Firewall as a Service (FWaaS) is an emerging security model in cloud computing and network security. It represents a shift from traditional, on-premise firewall solutions to cloud-based firewall services.
Firewalls as Service Providers (FWaaS) are pillars of enterprise network security.
It keeps an eye on both incoming and outgoing network traffic, allowing or blocking data packets in accordance with its security policies.
Its goal is to create a wall between your internal network and traffic from outside networks, such as the rest of the internet. this prevents malicious traffic, including that of hackers and viruses.
Table of Contents
What is a firewall as a service?
Which services does the firewall provide?
Is the firewall IaaS or PaaS?
10 Best Firewall as a Service Providers
1.Perimeter81 Firewall as a Service
2.Check Point Next Generation Firewalls (NGFWs)
3.Zscaler Internet Access
4.Palo Alto Networks’ Next-Generation Firewall
5.CrowdSec
6.Sophos Firewall
7.FortiGate NGFW
8.ZoneAlarm Free Firewall
9.Cisco Secure Firewall
10.Barracuda CloudGen Firewall
10 Best Firewall as a Service Providers (FWaaS) Features
Frequently Asked Questions
Also Read
What is a Firewall-as-a-service?
Firewall as a Service (FWaaS) moves firewall functionality to the cloud instead of the traditional network perimeter.
By leveraging cloud computing, an organization can reap several financial, network performance, and security benefits.
Firewalls were initially developed to safeguard local company networks, but firewalls had to change as more businesses migrated their data and applications to the cloud.
Firewalls can now be provided as a component of a company’s cloud infrastructure due to “firewall as a service,” or FWaaS.
It has some distinct benefits, like the capacity to scale almost instantly to accommodate a growing network.
Which services does the FWaaS Provides?
The firewall provides the following services:
- Static-packet filtering:It is a firewall with routing capabilities that can filter packets according to the packet’s fields and the rules set up by the administrator.
- Circuit-level firewalls: It serves as a handshaking mechanism for trusted clients, servers, and untrusted hosts.
- Proxy server: System for network security that defends application-layer message filtering.
- Application server: It defends web applications against numerous application layer assaults, including cross-site scripting (XSS), SQL injection, etc.
- NAT: Many firewalls have a feature called network address translation (NAT) that converts between internal and external IP addresses.
- Stateful packet inspection: Dynamic packet filtering chooses which network packets to allow through the firewall while keeping an eye on active connections.
Is the Firewall IaaS or PaaS?
A platform-as-a-service (PaaS) or infrastructure-as-a-service (IaaS) model is used to run virtual firewalls, which are cloud-based services that are created to run in a virtual data center using your own servers.
The firewall application, which runs on virtual servers in these circumstances, protects traffic to, from, and between cloud applications.
IaaS/PaaS allows you to create, provision, and manage your own virtual servers using infrastructure that you rent from a service provider.
The industry sometimes uses the term “next-generation firewalls” to describe any advanced firewall system that runs on-premises or in the cloud, though it is not consistently used in that sense.
How do you Choose the Best Firewall as a Service Providers?
When selecting a Firewall as a Service (FWaaS) provider, it is important to carefully consider various factors to ensure that you find the service that best meets your specific requirements. Here’s a systematic approach to assist you in making a well-informed decision:
Determine Your Security Needs:
- Evaluate the unique security requirements of your organization. Take into account the scale of your network, the variety of devices connected, and the sensitivity of the data you manage.
- Assess the necessary level of security. For example, companies that deal with sensitive data may require stronger security features.
Explore Potential Providers:
- Seek out providers who have established themselves as leaders in the field. Assess their history of dependability and customer contentment.
- Take a look at reviews and case studies to gain insights into how they have successfully assisted other businesses, particularly those that are similar to yours.
Assess the Feature Set:
- Make sure that the FWaaS includes all the necessary features such as intrusion prevention, anti-virus, web filtering, application control, and VPN capabilities.
- Look for advanced features such as AI-driven threat intelligence, sandboxing, and seamless integration with other security tools.
Enhancing Scalability and Flexibility:
- The FWaaS should be easily scalable to handle the expanding needs of your business.
