A hacking group has evolved with a new ransomware variant known as GhostLocker 2.0.
This group, in collaboration with the Stormous ransomware operators, has initiated double extortion ransomware attacks targeting various businesses globally.
The joint efforts of GhostSec and Stormous have led to the creation of a new ransomware-as-a-service program named STMX_GhostLocker, offering diverse options for their affiliates.
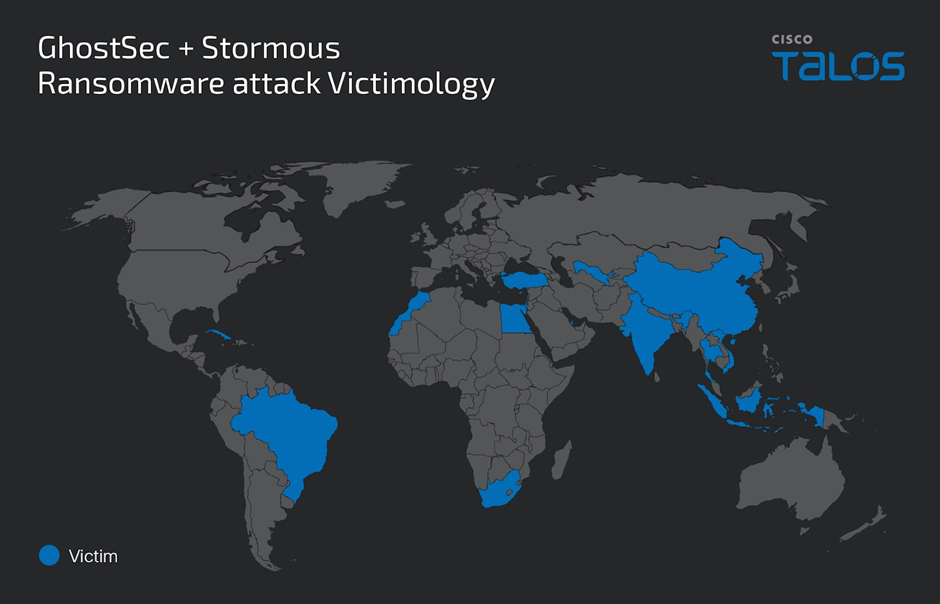
Global Impact of Ransomware Attacks
The victimology of these attacks spans across multiple countries, including Cuba, Argentina, Poland, China, and many others.
Are you from SOC and DFIR teams? – Join With 400,000 independent Researchers
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data If you want to test all these features now with completely free access to the sandbox: ..
These cybercriminal activities have affected victims in different business sectors, as disclosed by the groups in their Telegram channels.
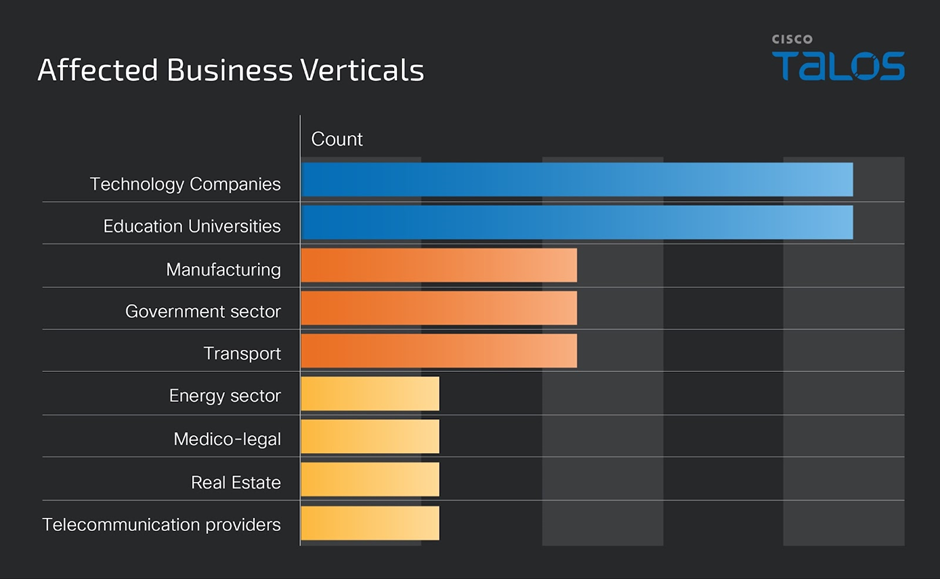
Notably, GhostSec has been actively targeting Israel’s industrial systems and critical infrastructure, with reported attacks on organizations like the Ministry of Defense in Israel.
