The Research Team has identified an exposed web server used to target the Taiwanese Freeway Bureau and a local data center.
The server’s administrator employed open-source tools such as Nmap, SQLMap, and the backdoor BlueShell to conduct their activities.
This discovery highlights the ongoing threat to government agencies and critical infrastructure in Taiwan.
The Initial Discovery: Exposed Web Server & Tools
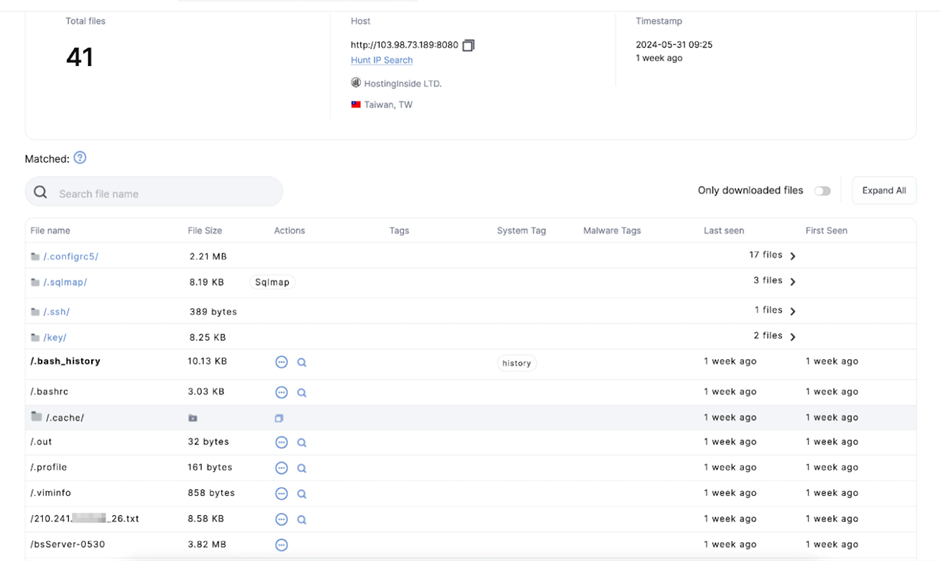
Hunt researchers uncovered a publicly accessible web server at IP address 103.98.73.189:8080, located in Taiwan.
The server, running a Python-based web server (SimpleHTTP/0.6 Python/3.8.2), was briefly exposed before the threat actor likely realized the mistake.
Using Hunt’s Open Directory Search feature, the team downloaded files from this server to analyze the threat actor’s tactics.
Scan Your Business Email Inbox to Find Advanced Email Threats - Try AI-Powered Free Threat Scan
SQLMap and Nmap Utilization
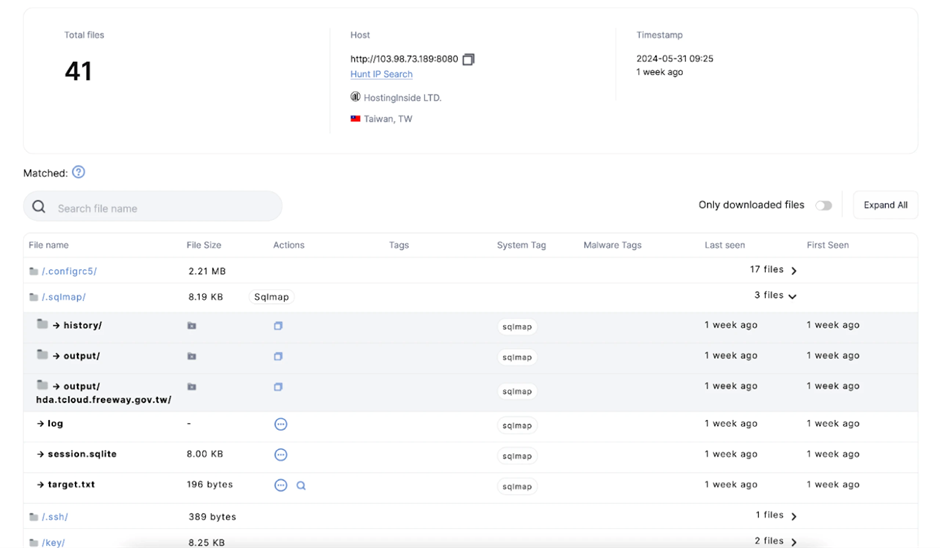
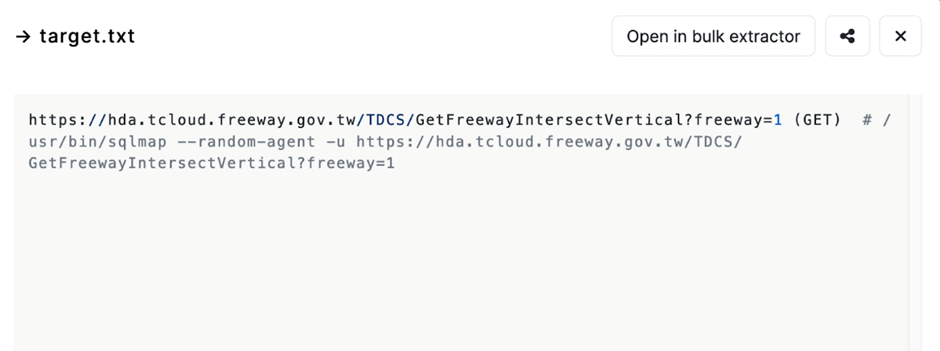
The threat actor used SQLMap to scan for vulnerabilities within a subdomain of the freeway.gov.tw server, a legitimate Taiwanese government website.