- It should also have the ability to easily adjust to evolving security requirements and advancements in technology.
Ensuring Compliance and Protecting Data Privacy:
- Make sure the provider adheres to the necessary regulations and standards that are relevant to your industry, such as GDPR and HIPAA.
- Gain insight into their approach to data management, including their data center locations and privacy policies.
Ensuring optimal performance and reliability:
- Evaluate the effect of the firewall on the speed and latency of your network.
- Ensure that you seek out assurances of high availability and reliability, typically outlined in the Service Level Agreements (SLAs) provided by the service providers.
Assistance and Customer Care:
- Effective customer support is essential. Please ensure that you verify the accessibility and promptness of the support services.
- Seek out providers that offer extensive training and resources for your team.
Factors to Keep in Mind When Evaluating Costs:
- Examine the pricing models offered by various providers. It’s important to be aware of any additional expenses that may not be immediately apparent.
- Take into account the overall cost of ownership, which encompasses setup, maintenance, and any extra functionalities.
Exploring Trial Periods and Demos:
- Make sure to utilize trial periods or request demos to evaluate the service in your specific setup.
- Take advantage of this chance to assess the user-friendliness and compatibility with your current infrastructure.
Peer Recommendations and References:
- Connect with colleagues in your field to gather suggestions.
- Request customer references or case studies from providers.
10 Best Firewall as a Service Providers (FWaaS) Features
| Firewall as a Service Provider | Key features |
|---|---|
| 1. Perimeter81 Firewall as a Service | 1. The integrated Perimeter81 FWaaS manages every network resource, user, and environment. 2. Because it guarantees that IT has a direct line-of-sight with all corporate data, both at rest and in transit, Perimeter81 Firewall as a Service is noticeable. 3. As it specifies the specific guidelines for when and how traffic is allowed to flow inside your networks, Perimeter81 is granular. 4. As the business expands, Perimeter81 FWaaS just creates, modifies, and applies network traffic policies. 5. The most important resources in your company can be completely monitored and secured from a single dashboard. |
| 2. Check Point Next Generation Firewalls (NGFWs) | 1. Defend against cyberattacks using your branch’s SD-WAN cloud connection. 2. Check Point NGFW has strong security because it offers the best threat prevention possible with SandBlast Zero-Day protection. 3. Since managing and configuring network security environments and policies is made simple by CheckPoint NGFW’s SmartConsole, it has unified management. 4. When users are out of the office or working remotely, give them secure, seamless access to the company’s networks and resources. 5. Remote users can connect without interruption due to CheckPoint NGFW’s remote access VPN. |
| 3. Zscaler Internet Access | 1. enhances the user experience by providing constant, quick, and secure connections across all ports and protocols. 2. To identify and stop specific, targeted threats, create personalized IPS signatures and quickly deploy them using Snort syntax. 3.Using centralized policy management, create flexible access policies for cloud services and PaaS/IaaS. 4. Detect and stop evasive and encrypted cyber threats as soon as they appear in traffic on unusual ports. 5. In addition to maintaining superior performance, localized resolutions protect your users and endpoints from malicious websites and DNS tunneling. |
