Researchers discovered several optimizer, utility, booster apps in Google Playstore and download as many as 3,000 malware variants or malicious payloads to perform various malicious activities including ad fraud and other malicious activities.
Malicious apps on Google play are not new, Cybercriminals keep targeting Android users due to over-popularity.
The adware programs will tend to serve unwanted advertisements on your mobile phone and computer. The adware can be included with some apps in a legitimate way to generate revenue.
These apps communicate with the command and control server to download and install the malware and also push malicious ads on the customer’s device.
Malicious Utility Apps
These malicious utility apps that are supposed to speed-up & clean the Android devices found to be downloaded more than 470,000 times.
According to the Trend Micro report, the malicious apps campaign is active since 2017 and more than 3,000 malware variants were detected.
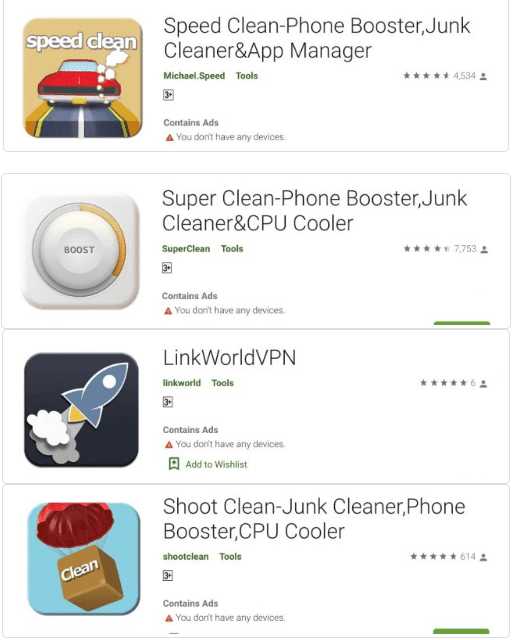
Once the apps get installed, it won’t show the app icons in the launcher and the attackers use the affected devices to post fake reviews and also for clicking the ads pop up.
These apps claim to provide features such as speed clean & VPN to boost the device performance and anonymity, but after installation, they use to pop-up the ads only.
Researchers also observed that malicious apps are capable of launching ” a transparent activity background to hide malicious content from the user.”
Also, these apps once installed on the device connect with a remote server and registers the new malicious device.
These apps are also capable of uses accessibility functions to log in users with other apps by using their Google and Facebook accounts.
The campaign primarily targets the following countries including Japan, Taiwan, the United States, India, and Thailand and Chinese users are excluded.
Here You can find the list of apps, now the apps have been removed from the Google Play.
| App Name | Package | No. of Installs |
| Shoot Clean-Junk Cleaner,Phone Booster,CPU Cooler | com.boost.cpu.shootcleaner | 10,000+ |
| Super Clean Lite- Booster, Clean&CPU Cooler | com.boost.superclean.cpucool.lite | 50,000+ |
| Super Clean-Phone Booster,Junk Cleaner&CPU Cooler | com.booster.supercleaner | 100,000+ |
| Quick Games-H5 Game Center | com.h5games.center.quickgames | 100,000+ |
| Rocket Cleaner | com.party.rocketcleaner | 100,000+ |
| Rocket Cleaner Lite | com.party.rocketcleaner.lite | 10,000+ |
| Speed Clean-Phone Booster,Junk Cleaner&App Manager | com.party.speedclean | 100,000+ |
| LinkWorldVPN | com.linkworld.fast.free.vpn | 1,000+ |
| H5 gamebox | com.games.h5gamebox | 1,000+ |
Indicators of Compromise
SHA256:
1e3f19dcfb23b8e04a88f87c3e4df67eba25b8012f1233295b60355b7545f5d4
1e3f19dcfb23b8e04a88f87c3e4df67eba25b8012f1233295b60355b7545f5d4
c91327f7e48ca64c829c29e6bcb30451dab6c9d32386048165702df3a728c173
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates
Also Read
Faketoken – Android Banking Malware Top-up Infected Mobile Devices to send Offensive SMS Messages





.webp)