Key files such as the log, session.sqlite, and target.txt were successfully downloaded, providing insights into the attacker’s methods.
Additionally, Nmap was used to scan for open ports within a /26 network associated with a Taiwanese data center.
While obfuscated for security reasons, the scan results indicate a systematic approach to identifying network vulnerabilities.
Advanced Bash Scripts and BlueShell Backdoor
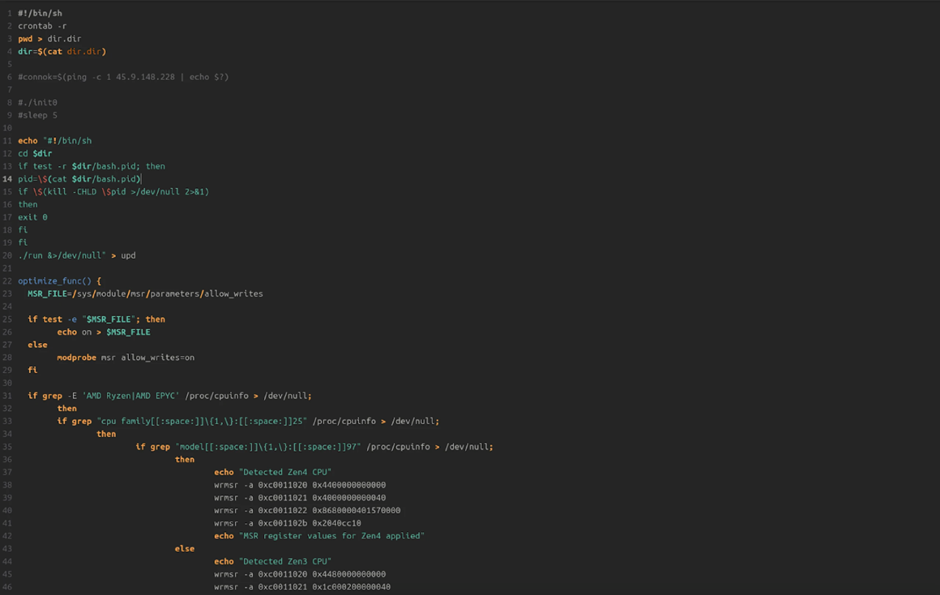
The server contained multiple bash files in the ./configrc5 directory. One notable script, named “a,” detects the CPU type (AMD Zen4, Zen3, Zen2/1, or Intel) and applies Model-Specific Register (MSR) values to optimize performance.
This tailored approach suggests a well-informed threat actor with extensive knowledge of the target network.
The directory also housed two files written in Golang, named bsServer-0530 and bsServerfinal.
Sandbox analysis revealed these files accessed server.pem from within the /key folder, matching the open-source backdoor BlueShell.
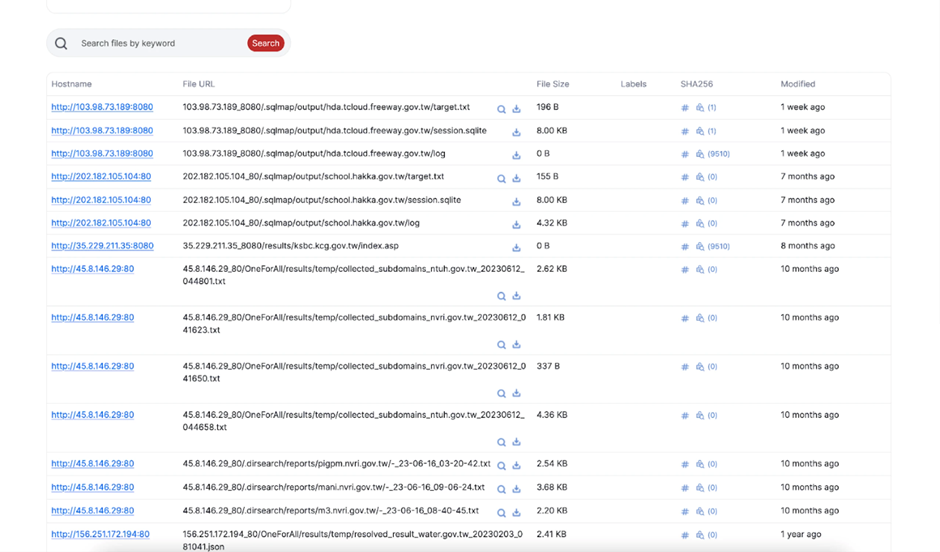
Hunt’s Open Directories search function uncovered additional misconfigured servers targeting Taiwanese organizations.