| 4. Palo Alto Networks Next-Generation Firewall | 1. Your company’s platform is protected, regardless of its complexity or size. 2. To block access to offensive websites, outbound connections can be filtered. 3. For thousands of branch offices, enable Zero Trust Network Security with streamlined security. 4. While analyzing traffic, guard against known vulnerability exploits, malware, spyware, and malicious URLs. 5. A PAN-OS virtual instance running on a VM-Series firewall is prepared for use in a virtualized data center environment. |
| 5. CrowdSec | 1. Check the security of your server, receive notifications of unusual activity, and gather IP address intelligence. 2. Every time an IP is blocked, the entire community is notified so they can all block it as well. 3. CrowdSec adds information, such as the origin country, the autonomous system, and other details, to the data by using resources from outside sources. 4. With a single CLI command, you can connect the Console to your current CrowdSec Agent installations. 5. Determine which IP address and attack method are used to attack your services. |
| 6. Sophos Firewall | 1. Instantly recognizes and isolates infected systems in response to incidents so that they can be cleaned up. 2. With quick and efficient intelligent TLS inspection, a significant blind spot can be removed. 3. You regain control of your networks by having better visibility into risky activity, suspicious traffic, and cutting-edge threats. 4. For all of your Firewalls, Sophos Central offers effective centralized management, reporting, and zero-touch deployment. 5. With options for isolation, bridging, zones, hotspots, channel width, and multiple SSIDs per radio, flexible configuration is possible. |
| 7. FortiGate NGFW | 1. While also adjusting to the threat landscape, it can stop malware and other kinds of attacks. 2. To identify and stop threats, see users, devices, and applications, even when they are encrypted. 3. With fully integrated networking capabilities, such as SD-Branch, SD-WAN, and 5G, you can connect and protect any edge at any scale. 4. With the included FortiGuard IPS, you can get virtual patching and protection from known and zero-day attacks. 5. Improve your environment’s operational efficiency while supporting overworked IT teams. |
| 8. ZoneAlarm Free Firewall | 1. It detects and prevents internet attacks while keeping an eye out for programs that exhibit suspicious behavior. 2. Actively defends against both incoming and outgoing cyberattacks. 3. Provides you with a daily notification of any changes to your credit report, which frequently signify identity theft. 4. Your PC can determine whether it is running a secure operating system or a potentially harmful rootkit with Early Boot Protection. 5. Removes potentially harmful elements from downloaded files, such as macros, embedded objects, and other harmful content, using Zero-Day Protection. |
| 9. Cisco Secure Firewall | 1. For situations where static IP addresses are not available, Cisco’s dynamic attributes support VMware, AWS, and Azure tags. 2. You can easily and consistently manage policies across all of your Cisco Secure firewalls with cloud-based firewall management. 3. By combining the logs from all Cisco Secure Firewalls, you can meet your compliance requirements. 4. Consistent visibility and policy enforcement for dynamic applications across the network. 5. In order to create a highly elastic, cloud-native infrastructure, Secure Firewall Native Cloud is a solution that is developer-friendly. |
