Before you know about pretexting, you must understand that it is one type of social engineering attack. Now, are you wondering what social engineering attack is? It mainly accounts for the massive portion of cyberattacks where studies show that the attack always rising. Most of the 90% of hacks start from the social engineering attack.
What is Pretexting?
Pretexting is a social engineering attack in which an attacker tries to convince the victim to give valuable information access to his system. This type of attack is a scam to make the victim fool. In this attacker will attack those person who have the right to access the company’s secret data to get information easily.
Elements of Pretexting
This work as foundation many techniques are involved in it. Here we will discuss the elements; those are below:
- Plausible situation: In this option, you can lead the objective which has been achieved. It is a sequence that helps for event, design, and guide the social engineer to extract the information and manipulate the target. The Pretext is based on initial reconnaissance, which not only points to the viable pretext, but also it provides the necessary information.
- Character: In this situation, the social engineer plays the role of an actor. It is not necessary that you need to impersonate; it is more than a fictitious character. It is very important to know that there are many aspects that get consider while creating the character. A social engineer has to consider how they should be addressed, speaks, and which kind of skill they must set.
Techniques of Pretexting:
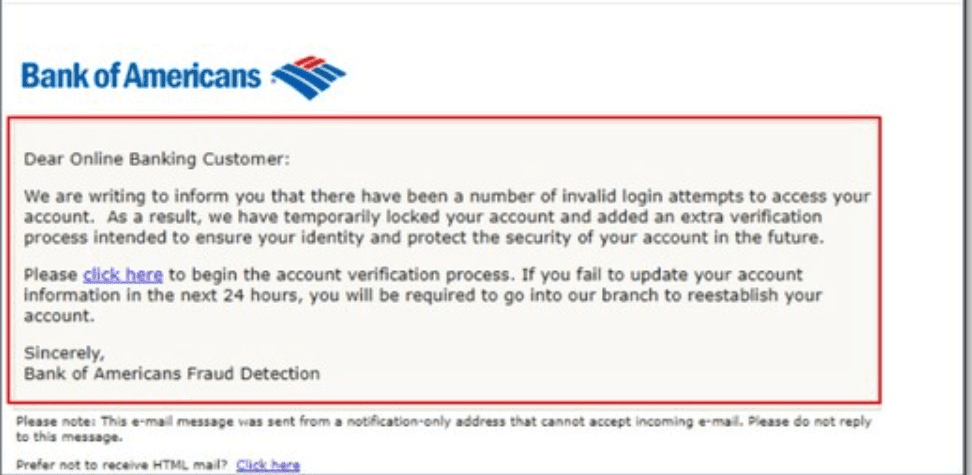
- Phishing: This is another social engineering scam that wants to steal your personal data such as username, password, and banking details. Pretexting’s main work is to build trust with victims by showing them fake emails, phone calls and imitating some authorized personnel. They try to make you fool where they will send you the email indicating that it has come from the bank, and you need to click on that link to get your credential.
- Smishing: It is also similar to phishing where social engineers scam by using SMS text instead of following email and other links. Smishing, name itself, you can understand that it is more effective. In this method, email gets leaked and sold on the dark web. The Maximum time they use phone numbers is more intimate because it creates the connection and trust when you send SMS in the bank.
- Vishing: This is another form of phishing, but it comes with the voice. As this is the social engineer, they will impersonate the regular service how the phishing does. In this you will have the person who will help you link everything with an email to go with the right tone, right question, and right patience. This is a very much effective process for unaware individuals. This is mainly for the older people who do not know to use email and SMS texts.
Examples of Pretexting
- The Attacker would send mail pretending to be from the company’s CEO, by finding the company’s information in directory listings.
- Send an email requesting phone numbers to use as proof of identity and unlock accounts online.
- The Attacker also mimics that they are from any of your company’s third-party service providers by wearing a company shirt or smart card to prove reliability, once they in, they can search for confidential information.
How to Avoid Pretexting Attack:
If you want to prevent pretexting, then you need to follow down safety measures, those are below:
- You need to make sure that every employee makes sure that he wears the employee tag and credential so that it can tailgating thing from the office premises.
- You must always focus on removing ‘teaser’ so that attacker can hunt for your password. To provide the perfect password protection, you need to focus on the latest technology, credential management and other multi-factor authentication.
- You should not click on the unknown links of any email.
- You will also get the constant update from your antivirus software.
- You need to provide every employee, the security awareness training so that they can build the defense against the human error.
- As soon as you receive any call, before doing any action you need to verify the call, email or text properly.
- You always need to verify the call, email, and text to prevent social engineering attacks.
Not only so much you must have a team of ethical hackers who has to be well-trained so that they will get alert before any incident happens. This is not a bad idea where you need to train your IT support team, and they must be certified in ethical hacking certification.
There are few new certifications that cover new technology so that industrial breakthrough becomes vital and becomes tough for the cybersecurity challenge in modern days. If you are looking for ethical hacking certification, then you need to take up the program.
Tailgating Attack:
This is another technique that comes under the pretexting category and this is a very common technique where you need to get through with the locking door where you need to simply follow someone who needs to open before it gets close.
You need to know which type of pretexting you need because the tailgater can put a persona that can encourage the person with the key to built the building.
Like other social engineering techniques, people have the desire to help others; since this software is very friendly and helpful in nature, it has a seemingly good reason where people can confront the tailgater.
Final Thoughts
Pretexting is very important for the business, so every business owner must use it to make it safe.






%20(1)%20(1).webp)