A highly sophisticated phishing attack exploiting vulnerabilities in Google’s OAuth system has been identified.
The attack, which successfully bypasses Gmail’s security filters, appears legitimate to users as it originates from authentic Google domains and passes all standard security checks, including DKIM authentication.
Attack Leverages OAuth Vulnerability
Nick Johnson, Ethereum Name Service (ENS) developer, reported being targeted by an attack that exploited a flaw in Google’s infrastructure, allowing threat actors to send emails that appear to come directly from Google’s official domains.
“Recently I was targeted by an extremely sophisticated phishing attack, and I want to highlight it here. It exploits a vulnerability in Google’s infrastructure, and given their refusal to fix it, we’re likely to see it a lot more,” Johnson wrote on X.
This attack’s technical sophistication lies in its clever manipulation of Google’s DKIM (DomainKeys Identified Mail) authentication system through what security experts call a “DKIM replay attack.”
Unlike conventional phishing attempts that rely on fake login pages, this attack leverages legitimate OAuth authorization flows.
The attack follows a precise sequence of technical steps:
- Attackers register a domain and create a Google account with the username “me@domain.”
- They create a Google OAuth application with the entire phishing message embedded in the app’s name.
- After granting the app access to their email address, Google automatically sends a security alert to the attacker’s inbox.
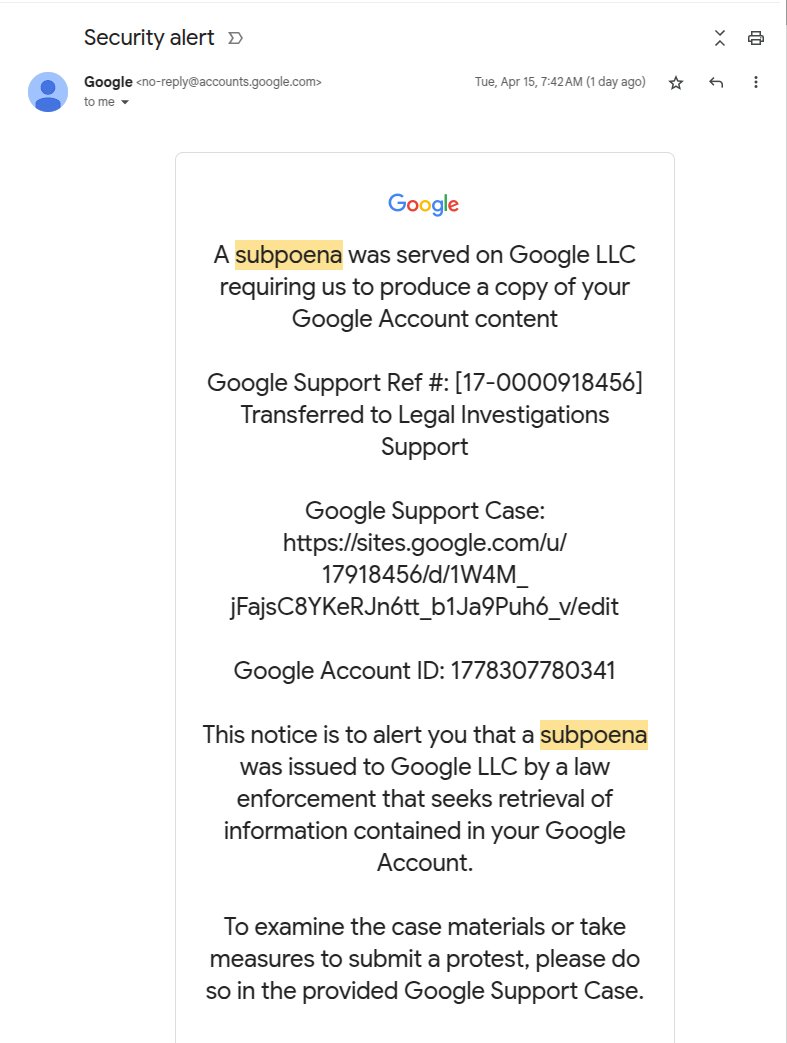
This alert, genuinely signed with Google’s DKIM key, is forwarded to potential victims. The message comes from “no-reply@google[.]com” and passes all standard security checks, including DKIM verification.
The fraudulent message contained a link to a seemingly legitimate Google support page hosted on sites.google.com, further increasing its credibility.
In Johnson’s case, the phishing email claimed that a subpoena had been served on Google LLC requiring the production of his Google Account content, complete with an official-looking case reference number.
Researchers noted that the embedded link in the email pointed to a phishing page under the ‘google.com’ subdomain, guiding users to enter a simulated login interface to steal credentials.
Google Acknowledges the Threat
Google has confirmed awareness of this phishing campaign and acknowledged that it exploits OAuth and DKIM mechanisms in a creative way.
The company stated it is implementing measures to counter this specific threat and expects to have a solution “fully deployed” soon.
“Google has reconsidered and will be fixing the OAuth bug!” Johnson confirmed in a recent update.
In the meantime, security experts recommend users enable two-factor authentication, use passkeys where available, and remain vigilant about any emails requesting account verification or login credentials, even if they appear to come from legitimate sources.
This attack represents a concerning evolution in phishing techniques, moving beyond traditional credential harvesting to more sophisticated exploitation of trusted authorization protocols like OAuth 2.0.
Malware Trends Report Based on 15000 SOC Teams Incidents, Q1 2025 out!-> Get Your Free Copy



.png
)