| 10. Barracuda CloudGen Firewall | 1. Your security infrastructure’s configuration and maintenance are simplified by the Barracuda Firewall Control Center. 2. You will find all the practical information you need to maintain security with Barracuda Firewall Insights. 3. Your corporate network will be seamlessly connected, and reports and analyses will be compiled. 4. Advanced application-based routing path selection and Quality of Service (QoS) capabilities are provided by the Barracuda CloudGen Firewall. 5. User-defined application definitions can be quickly created using the Barracuda CloudGen Firewall. |
10 Best Firewall as a Service Providers in 2024
- Perimeter81
- Check Point Next Generation Firewalls (NGFWs)
- Zscaler Internet Access
- Palo Alto Networks’ Next-Generation Firewall
- CrowdSec
- Sophos Firewall
- FortiGate NGFW
- ZoneAlarm Free Firewall
- Cisco Secure Firewall
- Barracuda CloudGen Firewall
1. Perimeter81 FWaaS
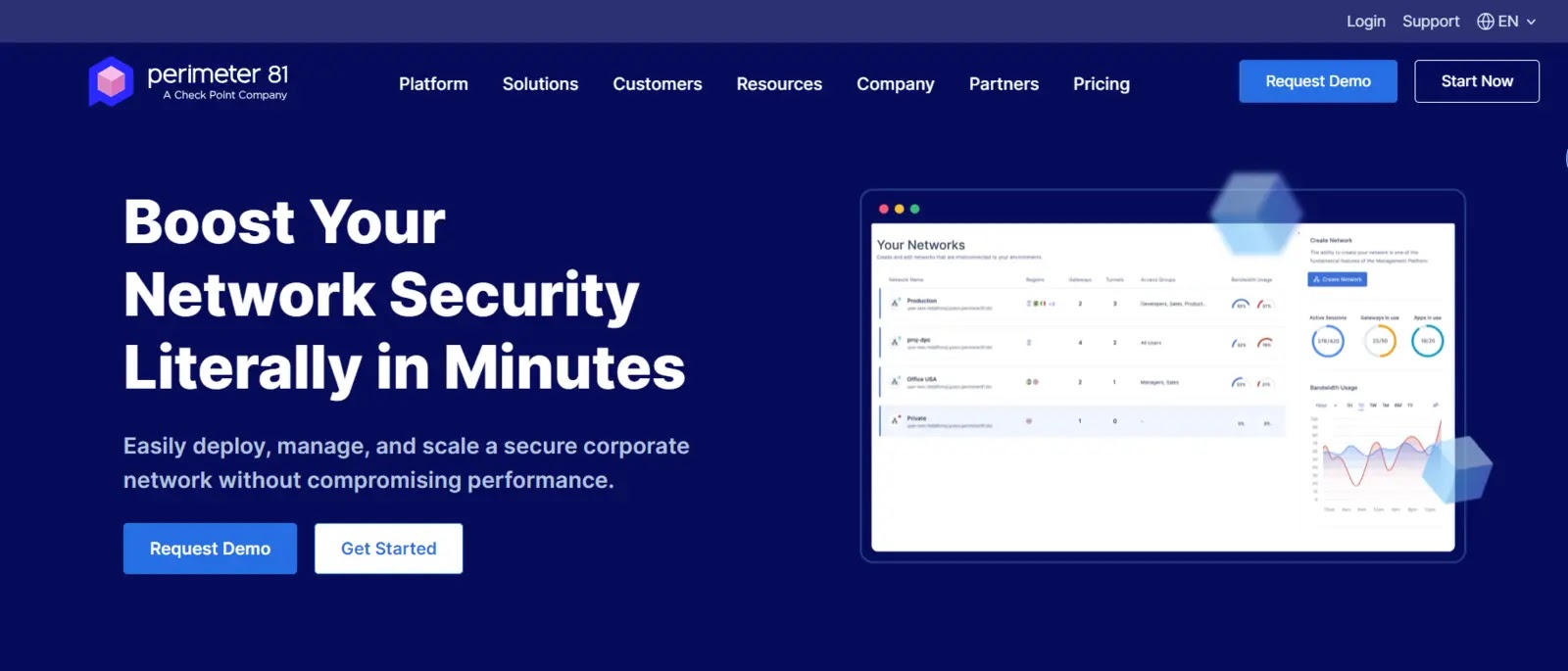
The Perimeter81 security system platform includes the firewall-as-a-service (FWaaS) utility, which comes in a variety of configurations.
Firewall as a Service, offered by Perimeter 81 as part of their Network as a Service platform, allows you to centralize the inspection of network traffic and prevent unauthorized access to your organization’s resources within a single, cloud-based location.
With Perimeter81, a combination of access rights management and connection security, remote workers may safely connect to the cloud without going via your local area network.
Perimeter81 creates a private, encrypted virtual network that incorporates all of your websites and online services.
All incoming and outgoing traffic on your unified network may then be scanned by turning on the firewall as a service.
Perimeter81 tends to focus security protection on individual apps rather than entire systems; the FWaaS will supplement fine-grained fence with system-wide security.
Features
- A central site for setting and managing firewall rules across networks.
- Easily separating and splitting network sections for safety and management.
- Managing networked programs and defining application-level firewall rules.
- Filtering controls incoming and outbound traffic based on predefined rules.
- Bad behavior is monitored and prevented to prevent threats.
| What is Good ? | What Could Be Better ? |
|---|---|
| The Perimeter 81 solution is significantly less expensive than a hardware firewall. | It would be complete with a software-defined network service that uses IP address overlays. |
| It permits the collection of traffic data by logging on to its servers. | There is no native client manual configuration available to Linux users. |
| Detailed control over the services and actions that each user may access. | To give the application a simpler feel, the UI could be updated and improved overall. |
| A service that is simple to use. |
2. Check Point Next Generation Firewalls (NGFWs)

Check Point’s next-generation firewalls (NGFWs) are among the most sensible and straightforward options on the market.
Check Point NGFW, a next-generation firewall, limits access to malicious programs while letting legitimate ones through, ensuring that users can use the internet with peace of mind.