Using the GhostLocker and StormousX ransomware malware, Talos discovered that the GhostSec and Stormous gangs were collaborating on several double extortion assaults.
Evolution of GhostLocker Ransomware
GhostSec introduced an upgraded version of their ransomware called GhostLocker 2.0, showcasing continuous development efforts with plans for further iterations like GhostLocker V3.
The ransom note strategy has evolved to include instructions for victims to secure their encryption ID and engage in negotiations within a specified timeframe to prevent data disclosure.
The ransomware’s capabilities include encryption of files with a “.ghost” extension and communication with a Command and Control (C2) server located in Moscow.
Tools and Techniques Employed
In addition to ransomware attacks, GhostSec has been utilizing tools like the “GhostSec Deep Scan tool” and “GhostPresser” to compromise websites. The Deep Scan toolset enables comprehensive scanning of websites for vulnerabilities and technologies used, while GhostPresser focuses on exploiting WordPress sites through XSS attacks.
These tools demonstrate the group’s sophistication in cyber operations and continuous enhancement of their capabilities.
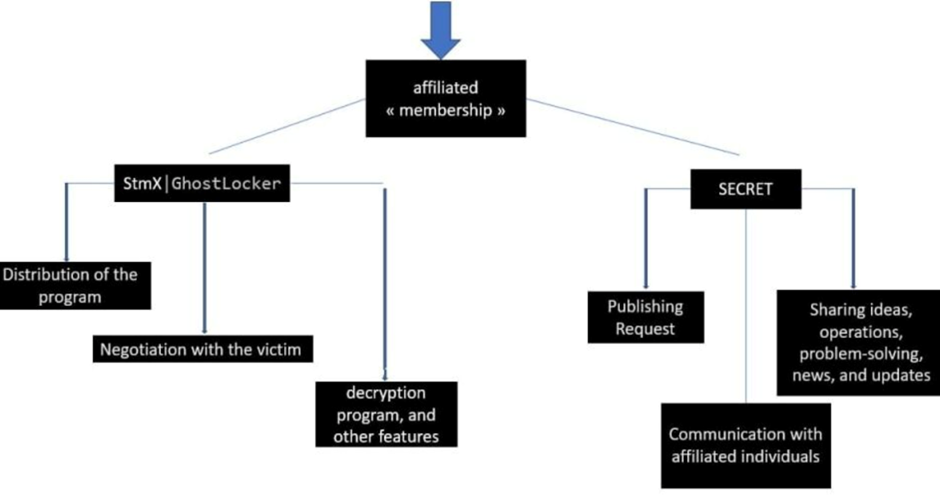
Stormous and GhostSec have jointly launched the STMX_GhostLocker program on the TOR network, providing services for affiliates to join and disclose victim data.
The program offers different categories of services for affiliates, including paid options and features for individuals looking to sell or publish data. The blog dashboard showcases victim counts and disclosed information, with reported ransom amounts reaching up to USD 500,000.
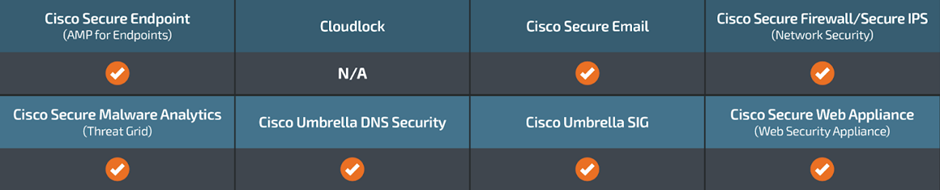
Cybersecurity Measures
The key solutions to prevent malware execution, block malicious websites and emails, detect malicious activity associated with threats like GhostLocker 2.0, and provide multi-factor authentication for network security.
This collaborative effort between GhostSec and Stormous in launching twin ransomware attacks underscores the evolving landscape of cyber threats targeting businesses worldwide.
The use of advanced tools and techniques highlights the need for robust cybersecurity measures to combat such malicious activities effectively.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.


.webp)


