Till September 2021, WhatsApp has no end in popularity, and it is one of the most popular global messenger app this worldwide. As per the report, there are two billion monthly active users for WhatsApp. In this, users can send text, voice messages, video calls, essential documents, the user’s current location, share images, and many more things.
Check Point Research has newly uncovered with Out-Of Bounds read-write vulnerability, which is available in this popular mobile application. But the issue is patched and theoretical that required complex steps to interact with the extensive user to exploit the thing.
It also allows the attacker to read the sensitive information from memory. In this scenario, WhatsApp has confirmed that they did not keep any evidence of abusing words.
This vulnerability is entirely related to the WhatsApp image filter, which functionality gets triggered as soon as the user opens the attachment, and it also containing the malicious craft image file. That time user tries to apply the filter and send the image to the attacker.
On November 10, 2020, CheckPoint Research disclosed this matter to the WhatsApp team, and they are coordinating to solve this issue.
WhatsApp has verified and acknowledged that the issue got fixed. This fix was already available from 2.21.1.13. Version, and it also has its source and filter image.
Technical Details:
As per the report, 55 billion messages get sent daily on WhatApp with 4.5 billion photos and 1 billion videos.
WhatsApp company is also focused on each process where the image types start from bmp, gif, png, and much more. Many also use the AFL fuzzing lab to check the malformed files. Many inputs files need modification, and this process is called a mutation.
There are few large set of modified file which gets used as an input in a target program. When the tested program gets crashes new bug comes for the security vulnerability.
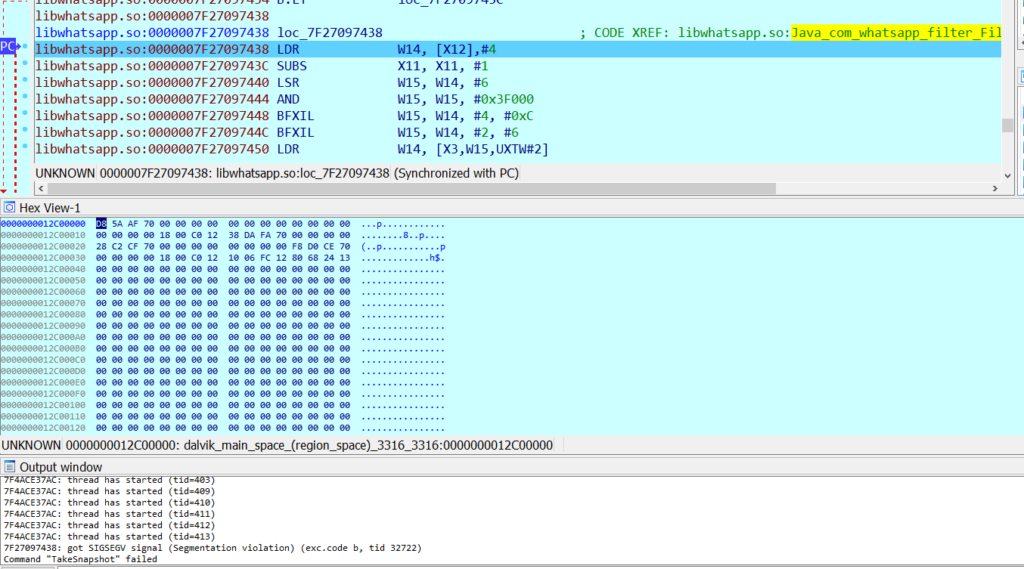
They also have the set of input that started to fuzz in the WhatsApp libraries. So while processing this there are few files that could not able to send and that image got filtered.
In this image filter process, original images get modified with some visual effects. Filtration is so promising that it involves reading and image contents. It also manipulates the pixel value, which includes writing data with a new destination image.
After getting crashes from the fuzzer, they have identified the memory corruption. So they started an investigation and were given a name called vulnerability. In CVE-2010-1910, the Heap-Based thing is the read and write the thing.
WhatsApp fix:
This WhatsApp has finally been fixed in version 2.21.1.13 and discloses the Security Advisory update. It changed the image format that is RGBA format. Every image has to validate the size by providing the correct height and weight.
WhatsApp Response:
In February 2021, as per the Security Advisory Report, WhatsApp had already disclosed the bug where they were working to improve and protect the people’s message. It is suggested that users always need to update their app when they get updated to avoid suspicious messages.
Follow us on Linkedin, Twitter, Facebook for daily Cybersecurity News & Updates





%20(1)%20(1).webp)