Linux Admins Beware! Fake PuTTY Client That Rhadamanthys Stealer
PuTTY is among the most popular targets of hackers due to several reasons.
Firstly, it is used for remote access to servers and systems at large, hence a great ground for infiltration.
Exploiting vulnerabilities or...
AcidPour Attacking Linux Systems Running On x86 Architecture
Linux systems are used widely for servers, cloud environments, and IoT devices, which makes them an attractive target to cybercriminals, just as they are for any other platform.
Its extensive usage also provides a big...
Magnet Goblin Hackers Exploiting 1-day Vulnerabilities To Attack Linux Servers
Threat actors often target Linux servers due to their widespread use in critical infrastructure, web hosting, and cloud environments.
The open-source nature of the Linux operating system allows threat actors to study its code for...
New Bifrost Malware Attacking Linux Servers Evades Security Systems
A new Linux variant of Bifrost, dubbed Bifrose, was observed exhibiting a creative way to avoid detection, such as using a deceptive domain that imitates the official VMware domain.
Bifrost is a remote access Trojan (RAT) that was first...
GTPDOOR Linux Malware Exploiting GPRS Protocol For Stealthy C2 Communication
Threat actors exploit Linux malware due to the widespread use of Linux servers in critical infrastructure and web hosting.
Linux's prevalence makes it an attractive target for cybercriminals seeking to compromise systems, steal data, or...
Nood RAT Attacking Linux Servers To Steal Sensitive Data
Nood RAT was recently found to be utilized in malware attacks targeting Linux servers to steal sensitive information.
A Linux-compatible variant of Gh0st RAT is called Nood RAT. Gh0st RAT for Linux cases is constantly...
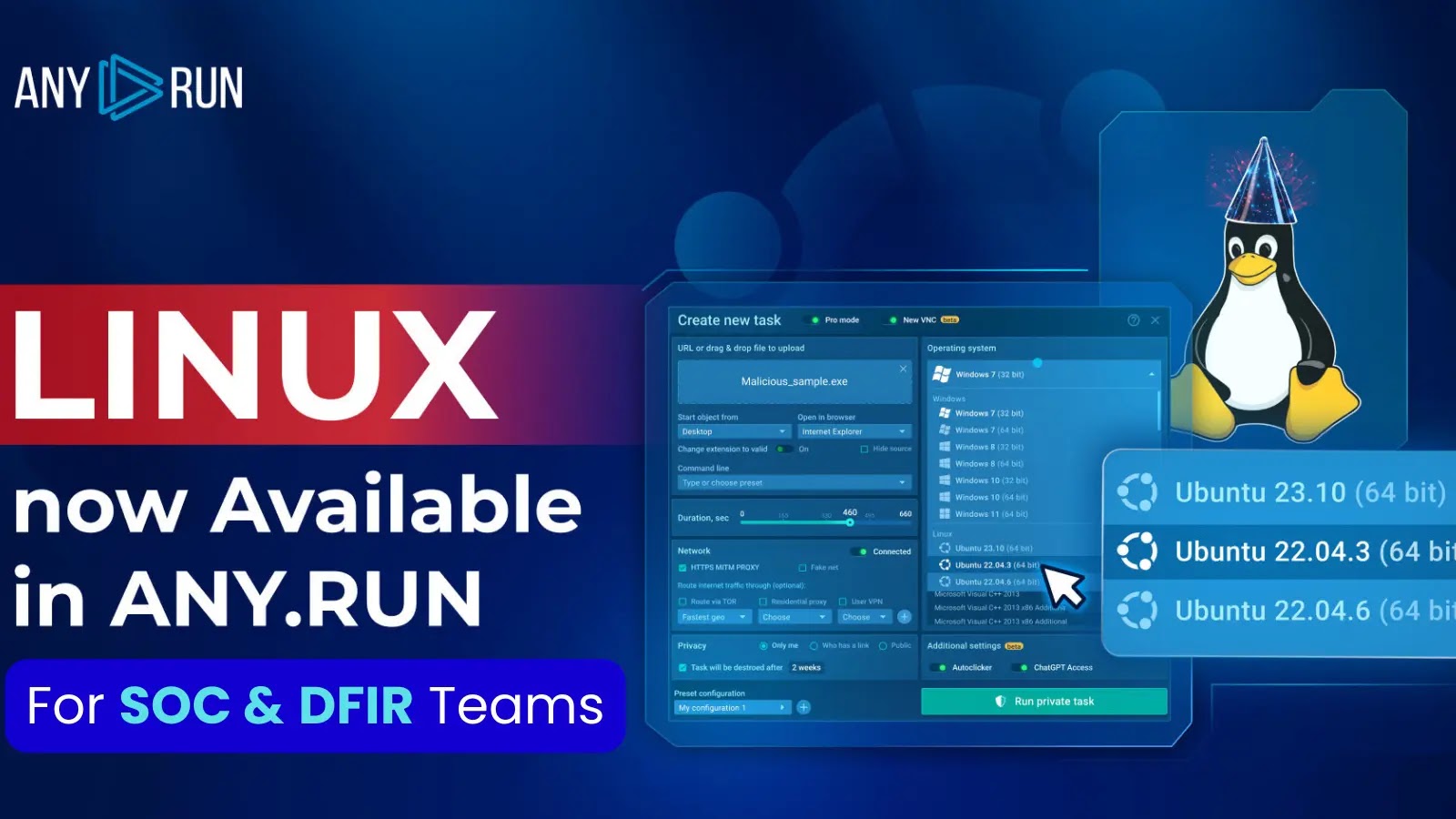
ANY.RUN Sandbox Now Analyzes Complex Linux Malware For SOC & DFIR Teams
The ANY.RUN sandbox has recently undergone an update to include support for Linux, strengthening its capacity to offer a safe and isolated atmosphere for examining malware and conducting threat analysis.
The latest feature introduced will...
Linux Shim Bootloader Flaw Expose Most Linux Distros to Code Execution Attacks
Shim is a small application used by open-source projects and other third parties for verifying and running the bootloader (typically GRUB2). The application was developed specifically to circumvent legal issues arising from license compatibility.
Shim...
Linux Kernel’s IPv6 Implementation Flaw Let Attackers Execute Arbitrary Code
With a CVSS score of 7.5, a high-severity IPv6 implementation issue in the Linux kernel identified as CVE-2023-6200 allowed attackers to execute arbitrary code execution.
Due to this vulnerability, an attacker from an adjacent network...
What is Linux Firewall? How to Enable Packet Filtering With Open Source Iptables Firewall?
One of the most important security tools for Linux is the firewall, which controls incoming and outgoing network traffic according to established security policies and prevents unauthorized users from accessing the system.
One popular...


%20(1)%20(1).webp)







-1.webp)


