In this article, we will explore the concept of a Security Operations Center (SOC) in greater detail, including its functions, benefits, and key components.
In today’s digital world, cyber security risks are becoming increasingly serious. Organizations are at increased risk from data breaches, cyberattacks, and other security incidents that can have a strong impact on them.
In order to cope with these attacks, many organizations have established security operations centers.
Table of Contents
- What Is a Security Operations Center (SOC)?
- How a Security Operations Center Works
- What are the roles in Security Operations Center?
- What are the SOC Components?
- Key Functions of a SOC
- What Are the Benefits of a SOC?
- What are the SOC Challenges?
- Conclusion
What Is a Security Operations Center (SOC)?
A Security Operations Center is a central unit within an organization that provides management and monitoring of its cybersecurity operations.
It’s usually staffed by cyber specialists who are responsible for detecting and analyzing security incidents, as well as responding to them.
The center is designed to provide a complete view of an organization’s safety posture when it combines security alerts with network logs from different systems and applications.
The primary responsibility of the safety operations center shall be to anticipate, examine, and react in the event of a security incident.
These activities include surveillance of possible threats, examination of security events and logs, and vulnerability assessments in order to identify potentially dangerous vulnerabilities.
The SOC team shall be responsible for assisting with incident response, collaboration with other IT teams to reduce threats, and reporting incidents to management and other interested parties.
The major components of the SNE are SIEM systems, threat intelligence feeds, advice on handling incidents, and qualified cyber security professionals.
Security event logs from a variety of sources are collected and analyzed by the SIEM system, as are threat intelligence feeds that provide updated information on possible threats.
Detailed instructions on how to deal with each type of security event are included in the Incident Response Handbook.
The responsibility of qualified cybersecurity professionals lies in the implementation of these procedures and in responding to events that occur.
In a nutshell, the Security Operations Center (SOC) is a vital element of an organization’s cybersecurity infrastructure.
Establishing a central location to monitor, analyze, and respond to security incidents, will help ensure the safety, integrity, and availability of vital data and systems.
How does a Security Operations Center work?
A Security Activities Center (SOC) is designed to serve as a centralized place for controlling and keeping an eye on a company’s cybersecurity activities. Here are the key steps involved in how a SOC typically works:
Collecting and analyzing security events:
- An SOC collects information from a number of sources, e.g., security frameworks like firewalls, interrupt identification schemes, and endpoints.
- This information is collected and broken down by a Security Data and Occasions Management (SIEM) framework to recognize potential security dangers.
Detecting potential threats:
- The SIEM framework will be examined by the SOC team in order to spot any unforeseen movements or possible dangers.
- Through a combination of rules-based and behavior-based analysis, the SIEM System finds dangers.
Investigating potential threats:
- The SOC team investigates potential threats and assesses their seriousness in order to establish if they are a real danger or a false positive.
- To determine the origin and type of a threat, further information must be gathered, a forensic investigation must be performed, and threat intelligence information must be used.
Responding to security incidents:
- The SOC team will initiate a reaction to stop and lessen the effect of the occurrence if a security phase is confirmed.
- This entails adhering to established incident response standards and offering detailed instructions on how to handle particular event types.
Reporting and documenting incidents:
- The SOC team shall record each incident together with its nature and the action that has been taken to respond to it, as well as lessons learned.
- These data shall be used for the purposes of developing cybersecurity legislation in the Association and reporting to its different presidents and partners.
Continuous improvement:
- The SOC team will continuously review and update its processes, tools, and procedures in order to ensure that they continue to play an efficient role when faced with constantly evolving threats.
- Monitoring of new threats, assessment of incident data, and adaptation to improve the organization’s security posture are part of this process.
Briefly, the Security Operations Center SOC is gathering and analyzing safety events, identifying possible risks, assessing these threats, dealing with them, responding to incidents, recording occurrences, and constantly improving its practices and procedures.
It will help to ensure that all the core data and systems of an organization are kept confidential, pure, and accessible through proactive detection and response to security risks.
