Let’s Encrypt to revoke more than 3 million certificates due to a bug in the CAA checking code which fails in checking for the Certificate Authority Authorization (CAA) for the domain.
CAA checks came mandatory on September 8, 2017, it is a way that domain owner whitelist which CA could issue the certificate.
CAA Checking Bug
So if the CAA record is added for the domain, then only the corresponding certificate authority alone can issue the certificate.
Let’s consider this record added for the domain
example.com. IN CAA 0 issue “sectigo.com”
Then only Sectigo alone can issue the certificates for the corresponding, other authorities are stopped from issuing a certificate for the domain.
So to acquire a certificate domain validation needs to completed first and then CAA checks to be done, in some cases Let’s Encrypt check CAA records a second time, just before issuance.
The bug resides in the certificate request, if the request sent for N domain names needed CAA rechecking, then it picks one domain and checks for N times.
“What this means in practice is that if a subscriber validated a domain name at time X, and the CAA records for that domain at time X allowed Let’s Encrypt issuance, that subscriber would be able to issue a certificate containing that domain name until X+30 days, even if someone later installed CAA records on that domain name that prohibit issuance by Let’s Encrypt.”
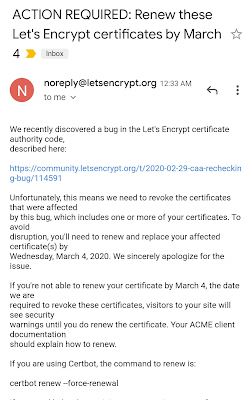
The bug was found by Let’s Encrypt on 2020-02-29 03:08 UTC and the fix deployed on 05:22 UTC. The company plans to revoke Misissued certificates at 2020-03-04 20:00 UTC (3:00 pm US EST).
Let’s Encrypt also sent an Email to users who must renew their certificates by tomorrow before they can become invalid.
To see if your domain affected with the bug, you can use this tool to check for the domain name. You can just enter the domain name to see it is affected or not.






