Google has announced a significant security initiative that will fundamentally change how Chrome handles unsecured web connections.
Beginning with Chrome 154’s release in October 2026, the browser will enable the “Always Use Secure Connections” feature by default, requiring users to approve access to any public website lacking HTTPS encryption before proceeding.
This strategic shift represents a critical advancement in browser security, addressing a persistent vulnerability that attackers continue to exploit.
Despite over a decade of progress toward universal HTTPS adoption, approximately 95 to 99 percent of Chrome navigations now use secure connections, leaving a small but significant percentage of traffic exposed to interception and manipulation attacks. The danger of unencrypted HTTP connections extends beyond mere data exposure.
Understanding the Security Threat
Attackers positioned between users and websites, known as man-in-the-middle actors, can hijack HTTP navigations entirely, redirecting users to malicious resources without detection.
This method of attack has proven highly effective in real-world scenarios, with documented cases of commercial surveillance vendors and state-sponsored threat actors using HTTP interception to deliver zero-day exploits and compromise targeted devices.
Unlike HTTPS sites that display “Not Secure” warnings, many HTTP sites immediately redirect to HTTPS, rendering the user completely unaware that an attack opportunity existed.
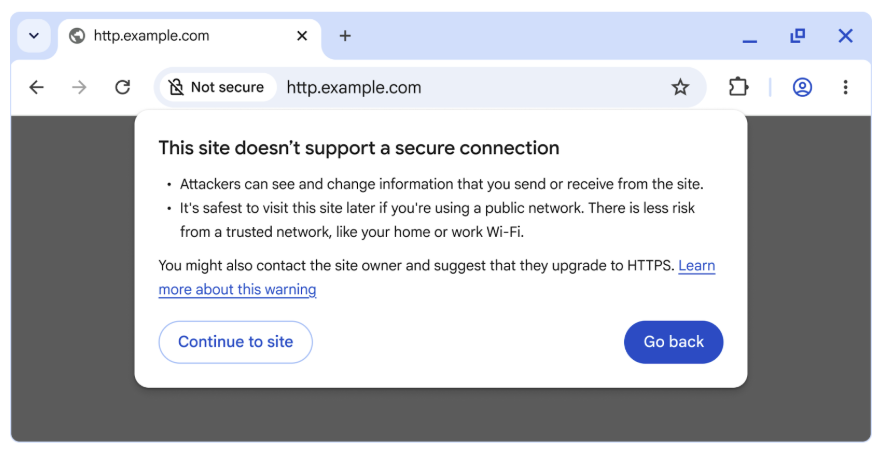
The Chrome Security team states that any unencrypted navigation, even at a small percentage, poses a potential risk to attackers.
Because these threats are not theoretical but actively exploited through readily available interception tools, the security implications justify aggressive mitigation strategies.
Google’s rollout strategy demonstrates careful consideration of user experience and the complexities of real-world deployment.
In April 2026, Chrome 147 will enable the feature exclusively for the over one billion users who have voluntarily opted into Enhanced Safe Browsing protections.
This initial phase provides a testing environment to validate warning frequency and user behavior before broader deployment.
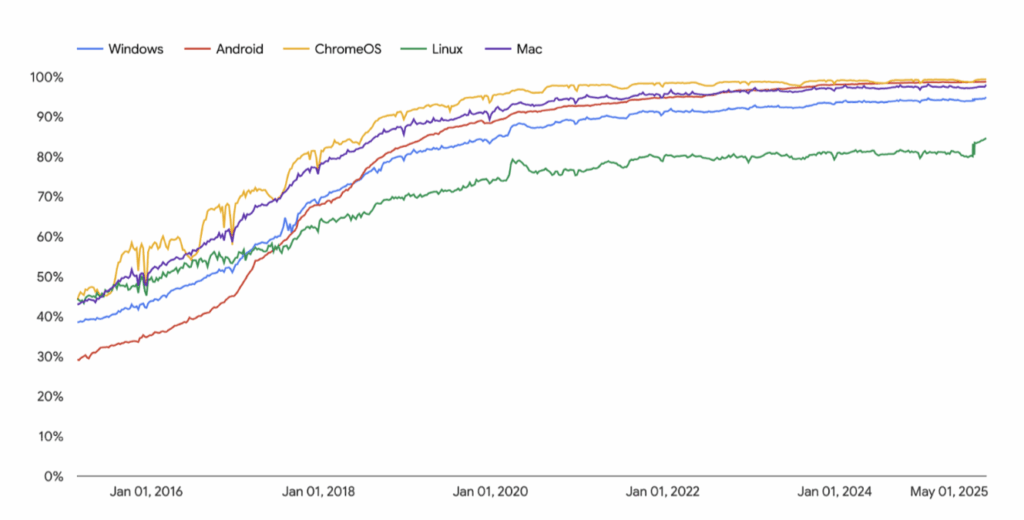
Chrome 141 already conducted a pilot program, revealing that the median user encounters fewer than 1 warning per week, with even heavy internet users experiencing fewer than 3 warnings.
This data contradicts assumptions about disruptive notification frequency, providing confidence for full-scale implementation.
A particularly thoughtful aspect of this initiative involves differentiating between public and private sites.
While Google will enforce strict HTTPS requirements for public websites, the implementation acknowledges that private sites, including local network devices and internal corporate systems, present reduced attack surfaces.
When analyzing platform statistics excluding private site traffic, HTTPS adoption rates approach 97 to 99 percent across all systems, indicating that most remaining HTTP usage concentrates on private infrastructure where obtaining trusted HTTPS certificates remains technically complicated.
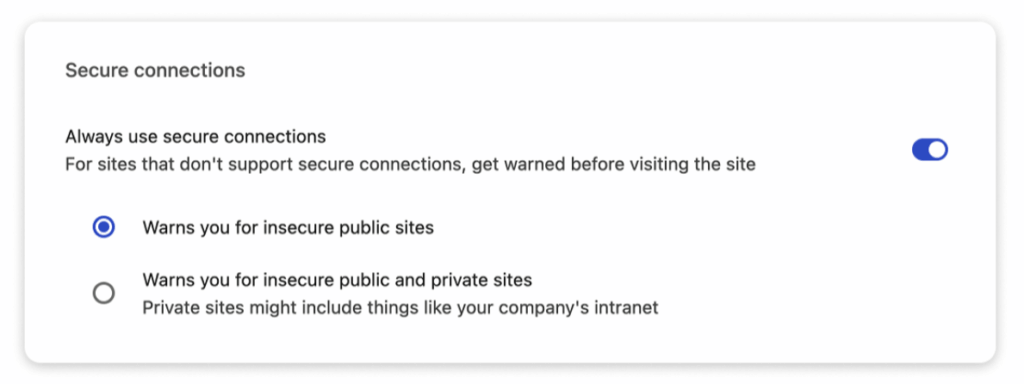
Website developers and IT professionals should immediately enable the “Always Use Secure Connections” setting to identify potentially affected sites.
Organizations managing Chrome deployments can reference Google’s comprehensive adoption guide to understand warning conditions and mitigation strategies.
Many HTTP-using organizations simply haven’t prioritized HTTPS migration, while others depend on HTTP for local network device configuration, a scenario now addressable through Chrome’s new local network access permission system.
Users retain full control, remaining able to disable warnings through settings if necessary, though Google strongly encourages adopting secure connections as standard practice moving forward.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.




.webp?w=218&resize=218,150&ssl=1)

.webp?w=100&resize=100,70&ssl=1)


