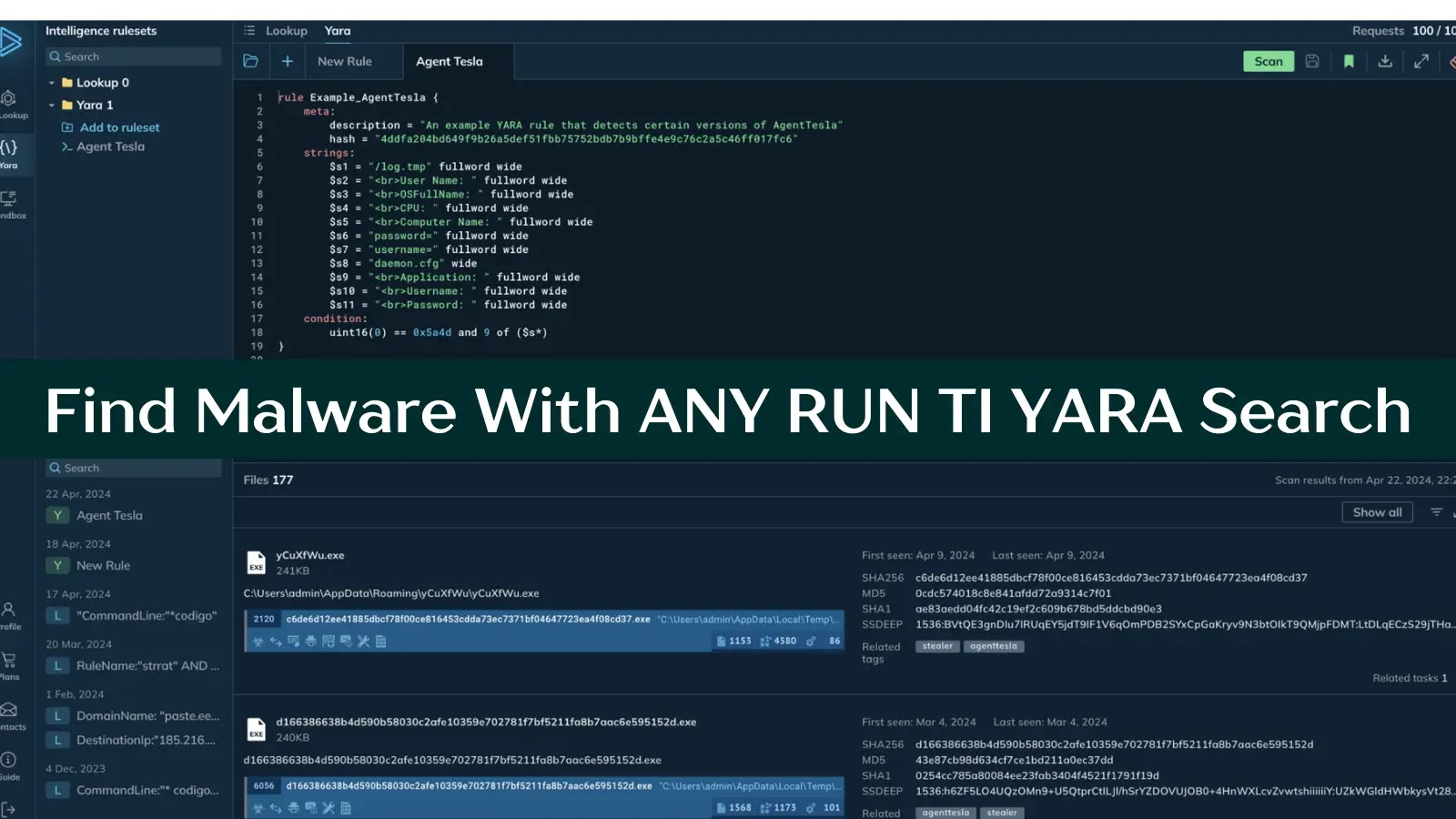
YARA is a rule-based malware detection tool that utilizes regular expressions and textual/binary signatures to create descriptions (rules) for identifying malicious files.
Within ANY.RUN TI, YARA Search allows you to write, edit, test, download, and manage your rules seamlessly, using your existing TI Lookup quota for searches.
- Find malicious files that match your YARA rules.
- Through associated recordings of sandbox analysis sessions, you can see how these files operate within a system and explore examples of their real-world attack scenarios.
- Download the identified files for further in-depth analysis.
Get started with YARA Search today and unlock its full potential! - Register for Free.
Analysts leverage these rules to scan a massive threat intelligence database (24TB) containing real-world samples collected by a global network of researchers and in-house analysts, as it allows them to hunt for malware by defining its characteristics and then searching for matches within the database.
ANY.RUN’s YARA Search functionality empowers security analysts to streamline their malware investigation workflow and uses existing Threat Intelligence Lookup quotas to search for malicious files based on user-written or downloaded YARA rules.
Analysts can not only identify matches but also observe the files’ behaviour within a sandbox environment through recorded sessions, which helps in understanding real-world attack scenarios, and the identified files can be downloaded for deeper forensic analysis.
YARA Search is a threat intelligence tool offered by ANY.RUN that allows users to search their database of malware samples using YARA rules and integrates with TI Lookup, so existing Enterprise plan users with access to TI Lookup already have YARA Search included.
Others can purchase access by contacting the ANY.RUN sales team, as YARA Search allows users to run multiple YARA searches in parallel, write and debug YARA rules in an online editor with syntax highlighting, and search for processes and sandbox analysis sessions based on file contents.
The system enables concurrent threat hunting through YARA searches and Threat Intelligence (TI) lookups and delivers initial results from a massive 24TB threat data repository within 5 seconds.
Results include matched files, triggered processes, relevant tags, file hashes, and matching sandbox analysis sessions. Users can seamlessly switch between searches and TI lookups or delve deeper by exploring process recordings in the ANY.RUN sandbox or downloading files for further local analysis.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
Additionally, it provides comprehensive analysis tools, and for each matched file by a YARA rule, users can access the Static Discovering window to view file metadata like TrID, EXIF data, hex values, clear text, and PE information.
Users can also download matched files for further analysis and reverse engineering within their own systems.
It also allows researchers to search its threat intelligence database using YARA rules, view metadata, and download matched files for further analysis.
Public YARA rules can be found on ANY.RUN’s GitHub repository, while YARA Search can return thousands of infected files based on a single HEX string in a YARA rule.
Complex searches or malware families not detected during submission may not yield accurate results, but ANY.RUN integrates its threat intelligence products to allow researchers to find real-world malware samples and see how they’ve been used in attacks.
YARA Search shares quota with TI Lookup, so if you’re an existing Enterprise plan user with access to TI Lookup, YARA Search is already included in your plan.
Are you from SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.