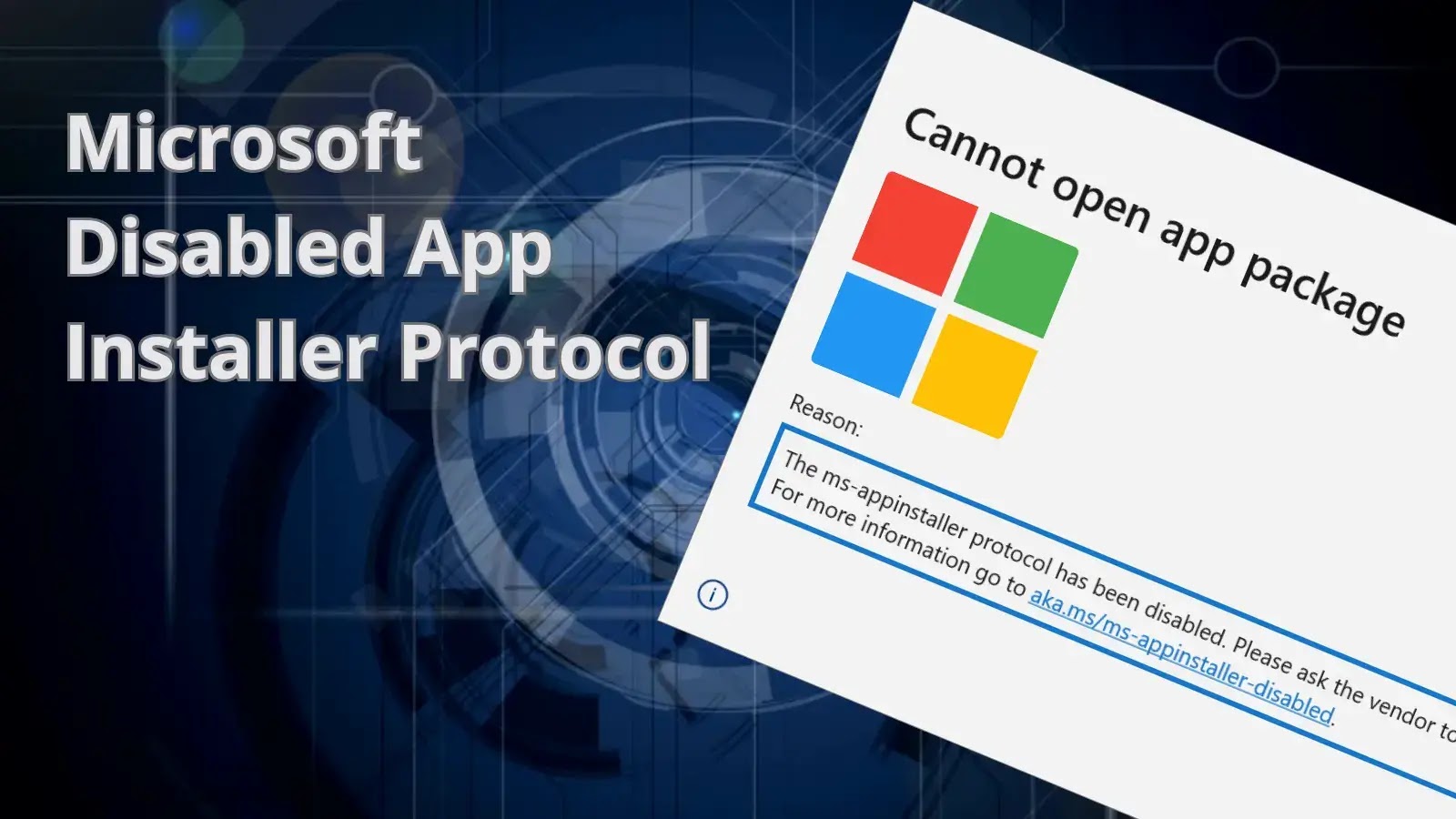
Threat actors, particularly those with financial motivations, have been observed spreading malware via the ms-appinstaller URI scheme (App Installer). As a result of this activity, Microsoft has disabled the ms-appinstaller protocol handler by default.
“The observed threat actor activity abuses the current implementation of the ms-appinstaller protocol handler as an access vector for malware that may lead to ransomware distribution,” the Microsoft Threat Intelligence team said.
The ms-appinstaller protocol handler vector is probably the one that threat actors have selected since it can bypass security measures like Microsoft Defender SmartScreen and built-in browser alerts for downloading executable file types, which are intended to protect users from malware.
Microsoft Threat Intelligence has identified App Installer as a point of entry for human-operated ransomware activities by several actors, including Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674.
Fastrack Compliance: The Path to ZERO-Vulnerability
Compounding the problem are zero-day vulnerabilities like the MOVEit SQLi, Zimbra XSS, and 300+ such vulnerabilities that get discovered each month. Delays in fixing these vulnerabilities lead to compliance issues, these delay can be minimized with a unique feature on AppTrana that helps you to get “Zero vulnerability report” within 72 hours.
Spoofing legitimate applications, tricking users into installing malicious MSIX packages that look like legitimate applications, and avoiding detections on the initial installation files are some of the activities that have been noticed.
Financially Motivated Threat Actors Abusing App Installer
Microsoft discovered that Storm-0569 was using search engine optimization (SEO) poisoning to spread BATLOADER by impersonating websites that offered legitimate downloads, including AnyDesk, Zoom, Tableau, and TeamViewer.
When a user searches on Bing or Google for a legitimate software application, they could see links to malicious installers using the ms-app installer protocol on a landing page that mimics the landing pages of the actual software provider. A prominent social engineering technique involves spoofing and imitating well-known, legitimate software.
Microsoft noticed that Storm-1113’s EugenLoader was distributed using search ads that looked like the Zoom application. A malicious MSIX installer called EugenLoader is downloaded onto a device by the user upon accessing a compromised website, and it is then utilized to distribute other payloads.
These payloads might contain malware installs that have already been seen, like Lumma stealer, Sectop RAT, Gozi, Redline stealer, IcedID, Smoke Loader, and NetSupport Manager (also known as NetSupport RAT).
EugenLoader from Storm-1113, distributed via malicious MSIX package installations, is used by Sangria Tempest. Next, Sangria Tempest distributes Carbanak, a backdoor that the actor has been using since 2014 and which subsequently spreads the Gracewire malware implant.
Financially driven cybercriminals Sangria Tempest (formerly ELBRUS, sometimes tracked as Carbon Spider, FIN7) mostly concentrate on ransomware deployments, such as Clop, or targeted extortion after executing intrusions that frequently result in data theft.
Storm-1674 used Teams to send messages with fake landing pages. The landing pages mimic many businesses as well as Microsoft services like SharePoint and OneDrive. Using the meeting’s chat feature, tenants that the threat actor creates can arrange meetings and communicate with possible victims.
Recommendation
- Develop and implement phishing-resistant user authentication techniques.
- Implement Conditional Access authentication strength to require phishing-resistant authentication.
- Educate Microsoft Teams users to verify ‘External’ tagging on communication attempts from external entities.
- Encourage users to use Microsoft Edge and other web browsers that support Microsoft Defender SmartScreen.
- Configure Microsoft Defender for Office 365 to recheck links on click.
- Turn on attack surface reduction rules to prevent common attack techniques.





.webp)