What are the Roles in the Security Operations Center?
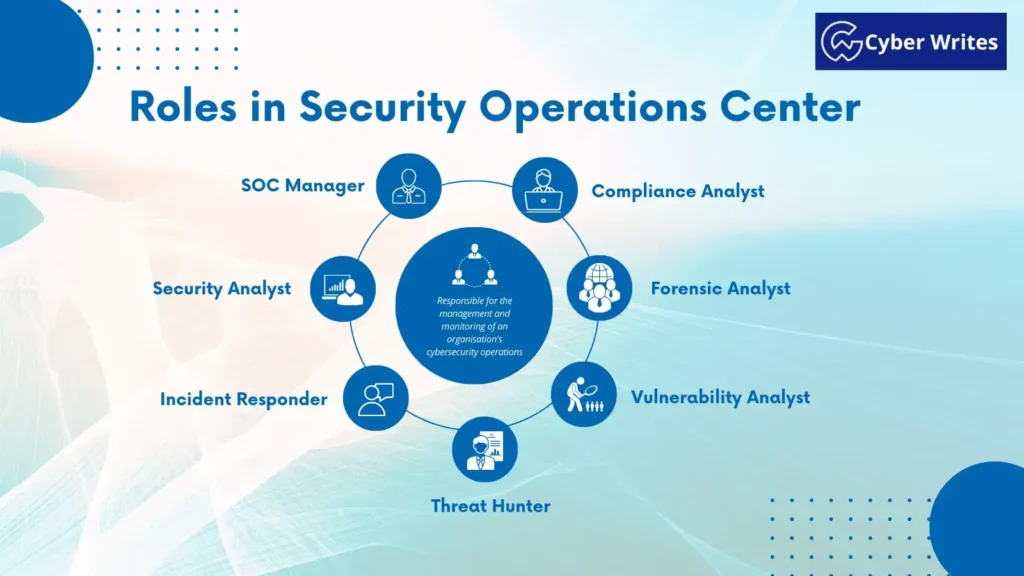
A Security Operations Center (SOC) consists of cybersecurity professionals who are responsible for the management and monitoring of an organization’s cybersecurity operations. Here are some of the key roles typically found in a SOC:
SOC Manager:
- The SOC manager is responsible for the day’s operations of the center.
- This includes keeping the Security Operations Center in line with the organization’s overall security strategy, developing and implementing safety policies and procedures, and managing a SOC team.
Security Analyst:
- Security analysts are watching for security events and identifying possible threats.
- They’re reviewing security logs, investigating incidents, and recommending ways to reduce risks in the field of safety.
Incident Responder:
- Security incidents need to be dealt with by incident responders as quickly as possible.
- They shall ensure that they comply with predefined incident response manuals and work on restoring systems and services which have been affected, to prevent and reduce the impact of an incident.
Threat Hunter:
- It is the threat hunters themselves who are responsible for the proactive detection and identification of potentially serious security threats by making use of modern Analytics and Threat Intelligence feeds.
- They undertake a review of potential threats, conduct forensic analysis, and issue recommendations for improving corporate security.
Vulnerability Analyst:
- Vulnerability analysts must carry out vulnerability assessments and penetration tests in order to locate potential security flaws.
- They look at the results of these studies and offer suggestions for reducing the risks they found.
Forensic Analyst:
- Investigating security issues as well as gathering and examining digital evidence are the responsibilities of forensic analysts.
- To ascertain the origin and scope of security issues, they employ forensic tools and methods.
- They then offer suggestions for strengthening the organization’s security posture.
Compliance Analyst:
- The Compliance Analyst is responsible for guaranteeing that the association meets generally pertinent security guidelines and norms.
- They screen consistency with managerial necessities, think up and execute security techniques and philosophy, and give propositions to further foster the affiliation’s consistency.
The security operations center is made up of a network of cybersecurity professionals performing numerous roles, such as SOC Manager, Security Analyst, Incident Response, threat hunter, vulnerability analyst, forensics analyst, and compliance analyst.
