ANY.RUN’s Process Tree shows all the processes that start when a file or URL is run in its sandbox, along with their hierarchical relationships.This is accomplished by capturing the initial process initiated by the sample and any more processes it generates. This provides a comprehensive understanding of the sample’s behavior and interactions with the system.
It allows for quick identification of parent-child process relationships, tracing potential malicious activity back to its source, and overall comprehension of the sample’s functionality at a glance.
According to the ANY.RUN detailed write-up, the process tree visualizes process relationships and provides tools for analysis, while icons indicate suspicious activities and process signatures. Clicking icons reveals static information like PE details, memory dumps, and configuration files.
Tags identify malware families and threats; a score is calculated based on process events. Highlighting lets you hover over PIDs in other tabs to see the corresponding process in the tree, while triangle icons allow you to collapse groups.
Clicking a process opens a tab with event descriptions, classifications (Dangers, Warnings, Others), MITRE ATT&CK mappings, and event categorization by criticality, which also affects the malicious score.
SOC analysts can use process tree analysis to determine a file’s legitimacy initially. When a seemingly harmless file (like an image) triggers execution within a virtual machine, the resulting process tree exposes the file’s true nature.
Even if signature-based detection fails, the analyst can identify malicious intent based on the spawned processes, allowing for swift reporting and the removal of the threat.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
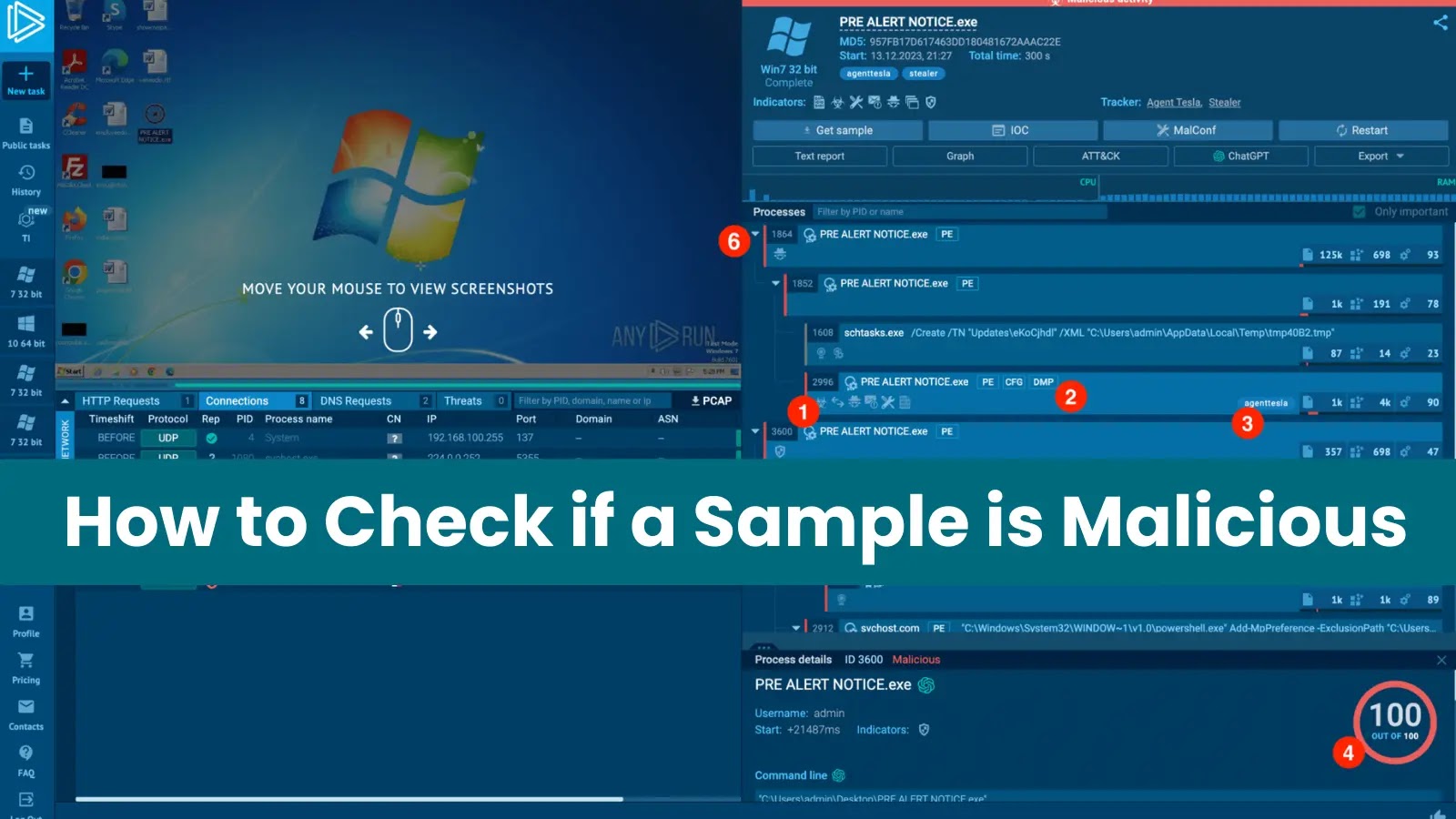
ANY.RUN, a threat analysis platform, displays a process tree to analyze a loaded executable file, which shows how processes are spawned and related to each other. In this example, the process tree of “PRE ALERT NOTICE.exe” reveals multiple concerning aspects.
First, a process (PID 2996) with the tag “agenttesla” is found, which strongly points to malicious activity centered on two instances of “PRE ALERT NOTICE.exe” (PIDs 1864 and 3600), which seem to be operating independently within the system.
Analysis of process ID 1864 reveals a potentially malicious program named “PRE ALERT NOTICE.exe,” which replicates itself and spawns additional processes. One child process uses “shtasks.exe” to create a scheduled task named “Updates\eKoCjhdl”.
The task likely attempts to establish persistence on the system or upload malicious data and the randomly generated task name and the use of the temporary directory (AppData\Local\Temp) for the task definition file (tmp40B2.tmp) are strong indicators of malicious intent.
The malicious process (PID 3600) creates deceptive svchost.com processes to hide itself by spawning powershell.exe instances, which could be used to download more malware.
PID 3600 replicates itself by creating another instance of the primary malware executable. For analysis purposes, the Process Graph view is helpful for visualizing the relationships between processes and identifying the malicious ones, even when dealing with a large number of processes.
What is ANY.RUN?
ANY.RUN is a cloud-based malware lab that does most of the work for security teams. 400,000 professionals use ANY.RUN platform every day to look into events and speed up threat research on Linux and Windows cloud VMs.
Advantages of ANY.RUN
- Real-time Detection: ANY.RUN can find malware and instantly identify many malware families using YARA and Suricata rules within about 40 seconds of posting a file.
- Interactive Malware Analysis: ANY.RUN differs from many automated options because it lets you connect with the virtual machine from your browser. This live feature helps stop zero-day vulnerabilities and advanced malware that can get past signature-based protection.
- Value for money: ANY.RUN’s cloud-based nature makes it a cost-effective option for businesses since your DevOps team doesn’t have to do any setup or support work.
- Best for onboarding new security team members: ANY. RUN’s easy-to-use interface allows even new SOC researchers to quickly learn to examine malware and identify signs of compromise (IOCs).