Check Point published an advisory regarding a critical vulnerability, CVE-2024-24919, which has since seen a surge in exploitation attempts.
The vulnerability, rated with a CVSS score of 8.6, allows attackers to access sensitive information on the Security Gateway, potentially leading to lateral movement and domain admin privileges.
CVE-2024-24919– The Vulnerability
This vulnerability allows attackers to access files and directories stored outside the web root folder.
The specific exploit involves sending a crafted POST request to the server, which runs as root. This enables the attacker to grab any file on the filesystem.
The exploit, as reverse-engineered by both Check Point and watchTowr labs, looks like this:
POST /clients/MyCRL HTTP/1.1
Host: <redacted>
Content-Length: 39
aCSHELL/../../../../../../../etc/shadowInitial Discovery and Advisory
Check Point’s advisory, although somewhat vague, highlighted the severity of the vulnerability.
Analyze any MaliciousURL, Files & Emails & Configuration With ANY RUN : Start your Analysis
The advisory noted that exploiting this vulnerability could result in accessing sensitive information and potentially lead to domain admin privileges.
It seems that the attacks in the wild had been occurring since April 7, 2024.
Two days after the advisory, on May 30, 2024, watchTowr labs published a detailed write-up, including a working proof of concept.
The Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2024-24919 to its Known Exploited Vulnerabilities list on the same day. By May 31, 2024, exploitation attempts were being observed globally.
Observations and Data
Sift, a cybersecurity monitoring tool, tagged the issue quickly. The first exploit attempt was logged on May 30, 2024, although it was a non-working exploit.
The first successful exploitation attempt was recorded on May 31, 2024, at around 9:30 AM UTC. The payload used in these attempts was identical to the proof of concept published by watchTowr labs.
A manual search of honeypot data revealed that the oldest exploit attempts started on May 30, 2024, at about 5 PM UTC.
These attempts, however, did not work, indicating that attackers were still refining their methods.
The first real exploitation was observed on May 31, 2024, from a New York-based IP address, Grey Noise said.
POST /clients/MyCRL HTTP/1.1
Host: <IP_ADDRESS>
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/<IP_ADDRESS> Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Length: 38
/clients/MyCRL/../../../..//etc/passwd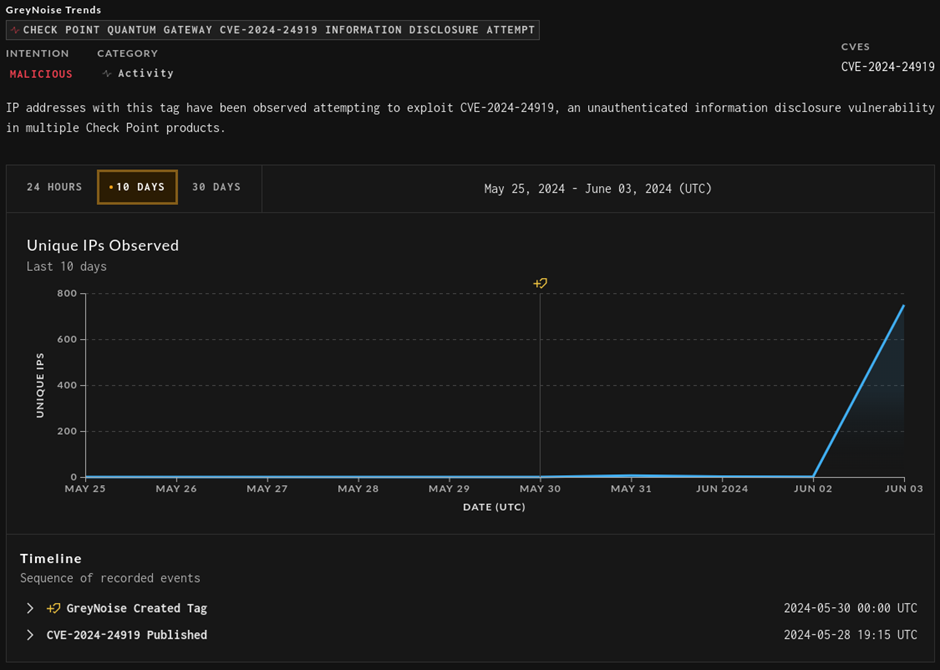
Top Exploited Paths
As of June 4, 2024, the top-10 list of plausibly-working payloads observed includes:
- ../../../../../../../etc/fstab – 4805 attempts
- ../../../../../../../etc/shadow – 2453 attempts
- ../../../../../../../sysimg/CPwrapper/SU/Products.conf – 980 attempts
- ../../../../../../../config/db/initial – 959 attempts
- ../../../../../../../etc/passwd – 508 attempts
- ../../../../../../../home/*/.ssh/authorized_keys – 202 attempts
- ../../../../../../../opt/checkpoint/conf/ – 166 attempts
- ../../../../../../../etc/ssh/sshd_config – 165 attempts
- ../../../../../../../etc/vpn/vpn.conf – 163 attempts
- ../../../../../../../home/*/.ssh/id_rsa – 161 attempts
The rapid increase in exploitation attempts following the public disclosure of CVE-2024-24919 underscores the critical need for organizations to patch their systems promptly.
With a public proof of concept available and exploitation ramping up, all affected entities must apply the necessary patches to mitigate this severe vulnerability.
Looking for Full Data Breach Protection? Try Cynet's All-in-One Cybersecurity Platform for MSPs: Try Free Demo


.webp)


