The vast majority of companies had to switch to remote work due to the Covid-19 pandemic. As life for large swaths of the population moved entirely online, the cybercriminals were all set. The methods and tactics used by criminals on the Internet looking to exploit the massive increase in online traffic.
Kaspersky experts decided to take a look back at how the threat landscape has evolved since the beginning of the pandemic.
The Biggest Trends in Spam and Phishing
Phishing attacks proved to be a highly lucrative attack vector for cybercriminals. For instance, involving advertisements for masks, the primary goal is stealing money and/or payment information. A fake landing page for a mask advertised in a phishing email (as shown below). Users are prompted to put in their payment details for a mask that will most likely never arrive.
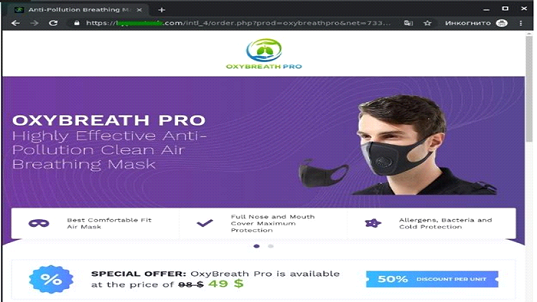
Scammers often mimic leading authority figures on the pandemic, like the CDC and the World Health Organization, to give their emails additional authority and increase the chances that users would click a malicious link.
Upon clicking the link, users could end up unintentionally downloading a range of threats on their computer, from various Trojans (malicious files that allow cybercriminals to do everything, from deleting and blocking data to interrupting the performance of the computer) and worms (files that are capable of destroying, blocking, modifying or copying data).

Remote Work and the Rise of Brute-Force Attacks
During the pandemic, very few companies had time to put the proper security measures in place. The result was that many became vulnerable to a host of new attacks as their employees began logging in to corporate resources from personal devices and on unsecured networks.
RDP is one of the most popular remote access protocols used by companies, making it a favourite target for attackers. In a brute-force attack, attackers attempt to randomly guess a username and password for the RDP connection by trying different combinations until they guess the correct one — and gain access to the confidential corporate resources.
As soon as lockdowns were announced, the number of brute-force RDP attacks radically increased — from 93.1 mln worldwide in February to 277.4 mln in March — a 197 percent increase. In February 2021, there were 377.5 mln brute-force attacks — a far cry from the 93.1 mln witnessed at the beginning of 2020.
Virtual Communication Platforms Under Attack
Internet demand reached extraordinary levels. Large companies from Facebook to Netflix to YouTube were forced to reduce their video quality to keep up with demand.
By May of 2020, the average daily number of attacks blocked by Kaspersky Web Anti-Virus had increased by 25%. The number of web attacks, after displaying a decline in the summer of 2020, reached a new peak in December as much of the world was facing a second wave of pandemic. Meeting and messenger apps, like Zoom and Teams, became a popular lure for distributing cyberthreats.
Awareness
Certainly, the more time users spend online, the more vulnerable they are to security risks. Users must view any email or website referencing the pandemic with a skeptical eye. Businesses need to reevaluate their usage of RDP and learn how to secure remote access.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.
Also Read
Enormous Growth in RDP Attacks as Hackers Targeting Employees Working From Home
Hackers Can Exploit Windows RDP Servers to Amplify DDoS Attacks






