network defense strategy. You may also use a honeypot to study how cyberattacks behave when interacting with a network.

Spam trap helps the honeypot where they can do the setup so that email addresses can attract spam web traffic. Usually, spam traps are used for Project Honey Pot, which is embedded in the website software.
They need information related to the spammers, including IP addresses, email addresses, and other site addresses. It does not get used for the security measures that everybody can use for network reconnaissance, even hackers.
Spam Trap: An Email Honeypot:
As we have already mentioned the spam trap is a fraud management tool that helps by providing internet service providers. This also helps to identify and block the spammers. They will make user inboxes safe by blocking vulnerabilities.
A spam trap can make a fake email address that gets used by the bait spammers. There are few legitimate emails sent to the fake address so when you receive the mail it will go to spam.
Here you will get different types of spam traps, which are discussed below:
- Username typos: The spam filter detects typos error that can be done by machine or the human but it will come in the spam folder. Most of the time, the misspelled will be an email address.
- Expired email accounts: Few providers can use abandoned email accounts, which will expire in the domain name, which can be the same as spam traps.
- Purchase email lists: They contain many invalid email addresses, which can trigger a spam trap. Since the sender does not get the authorization to send the email, they get treated in the spammer’s list and get backlisted.
Benefits of Honeypots:
Just placing a honeypot on your network will not complete your needs; there are other security controls available such as intrusion detection systems, firewalls, intrusion prevention systems, and much more. Benefits are described below:
- It helps to distract the cybercriminal so that they cannot target the legitimate system. The more time they spend on the honeypot, the less you have to invest in the system to attract them.
- It gives you the best visibility so that attacks can happen quickly. The attacker does the keystroke to send the instant alerts and the scammer gets an attempt to access the system.
- You can even monitor the attacker’s behavior and detect the vulnerabilities. Another side you need to release the published signature so that you can identify the attack.
- Honeypot will help you to put the organization’s incident response capabilities to the test. You need to prepare your team to take appropriate countermeasures to block that attacker and his access.
- Honeypot also helps to improve your company’s all-over security. It mainly puts the light on the attackers so that you can formulate the correct prevention strategies.
- Honeypot is a very cost-effective method, and it is also a good investment, but it will only interact when malicious activity happens, and it does not require any high-performance resources to control the network traffic for an attack.
- It can capture all types of malicious activity, though attackers use encryption.
- Honeypot collects the data from the attacks which include unauthorized activity, a rich source of useful information, and much more.
Honeynet
This honeynet includes two or more honeypots for one network. When you will have an interconnected network that time honeypot gets used. It allows the organization to track the attacker’s interaction with the resource.
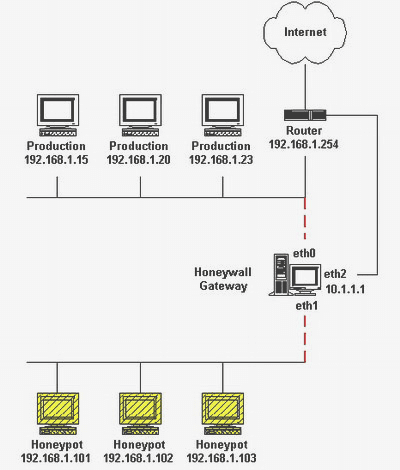
It also helps you monitor intruder moves in the network so that you can interact with multiple points at one time. The main goal is to catch the hacker and successfully breach the network, so if you have more network destinations, it can be more convincing for the attacker.
Deception technology is the more complex implementation for the honeypots as well as a honeynet. It often packages with other technology like next-generation firewalls, Secure web gateways, and IDSes. This technology includes automated features where the honeypot can respond the real time to potential attackers.
Final thoughts
Cyber threats will continue and Honeypot will help the organization to keep the ever-changing threat landscape. Though it is impossible to predict you can prevent every attack with the help of a honeypot.
It always provides useful information and makes sure that the organization can prepare for the reaction to the attacker’s act. This is a good place for the cybersecurity professional to get all hacking-related information.
You can follow us on Linkedin, Twitter, and Facebook for daily Cybersecurity and hacking news updates.
Also Read
What is ICMP Protocol – How does ICMP work, Message Code & ICMP DDoS
What is WarXing in Cyber Security? What are the Benefits?
What Is SOAR and How It Works? Features and Benefits