It contains advanced malware prevention features like sandboxing, application and user controls, and integrated intrusion prevention (IPS).
Check Point’s NGFW was designed with 23 unique firewall types to allow for simultaneous operation of many forms of threat prevention. Full SSL inspection is a part of this, and it has no effect on either performance or security.
Check Point’s NGFWs, or Next-Generation Firewalls, focus on improving technologies that stop threats, such as debugging at the CPU level and blocking ransomware.
Moreover, it provides the most advanced and effective protection throughout all portions of the network, safeguarding users from danger no matter where they may be.
Features
- Full security is achieved by inspecting encrypted data to discover concealed risks.
- Segmenting the network makes it safer and easier to maintain.
- Easily configure, monitor, and report on the whole security architecture with a single management console.
- Detail-oriented logging and reporting of network traffic, security incidents, and compliance needs.
- Integration with automation and management platforms to streamline security operations and responses.
| What is Good ? | What Could Be Better ? |
|---|---|
| More secure than any Next Generation Firewall (NGFW). | It is necessary to raise the standard and accessibility of training. |
| Check Point NGFW is ranked fourth among the top solutions. | After each module/blade is enabled, the firewall’s throughput or performance is significantly reduced. |
| The Office VPN is one of the many helpful features. | Sometimes CLI doesn’t display all of the connections. |
| Allows users who are working remotely to connect without any issues. |
3. Zscaler Internet Access
Zscaler Internet Access is the market-leading cloud-native security service edge (SSE) technology, defining what it means to have secure, fast internet and SaaS access.
Zscaler Cloud Firewall provides rapid, secure on- and off-network connections and local internet breakouts for all user traffic without requiring you to manage any hardware or software.
Zscaler Cloud Firewall provides the most comprehensive cloud-native security service edge (SSE) platform available, ensuring that all users, applications, and locations may safely and securely access the internet.
Zscaler Cloud Firewall ensures that you can safely access the internet by managing all types of traffic across all ports and protocols with limitless elasticity and unrivaled performance.
When utilizing the Zscaler service to access the internet, no personally identifiable information is recorded or stored.
Only while connected to the workplace network will your internet traffic be scanned for risks.
Zscaler Cloud Firewall, in conjunction with Zscaler Internet Access and the Zscaler Zero Trust Exchange, provides unparalleled safety and usability.
Features
- Offers a cloud-based firewall to enforce security policies, restrict app access, and block unauthorized network traffic.
- Monitors and restricts network data transmissions to protect private data.
- Administrator-set rules control website and content group access. This enforces rules and blocks hazardous stuff.
- It provides a complete picture of user activity, application use, and security incidents through consolidated dashboards and data.
- employs a network of data centers to give internet customers in different locations the best speed and lowest latency.
| What is Good ? | What Could Be Better ? |
|---|---|
| Infiltrate evasive web traffic on uncommon ports. | Setting up a global organization with split-off locations using separate SD WAN circuits is challenging. |
| Global edge presence protection delivered through the cloud. | If a connection is lost, users should be notified. |
| Without sacrificing performance, secure DNS. | Website access is a little too slow when Zscaler monitoring is enabled. |
| Complete security for users who work from anywhere. |
4. Palo Alto Networks Next-Generation Firewall
.webp)
Palo Alto Networks’ Next-Generation Firewalls (NGFW) use advanced traffic identification, malware prevention, and threat intelligence technologies to give security teams full command and control of all networks.
With CEF integration, Palo Alto Networks firewalls may create logs in the CEF format for traffic, threats, systems, settings, and HIP matches.
They have a unified network security architecture and real-time deep learning in their firewalls, so you can monitor and protect your entire system.
When it comes to vetting people, applications, and content, Palo Alto NGFWs provide enterprises with a wide variety of cutting-edge security tools and methodologies.
By utilizing three distinct identifying technologies—App-ID, User-ID, and content-ID—Palo Alto Networks’ next-generation firewalls allow businesses to monitor and control access to all types of data.
Features
- Allows you to zone the network for better management and security.
