Researchers identified security vulnerabilities in the VS Code Marketplace that could be exploited by malicious actors, as these flaws allowed extensions with malicious dependencies to gain credibility (through high install numbers) and access to user systems.
They found extensions that communicated with suspicious addresses, executed unknown binaries, and contained hardcoded secrets, highlighting the need for stricter security measures in the VS Code Marketplace to protect users from potential attacks.
VSCode extensions lack a permission system, allowing any extension to perform any action, which creates a security vulnerability because a seemingly harmless theme extension could execute code or access files without user knowledge.
.webp)
Extensions silently update in the background, creating a risk where a legitimate extension could be compromised later to inject malicious code, which mirrors how threat actors have exploited the Chrome Web Store in the past.
VSCode extensions have unrestricted access to the host machine, unlike browser extensions or add-ins, which grants them permission to execute system calls, spawn child processes, and import any NodeJS package, and the ability for extensions to interact with the OS in various ways makes it impossible for VSCode to regulate their behavior.
Researchers said traditional security tools designed to detect suspicious activity are also ineffective because legitimate VSCode functionality inherently involves reading files, executing commands, and creating child processes.
A lack of boundaries around extension behavior creates significant security risks.
.webp)
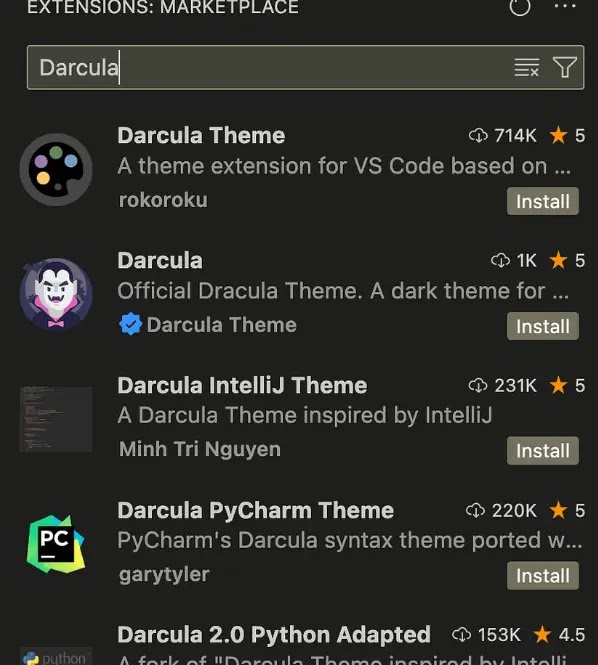
A security vulnerability was found in the Visual Studio Code Marketplace, as researchers discovered that anyone can become a verified publisher (the top 4% of publishers) by simply adding a cheap domain to their account.
The verification process is supposed to signify trustworthy extensions, but in reality, it only requires a $5 domain name and grants attackers credibility to distribute malicious extensions.
The information displayed, including the GitHub repository linked to the extension, is derived from the extension’s package.json file without verification, which allows malicious actors to impersonate open-source extensions and distribute potentially harmful code while appearing legitimate.
.webp)
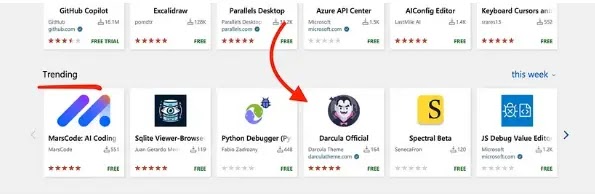
Additionally, the trending algorithm seems to prioritize extensions with low install numbers, and installing the extension repeatedly can manipulate the ranking by creating opportunities for attackers to gain exposure to developers.
.webp)
They identified design flaws in Visual Studio Code extensions that allow malicious extensions to steal authentication tokens and perform arbitrary code execution, which leverage unrestricted API access and a lack of permission models to gain access to sensitive information.
Amit Assaraf recommends that Microsoft implement permission models and restrictions on extensions to mitigate these risks, and the lack of manageability in VS Code makes it difficult for organizations to assess and govern extensions, highlighting the need for improved security controls.
Looking for Full Data Breach Protection? Try Cynet's All-in-One Cybersecurity Platform for MSPs: Try Free Demo





%20(1)%20(1).webp)