Recently, the security researchers at Avast have managed to gain unrestricted access to the components of the GhostDNS exploit kit after the malicious package itself fell into their hands.
Don’t know about GhostDNS? It is a kit of exploits for routers that, using cross-site request forgery (CSRF), changes the DNS settings and redirects the users to phishing pages to steal their credentials for authorization on various resources like online banking services, news sites, streaming services, etc..
The entire source code of the exploit kit, together with phishing pages in the form of a RAR archive, was published on a file-sharing site by a careless user who apparently did not pursue any criminal purposes.

The user did not protect the archive with a password and left Avast antivirus software enabled with the Web Shield active component protecting against malicious web content, which gave Avast analysts the opportunity to thoroughly study GhostDNS.
“We downloaded the linked file and found all the source code for the GhostDNS exploit suite,” the researchers said.
Source Code Structure
The name of the KL DNS.rar archive indicates that the tool uses DNS hijacking and keylogging to steal the credentials of its victims, as this file contains everything that needed to run a successful DNS hijack campaign.

In total, the archive contained two methods of attacking routers, Router EK and BRUT, and both of them used cross-site request forgery (CSRF) to change the DNS settings.
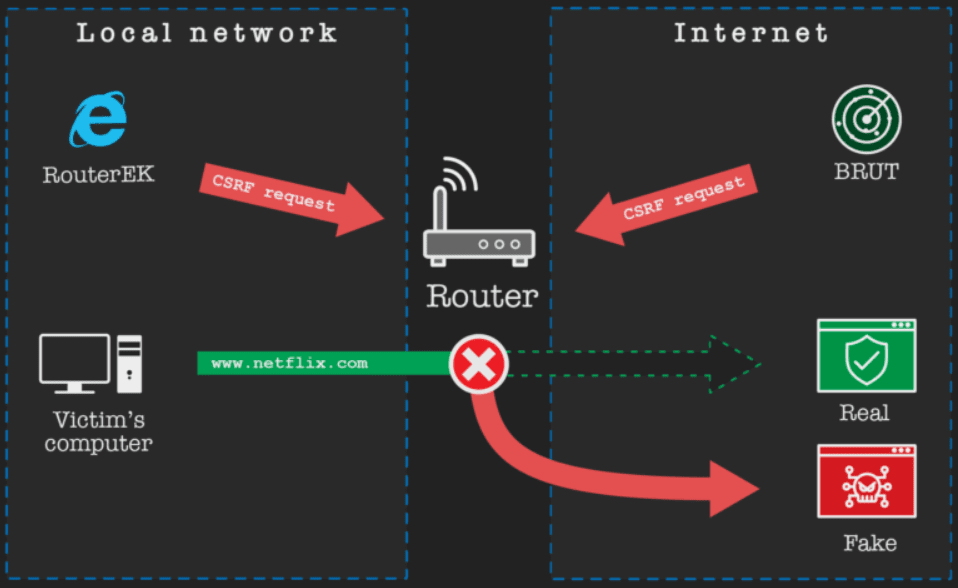
The Router EK attacks from the local network, and it requires the user to click on a malicious link, while the BRUT is a scanner for finding the routers that are accessible through the internet and attacking them without user intervention.
Number of targeted countries
Moreover, the security researchers have found a list of IP address prefixes in 69 countries, and most often in South America. Not only that, even for each prefix, 65,536 addresses were scanned in the given range in increasing order.
After the attacker picked the prefix, some versions of the exploit set printed the name GhostDNS, ‘with an error – GostDNS instead of GhostDNS’, in order to inform operators about cross-site request forgery (CSRF) execution.
Apart from this, the security researchers have also published the top targeted countries as well, and here they are:-
- Brazil
- The United States
- Mexico
- Colombia
- Argentina
- Chile
- Canada
- Venezuela
- Australia
- Costa Rica
- Germany
Phishing server and web pages
Along with the GhostDNS source code, the security researchers also found several phishing sites and some phishing web pages that were not yet implemented as well. Here, all these web pages indicate that the attackers are mainly focused on the biggest banks in Brazil, on Netflix, travel companies, etc.:-
- Banco Bradesco
- Itau
- Caixa
- Santander
- MercadoPago
- CrediCard
- Netflix
- Flytour Viagens
- Banco do Brasil
- Cartao UNI
- Sicoob
- Banco Original
- CitiBank
- Locaweb
- MisterMoneyBrasil
- UOL
- PayPal
- LATAM Pass
- Serasa Experian
- Sicredi
- SwitchFly
- Umbler
The primary goal of the attackers is to collect users’ data like the login credentials to online banking sites, and credit card numbers with all these phishing web pages. The attackers receive the stolen users’ information through email from the phishing server, and the security experts at Avast has found two different configurations of the email addresses that were used to send the emails with stolen data to the attacker.
Sender email: autenticadead[at]gmail.com, Destination email: jokersdead69[at]gmail.com
Sender email: dnsautenticador[at]gmail.com, Destination email: caixadeinfor2018[at]gmail.com
List of affected routers
- ASUS
- U2C
- Upvel
- Sitecom
- ZTE
- D-Link
- Planex
- ECI
- COMTREND
- Sagemcom
- Lenovo
- NETGEAR
- ZyXEL
- TP-Link
- eCos
- Thomson
- Technicolor
- TRENDnet
Hijacking the DNS settings through CSRF attacks is a common form used by the attackers to send phishing websites rather than the real sites to the users to steal sensitive information and login credentials.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.
Also Read
Top 10 Dangerous DNS Attacks Types and The Prevention Measures
Zero Trust – The Best Model For Strengthening Security in The Enterprise Networks – A 5-Step Guide