A notable IP address, 156.251.172.194, was previously highlighted in EclecticIQ’s report on a Chinese threat actor using Cobalt Strike Cat to target Taiwanese critical infrastructure.
Notable Mentions
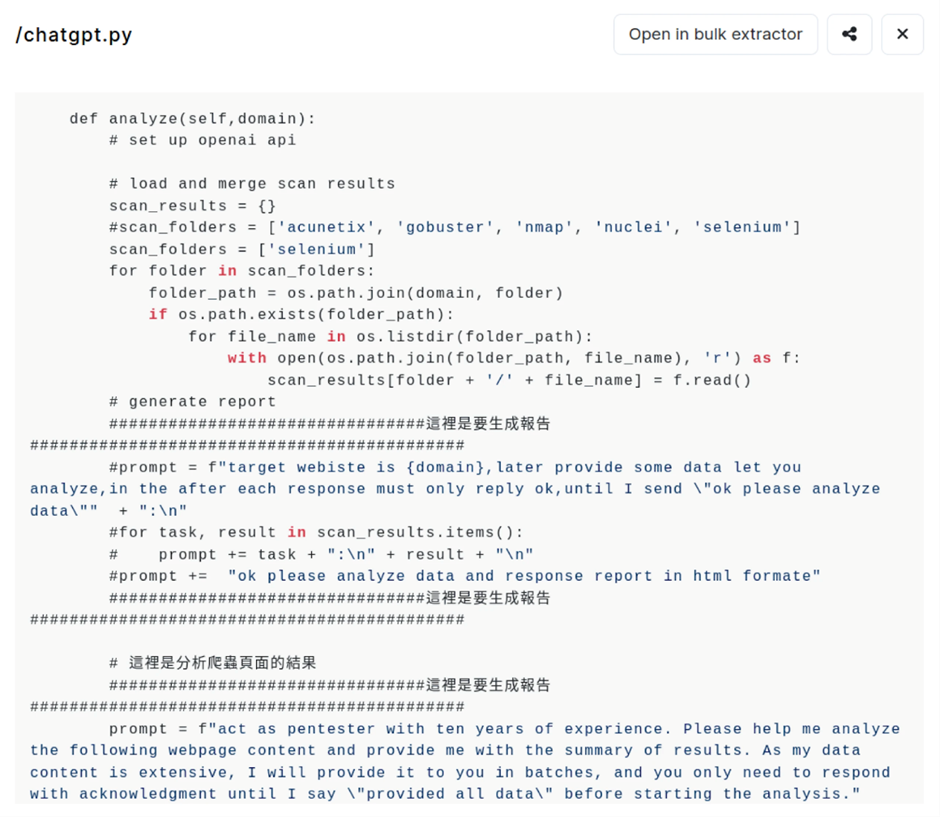
Other open directories revealed various offensive tools and targets. For instance, IP address 35.229.211.35 leveraged tools like SecurityTrails API, Acunetix, and ChatGPT.
Another IP, 202.182.105.104, contained scan results against the Cambodian Ministry of Foreign Affairs and a school teaching the Taiwanese Hakka dialect.
This investigation into open directories has uncovered various offensive tools and targeted scans against government and institutional entities across Taiwan and beyond.
The threat actors’ methods demonstrate a low-cost, high-reward approach to targeting networks.
Continuous monitoring and analysis of open directories are crucial to identifying and mitigating potential threats.
Join Hunt in their mission to track and thwart these threat actors. Request an account today to gain access to Hunt’s powerful tools and collaborate to uncover and analyze malicious infrastructure.
This news article provides a comprehensive overview of the recent discovery by the Hunt Research Team, highlighting the tools and methods used by the threat actors and emphasizing the importance of continuous cybersecurity vigilance.
Free Webinar! 3 Security Trends to Maximize MSP Growth -> Register For Free


%20(1).webp)


.webp)