- Allows branch offices and remote users to securely connect via VPN.
- A single-pane-of-glass administration console simplifies policy management, monitoring, and security infrastructure reporting.
- Integration with automation and management platforms to streamline security operations and responses.
- Full logging and reporting show network activities, security events, and compliance needs.
| What is Good ? | What Could Be Better ? |
|---|---|
| perfect for your hybrid, public, and private cloud computing environments. | A little more simplicity would help with the Global Protect VPN setup. |
| Secure various public cloud environments with the same level of security as data centers that are located on-site. | Small businesses with limited resources cannot afford it. |
| By establishing decryption policies according to URL category, SSL Inspection was very manageable. | It is challenging to integrate it into an established network. |
| seamlessly integrates with tools and systems from third parties. |
5. CrowdSec
CrowdSec, a free and open-source multi-user firewall, uses IP reputation and IP behavior analysis.
To defend your online services, identify and respond to threats, and block rogue IPs, CrowdSec provides a crowd-based cyber security package called TIP.
Highly curated data on intrusion attempts, sources, and trends is made available to SOC teams and security analysts through the distribution of CrowdSec CTI’s IP reputation intelligence.
Threats, notifications, remediation options, and suspicious IP behavior may all be viewed in a graphical dashboard when the console is linked to CrowdSec Agent.
It monitors system and application logs for suspicious activity and then implements remediation of any type (multi-factor authentication, captchas, or even a simple drop) and at any layer (firewall, reverse proxy, etc.).
It analyzes user actions and provides unique protection from all threats.
Users can use the product for self-defense as well.
Features
- Allows you to zone the network for better management and security.
- Allows branch offices and remote users to securely connect via VPN.
- A single-pane-of-glass administration console simplifies policy management, monitoring, and security infrastructure reporting.
- Integration with automation and management platforms to streamline security operations and responses.
- Full logging and reporting show network activities, security events, and compliance needs.
| What is Good ? | What Could Be Better ? |
|---|---|
| Tool for detecting and resolving cooperative malicious activity. | If it was compatible with different platforms, that would be interesting. |
| It is both open source and free. | Currently, only the Linux operating system is supported; Windows is not. |
| Manage your devices by naming and tagging them. | a few CMS plug-ins are missing. |
| To spot trends and patterns, examine the activity history from the previous months and over time. |
6. Sophos Firewall

Using deep learning and synchronized security, the Sophos XG Firewall offers next-generation firewall protection at a high level.
When it comes to expanding your network’s security and efficiency, the Sophos Firewall ecosystem can provide you with unparalleled benefits.
Accelerating your essential SaaS, SD-WAN, and cloud application traffic while protecting your network from modern threats is what Sophos Firewall’s Xstream architecture is all about.
New SD-WAN features in Sophos Firewall allow for maximum network speed, adaptability, and security.
Sophos Firewall automatically adjusts to your system’s configuration without your having to do anything.
You get all the features, flexibility, and customization options you need to make it work in your setting.
The Sophos XGS Series Firewalls are capable of deep packet inspection thanks to their combination of a high-performance multi-core CPU and a dedicated Xstream Flow Processor.
Features
- Allows you to zone the network for better management and security.
- Allows branch offices and remote users to securely connect via VPN.
- A single-pane-of-glass administration console simplifies policy management, monitoring, and security infrastructure reporting.
- Integration with automation and management platforms to streamline security operations and responses.
- Full logging and reporting show network activities, security events, and compliance needs.
| What is Good ? | What Could Be Better ? |
|---|---|
| Reveals unknown apps and other hidden risks on your network. | If there is any downtime activity, the support team can respond more quickly. |
| Blocks unknown threats using a broad range of cutting-edge security. | Putting 2FA into practice for user authentication at the domain level. |
| Traffic in IPsec tunnels is accelerated by Xstream FastPath. | With OpenVPN, there is no integration. |
| An intuitive interface for configuring rules and VLANs. |
7. FortiGate NGFW

Fortinet, a market leader in secure networking, provides scalable, seamless convergence for any environment, from branch offices and campuses to data centers and the cloud.
