A Costly Mistake: How an Empty S3 Bucket Led to a Massive AWS Bill
AWS Customer Faces Massive Bill Due to Open-Source Tool Misconfiguration.
In a startling incident, an AWS customer faced a staggering $1,300 bill for S3 usage, despite creating a single, empty bucket for testing purposes.
The...
Gemini 1.5 Pro – Powered With Automated Malware Analysis To Detect Zero-Day
Google has introduced Gemini 1.5 Pro for malware analysis, an advanced AI tool capable of processing up to 1 million tokens. This tool revolutionizes automated malware analysis and marks a significant leap forward in...
AI-Based Brute-Forcing Attack Outperforming Probabilistic Model
Web Vulnerability Assessment and Penetration Testing (Web VAPT) aims to identify vulnerabilities in web apps.
However, current wordlist-based methods are ineffective since directory brute-forcing attacks can establish reachable directories.
Offensive AI is the integration of AI...
NSA, CISA Released Guidance And Best Practices To Secure The AI
In an era where artificial intelligence (AI) systems are becoming increasingly integral to our daily lives, the National Security Agency’s Artificial Intelligence Security Center (NSA AISC) has taken a significant step forward in enhancing...
Cypago Announces New Automation Support for AI Security and Governance
Cyber GRC software company Cypago has announced a new automation solution for artificial intelligence (AI) governance, risk management and compliance. This includes implementation of NIST AI RMF and ISO/IEC 42001, the newest AI security...
Microsoft Adds 5 New AI Tools to be Added with Azure AI
Microsoft has unveiled a suite of new tools within its Azure AI Studio.
These innovations are designed to address the growing concerns around prompt injection attacks, content reliability, and overall system safety, marking a...
DNS Tunnel Keylogger – An Offensive Post-Exploitation Tool For Pentesters
A new keylogging server and client tool have been released on GitHub for pentesters. The tool utilizes DNS tunneling to transmit keystrokes through firewalls, potentially evading detection covertly.
The tool, DNS-Tunnel-Keylogger, was designed for...
AttackGen : AI-Based Incident Response Tool With MITRE ATT&CK Framework
In the ever-evolving landscape of cybersecurity, the need for advanced tools to simulate and test incident response is critical.
AttackGen, a cutting-edge incident response testing tool, has emerged as a game-changer in this domain....
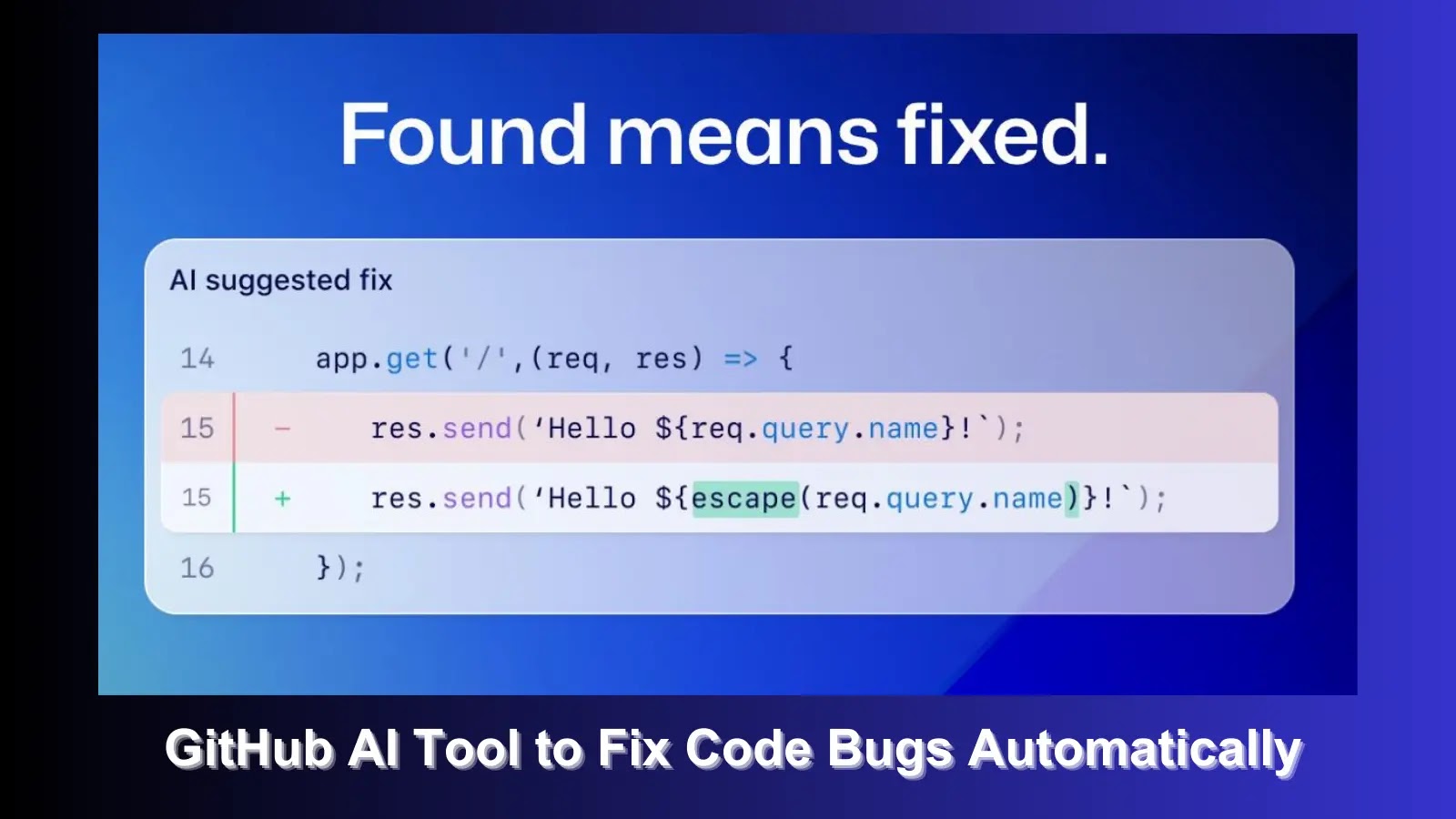
New GitHub AI-Powered Tool Can Automatically Fix Code Vulnerabilities
In a groundbreaking move to enhance code security, GitHub has announced the launch of a new feature called "code scanning autofix," which leverages the power of GitHub Copilot and CodeQL to resolve code vulnerabilities...
Researchers Detailed Red Teaming Malicious Use Cases For AI
Researchers investigated potential malicious uses of AI by threat actors and experimented with various AI models, including large language models, multimodal image models, and text-to-speech models.
Importantly, they did not fine-tune or provide additional training...






.webp)
.png)