Effective management and control of an enterprise’s cyber security activities is crucial to each of these roles.
What are the SOC Components?
The organization’s primary security-related unit is the Security Operations Center, or SOMC.

The Security Operations Center will be the central entity to screen and dissect security cautions, distinguish and answer security episodes and execute and uphold well-being strategies.
The components of a SOC typically include:
People:
- Responsibility for monitoring, analyzing, and responding to security incidents lies with the SOC team.
- The team may be made up of safety analysts, incident response personnel, threat hunters, and managers.
Processes:
- The SOC shall follow the procedures in place for detecting, analyzing, or reacting to incidents.
- In order to take into account changes in the threat landscape, such processes shall be recorded, repeated, and updated on a regular basis.
Technology:
- SOCs rely on different technologies to monitor and analyze security events.
- These may include SIEM (Security Information and Events Management) tools, intrusion detection/prevention systems, endpoint detection and response (EDR) solutions, and intelligence feeds about the threat.
Data:
- The Security Operations Center must be able to access relevant sources of information, including network logs, system logs, and other security event data.
- In order to identify security problems and investigate safety breaches, this information will be used.
Facilities:
- SOCs need a safe and reliable location to operate from, with appropriate backup, network, and access controls.
The components of the Security Operations Center work together to create an integrated security strategy that can assist organizations in identifying and dealing with safety threats rapidly and effectively.
Key Functions of a SOC
The SOC performs a range of key functions to maintain the security of an organization’s assets and protect them from cyber threats. Some of the primary functions of a SOC include:
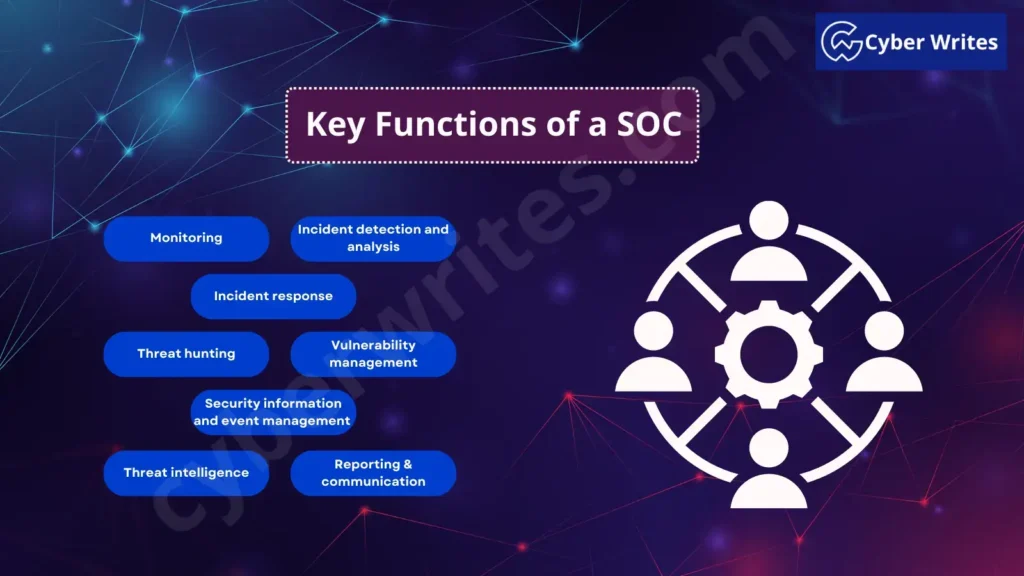
Monitoring:
- One of the main responsibilities of a SOC is to monitor an organization’s networks and systems for possible security incidents.
- This also means looking at logs or other data sources to detect abnormal behavior such as irregular web traffic on a network and attempts of unauthorized access.
Incident detection and analysis:
- When a security event is detected, the SOC team investigates the incident to determine its cause, scope, and severity.
- This includes conducting a thorough analysis of the incident and its impact on the organization’s systems and data.