The security performance, threat intelligence, full visibility, and secure networking convergence provided by FortiGate NGFW are unmatched.
To avoid user experience degradation and downtime, this firewall system can execute hyper-scale traffic inspections at top speeds.
Secure networking is possible with the help of a wide variety of characteristics, such as software-defined wide area networking (SD-WAN), switching, wireless, and 5G.
FortiGate next-generation firewalls (NGFWs) combine best-in-class security features including intrusion prevention systems (IPS), web filtering, SSL inspection, and automated threat protection to provide safe, policy-driven networking.
Features
- One platform includes firewall, VPN, intrusion prevention, antivirus, application control, and more.
- Managers can set rules based on apps, users, and groups with fine-grained control and visibility over applications.
- Advanced IPS technology that detects and stops known and unknown threats, including zero-day attacks, in real time.
- URL filtering and content management can restrict web browsing and block hazardous or inappropriate websites.
- Stops risks hidden in SSL/TLS encrypted messages by decrypting and checking contents.
| What is Good ? | What Could Be Better ? |
|---|---|
| The user interface is incredibly straightforward and user-friendly. | The Logging Services could be enhanced to provide more information. |
| having the capacity to control from a single automated control console. | Scaling FortiGate is not simple; in order to scale the firewall as the business expands, you must change the hardware box. |
| FortiGate has the benefit of being able to be used on-premises or in the cloud. | Make some features, which are only available in CLI, available in the GUI. |
| The control over applications is extremely strong and constantly updated. |
8. ZoneAlarm Free Firewall
.webp)
ZoneAlarm Free Firewall provides the highest standard of firewall security possible.
ZoneAlarm Free Firewall blocks malicious traffic from entering your home computer and thwarts hackers’ attempts to gain access.
ZoneAlarm Free Firewall delivers many levels of cutting-edge protection to monitor and prevent illegal traffic, protect personal information, and guard against malware and hackers.
This firewall’s Full Stealth Mode makes it possible to remain undetected by intruders and protects against harmful programs.
Your computer is safe from viruses that slow it down and malware that takes your personal data, passwords, and financial information thanks to ZoneAlarm Free Firewall.
With constant DefenseNet security upgrades, it helps you respond rapidly to online attacks.
Features
- Keeps a watch on incoming and outgoing traffic and blocks unauthorized access to your computer and the internet.
- Hides your computer from hazardous traffic by making it appear unavailable to attackers.
- Allows users to authorize or ban internet access for specified programs.
- Updates security rules and standards to prevent new attacks and weaknesses.
- Notifies users of suspicious activity, attempted breaches, and security threats so they may act promptly.
| What is Good ? | What Could Be Better ? |
|---|---|
| Protect your personal information by making yourself untraceable to hackers. | It only supports WindowsOS at the moment. |
| Block unauthorized traffic and manage program internet access. | There is no URL filtering present. |
| With ZoneAlarm Free Firewall, your WiFi PC is protected. | There aren’t many options for scanning. |
| This software offers protection against network threats for desktops and laptops. |
9. Cisco Secure Firewall

The Cisco Secure Firewall was formerly known as Firepower.
Cisco Secure Firewall is the most often used firewall among the best firewalls offered by service providers.
Cisco Secure Firewall is a firewall product that works with Cisco’s other security services and provides comprehensive anti-malware safeguards like DDoS protection and sandbox configurations.
With Cisco Secure Firewall, you can see everything that’s going on inside your network thanks to the powerful security capabilities it integrates, such as Cisco Secure IPS and Cisco Secure Endpoint.
The Cisco Secure Firewall portfolio offers superior protection for your network against today’s sophisticated and ever-evolving threats.
The Cisco Secure Firewall allows for the highest possible level of protection, both now and in the future.
Cisco’s unified platform all easily manages firewall, application, intrusion, URL, and virus security policies.
Any suspicious packets that make it past Cisco Firepower NGFW are reported in detail.
Features
- VPN technology ensures secure remote access for users and branch offices.
- Provides a single control panel for creating policies, monitoring, and providing security system information.
- Uses automation and orchestration to improve security operations, response, and policy enforcement.
