Sygnia Incident Response Team found an advanced and persistent threat actor named “Praying Mantis” or “TG2021”, operating completely in memory. The attacks targeted Windows internet-facing servers to load a completely volatile, custom malware platform customized for the Windows IIS environment.
How does TG1021: “Praying Mantis” Operates?
Experts say TG1021 use a completely volatile and custom malware framework tailor-made for IIS servers. The core component, loaded into internet-facing IIS servers, intercepts and handles any HTTP request received by the server.
In addition, it utilizes a further stealthy backdoor and several post-exploitation modules to perform network reconnaissance, elevate privileges, and move laterally within networks.
TG1021 was observed to be highly aware of OPSEC (operations security). To avoid detection, the malware interfered with logging mechanisms, successfully evading commercial EDRs and silently awaiting incoming connections, rather than connecting back to a C2 channel and continuously generating traffic.
Windows IIS Server & Web Application Exploits
Researchers observed that these exploits abuse deserialization mechanisms and known vulnerabilities in web applications and are used to execute a sophisticated memory-resident malware that acts as a backdoor. This malware will be referred to as the “NodeIISWeb” malware.
The vulnerabilities that threat actor leveraged to exploit:
- Checkbox Survey RCE Exploit (CVE-2021-27852)
- VIEWSTATE Deserialization Exploit
- Altserialization Insecure Deserialization
- Telerik-UI Exploit (CVE-2019-18935 and CVE-2017-11317)
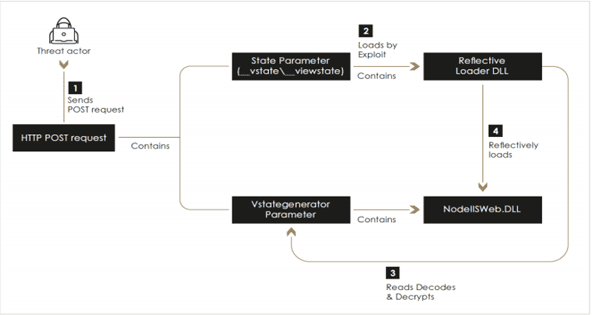
The vulnerability in the “Checkbox Survey” (CVE-2021-27852) application enables remote code execution (RCE) on the target resulting in the initial compromise of an IIS server. The vulnerability resides in an insecure implementation of the VIEWSTATE mechanism in .NET.
VIEWSTATE is a mechanism in .NET used to maintain and preserve web page session data between a client and a server. When using this feature any client that browses an application receives a serialized.

The deserialization process is exploited by the crafted object to compile an in-memory web shell, then the threat actor accessed it to load the malicious NodeIISWeb malware on the compromised asset.
Telerik-UI products (CVE-2019-18935, CVE-2017-11317), found to be vulnerable due to weak encryption, enabling a malicious actor to upload a file and/or to run malicious code. The vulnerabilities were used by TG1021 to upload a web shell loader to IIS servers accessible from the internet.
Researchers mention that ‘Praying Mantis’ targeting high-profile public and private entities in two major Western markets illustrates an increasing development of cybercriminals using difficult, nation-state attack methods to target commercial organizations.
As a result "Continuous forensics activities and timely incident response are essential to identifying and effectively defending networks from attacks by similar threat actors."
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.






.webp)