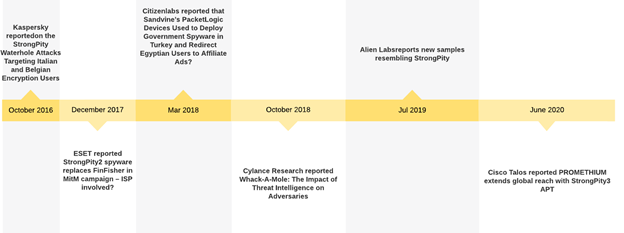
StrongPity or Promethium APT, also referred to as APT-C-41, has been active since 2012. It had been first publicly reported in October 2016, after cyberattacks against users in Belgium and Italy during which it used the watering-hole attack technique to deliver malicious versions of WinRAR and the TrueCrypt file encryption software.
The group mainly uses Truvasys, a first-stage malware used with trojanized common computer utilities, including WinUtils, TrueCrypt, WinRAR, or SanDisk.
Distinctive features of StrongPity APT
Researchers explain that StrongPity APT employs zero-day vulnerabilities and sophisticated attack tools to invade victims for espionage.
At present, the threat actors have expanded its TTPs to include watering hole attacks and mass phishing email campaigns.
High-level process flow of the StrongPity malware
The high-level execution flow of the StrongPity infection (as shown in the image below) is as follows:
- The APT actor employing the watering hole attack or Phishing email to deliver trojanized Partition Find and Mount software utility on the victims.
- The Trojanized installer drops multiple malware components in the %temp%\ndaData folder along with configuration files.
- The Launcher component is responsible for executing the Exfiltrate module, which runs another File searcher component.
- The File searcher component enumerates system drives and looks for target files with specific extensions. The list of extensions is embedded in the StrongPity payload.
- If the files are found in the victim’s machine, it will be copied into a temporary zip archive. After completion of adding the files to the archive, it splits into hidden .sft encrypted files.
- These hidden .sft files are sent to the C&C server through a POST request and are then removed from the disk-based on further C&C command. The Exfiltrate module has commands to delete the .sft files after being sent to the hacker C&C server

Final Word
The StrongPity APT group has ties to state-sponsored campaigns which include the potential to search and exfiltrate multiple files or documents from the victim’s machine.
This group uses a three-layer C&C for preventing forensic investigations and operates with fully functional Trojanized popular tools.
The Cyble Research team constantly monitoring to reap the threat indicators or TTPs of emerging APTs within the wild to make sure that targeted organizations are notified and protected.
You can follow us on Linkedin, Twitter, Facebook for daily Cyber security and hacking news updates.






.webp)