- Full logging and reporting show network activities, security events, and compliance needs.
- SD-WAN improves network connections, ensures app functionality, and provides safe internet and cloud access.
| What is Good ? | What Could Be Better ? |
|---|---|
| You can use the firewall locally, remotely, or through the cloud2, which are the three available usage options. | There is no option for CLI configuration changes, and pushing configuration changes is slow. |
| Advanced level malware protection, URL filtering, VPN support, and SSL support are all provided. | Poor reporting engine, rigidity of administration console, and inability to scale product functionality |
| If you’re switching from a more recent ASA or FTD, Cisco provides a migration tool to make the process easier. | Compared to other market rivals, it is a little more expensive. |
| Integrated control across dynamic application environments through real-time, unified workload, and network security |
10. Barracuda CloudGen Firewall

Barracuda’s CloudGen Firewalls redefine the firewall as a distributed network optimization solution that grows to an unlimited number of sites and applications, bridges the gap between on-premises and cloud infrastructures, and facilitates business transformation.
Barracuda firewalls can be deployed on-premises, in Microsoft Azure, Amazon Web Services, or Google Cloud Platform, among other places.
Advanced threat signatures, behavioral and heuristic analysis, static code analysis, and sandboxing are just some of the detection layers available in the Barracuda CloudGen Firewall.
The Barracuda CloudGen Firewall features both on-premises and cloud-deployable SD-WAN capabilities, in addition to supporting connections to geographically distributed sites, different clouds, and mobile users.
Barracuda’s Advanced Threat Protection solution is connected to its global threat intelligence network to provide continuous protection against the latest attacks.
Barracuda gathers threat information from various sources worldwide, including network, email, website, and web browser threats.
Features
- contains basic firewall capabilities and advanced security features like intrusion blocking, program management, URL filtering, and virus & malware protection.
- SD-WAN features improve network performance, reliability, and support many links and connections.
- Searches network data for suspicious activity and hazardous content to block known and unknown threats.
- Gives administrators fine-grained control over apps, users, and content by setting rules for individual apps and user groups.
- Allows partners, remote users, and branch offices to securely connect over VPN.
| What is Good ? | What Could Be Better ? |
|---|---|
| It is user-friendly, simple to use, and makes it simple to unlock captured emails. | falsely blocking users who are not spammers and who are active on trustworthy websites. |
| There are a good number of features for firewall rules pertaining to internal and external networks. | A more user-friendly configuration would make it easier to find specific settings in the menu tree. |
| Flexibility in using tunnels to set up small, remote offices, providing an affordable solution. | Content filtering is not working properly, allowing a lot of unwanted contents. |
| Excellent traffic visibility allows us to monitor real-time traffic applications on the dashboard. |
Frequently Asked Questions
Firewalls are typically your first line of defense against malware, viruses, and attackers trying to access your organization’s internal network and systems, whether they are implemented as hardware, software, or both.
The way they function is another way to classify firewalls, and each type can be configured as either software or a physical device.
1. Packet Filtering Firewalls
The earliest and most fundamental type of firewalls are packet filtering firewalls. Firewalls with packet filtering operate in a line at intersections where switches and routers are used.
2. Circuit-Level Gateways
Circuit-level gateways monitor active sessions and confirm established Transmission Control Protocol (TCP) connections while operating at the session layer. They do not personally inspect the packets.
3. Stateful inspection firewall
State-aware devices not only examine each packet, but also keep track of whether or not it is a part of a TCP or other network session that has already been established.
When it comes to security in the cloud, the cloud provider will manage your solution and the hardware infrastructure that powers it.
Service-based architectures are necessary for many businesses because it allows them to grow as needed without worrying about provisioning new hardware.
Businesses must still provide enterprise firewall capabilities to all users and locations across the organization even as they use cloud infrastructure providers like AWS to increase scalability.
NGFWs go much further, offering extra functionality that makes it possible for a company to detect and thwart attempted cyberattacks more successfully.
With FWaaS, a company can scale security more effectively by connecting its distributed sites and users to a single, logical, global firewall with a unified application-aware security policy.