Incident response:
- The SOC team conducts an investigation into a security event to ascertain its nature, extent, and severity.
- The incident’s investigation, as well as its effects on the organization’s data and systems, will also be thoroughly examined.
Threat hunting:
- The SOC proactively searches for potential security threats or vulnerabilities within the organization’s network and systems.
- This may involve analyzing network traffic, system logs, and other data sources to identify potential threats that may have gone undetected.
Vulnerability management:
- The SOC has responsibility for identifying, prioritizing, and mitigating security vulnerabilities in the organization’s systems and networks.
- In this way, it may involve vulnerability assessments, software patching or updates, and the introduction of security checks to reduce the risk of exploitation.
Security information and event management (SIEM):
- System operators shall use SIEM tools to collect and analyze information on security events from various sources, such as network data or system logs.
- The identification of potential security risks helps the organization assess its safety postures, which in turn gives invaluable insight.
Threat intelligence:
- To keep an eye on the newest security threats and to defend against them in a proactive manner, SOCs are using threat intelligence feeds.
- To find possible threats, it may be necessary to analyze data from open-source intel feedsOSINTs, dark web forums, and other sources.
Reporting and communication:
- The Security Operations Center (SOC) is responsible for providing periodic updates on an organization’s safety situation to key stakeholders, such as management and information technology staff.
- It likewise assists with illuminating financial backers and security strategy producers regarding conceivable gambling, which can provide them with a more noteworthy comprehension of their decisions.
The SOC is playing a critical role in the protection of an organization’s assets from security threats, through maintaining active safety measures, quick response, and incident detection, as well as constant improvement to its security posture with vulnerability management and threat discovery.
What Are the Benefits of Having a SOC?
There are several benefits to having a Security Operations Center (SOC) within an organization, including:
Improved security posture:
- The Security Operations Centre can help an enterprise’s total safety posture with rapid detection and removal of threats in order to provide a centralized location for the control and resolution of security issues.
Reduced risk:
- The Security Operations Center may help reduce an organization’s overall risk of security breaches or incidents by proactively monitoring potential security threats.
Faster incident response:
- Security operations centers can respond to security issues more quickly and efficiently, which lessens the negative effects on the business operations and reputation of their organization.
Better visibility:
- Thanks to the SOC’s access to an organization’s network and systems, IT professionals may better understand their environment and spot possible risks.
Compliance:
- Many legal regimes may demand the creation of a security operations center (SOC) in order for enterprises to have a strong security program in place.
Cost savings:
- The Security Operations Center can help reduce the potential costs of a security incident, such as lost productivity, data, or reputation, by identifying and responding to security risks more quickly. damaged.
Proactive threat hunting:
- In the event of an emergency, SOC could proactively identify vulnerabilities or possible threats to organizations’ networks and systems which may help mitigate security problems before they occur. happen.
A SOC may provide an organization with a proactive and efficient security program that can assist to ward off possible security risks and lessen the impact of security events.
What are the SOC Challenges?
A Security Operations Centre (SOC)’s setup and upkeep might be difficult for a number of reasons.
These include a lack of resources, such as skilled workers, infrastructure, and technology, alert fatigue brought on by an abundance of security alerts; the complexity of security threats, the challenge of integrating various IT systems and applications; the expense of maintaining and training qualified staff, and compliance with regulatory frameworks.
Resources, knowledge, and unwavering effort are needed to meet these obstacles in order to keep an efficient SOC and preserve a solid security posture.
Conclusion
A Security Operations Centre (SOC) is, in essence, a centralized location within an organization that is in charge of keeping track of, identifying, and responding to security issues.
It plays a crucial part in an organization’s security program by proactively monitoring possible security threats, quickly identifying and mitigating security events, and lowering the overall risk of security breaches or incidents.
Despite the advantages, creating and sustaining an efficient SOC may be difficult and need money, knowledge, and persistent work.
Overall, an organization may maintain a strong security posture and protect itself from possible security risks with the aid of a well-established and effectively managed SOC.


