New Inception Attack Let Attackers Steal Sensitive Data from all AMD Zen CPUs
Phantom Speculation and Training in Transient Execution are two novel techniques that have been identified to leak arbitrary information from all modern CPUs.
A new technique called "Inception" has emerged from the combination of these...
Top 5 Security Vulnerabilities of 2023: Apache and OpenSSH Are The Most Vulnerable
The top 5 security vulnerabilities for 2023 have been revealed by a recent study, with Apache and OpenSSH services being the most vulnerable.
MOVEit and Barracuda Networks' attacks on the email supply chain have had...
SAP Security Update: 16 Flaws in Multiple SAP Products Addressed
SAP has released patches for 16 vulnerabilities with Critical, High, Medium, and Low severities. The CVSS scores for these vulnerabilities are between 3.7 (Low) to 9.8 (Critical) which contributes to 1 Critical, 6 High,...
New AD CTS Attack Vector Enables Lateral Movement Between Microsoft tenant
According to reports, the threat group known as “Nobelium” who were responsible for the SolarWinds attacks is now discovered to be targeting Microsoft tenants through the new Cross-Tenant Synchronisation (CTS) feature introduced by Microsoft.
CTS...
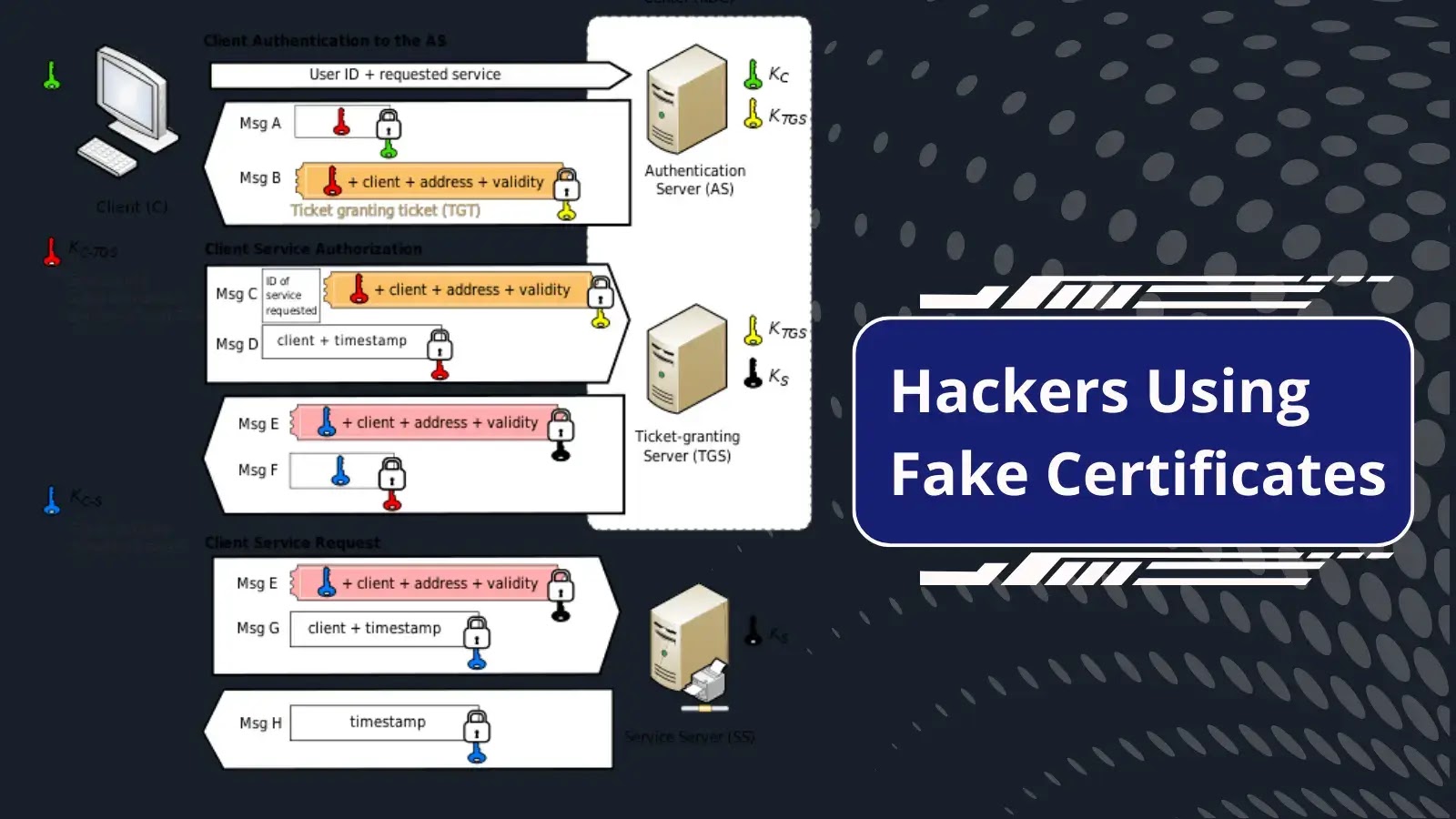
Hackers Using Fake Certificates to Infiltrate Corporate Networks
Using fake certificates, attackers gain unauthorized access to corporate network resources.
Attackers use such certificates to trick the Key Distribution Center (KDC) to get into the target company's network.
Shadow Credentials are an example of such...
Ivanti MobileIron API Access Flaw let Attackers Access Sensitive Information
There is a critical vulnerability in Ivanti's MobileIron Core 11.2 version that could allow a malicious actor to gain unauthorized access to restricted functions.
MobileIron core is a product of Ivanti that allows users to...
QNAP Operating Systems Flaw Let Attackers Launch DoS Attacks
QNAP operating systems are robust, user-friendly software platforms that power NAS and NVR devices. QNAP offers four operating systems, and here below we have mentioned them:-
QTS
QuTS hero
QuTScloud
QES
Since the wide use of its operating systems...
Canon Printers Wi-Fi connection settings Flaw Expose Sensitive Data
Exfiltration of data from disposed electronic devices has been one of the various techniques used by threat actors for stealing sensitive information about an organization.
This information is then used to gain unauthorized access...
Trust Wallet Browser Extension Flaw Lets Attackers Steal Funds Without User Interaction
Trust Wallet made a significant announcement on November 14th, 2022, unveiling its newly launched browser extension for wide usage.
The browser extension grants direct access to digital assets on multiple blockchains, a highly anticipated complement...
IBM Security Verify Access Flaw Let Attacker Launch Phishing Attacks
An Open-redirect vulnerability was discovered by IBM, which could allow threat actors to spoof the original URL of IBM Security Verify Access to lure victims into a malicious website and steal sensitive information.
IBM Security...





-1.webp)






.webp)