A sophisticated malware campaign has been compromising the update mechanism of eScan antivirus software to distribute malicious backdoors and cryptocurrency mining software.
The campaign, dubbed GuptiMiner, has been linked to a threat actor with potential connections to the notorious Kimsuky group.
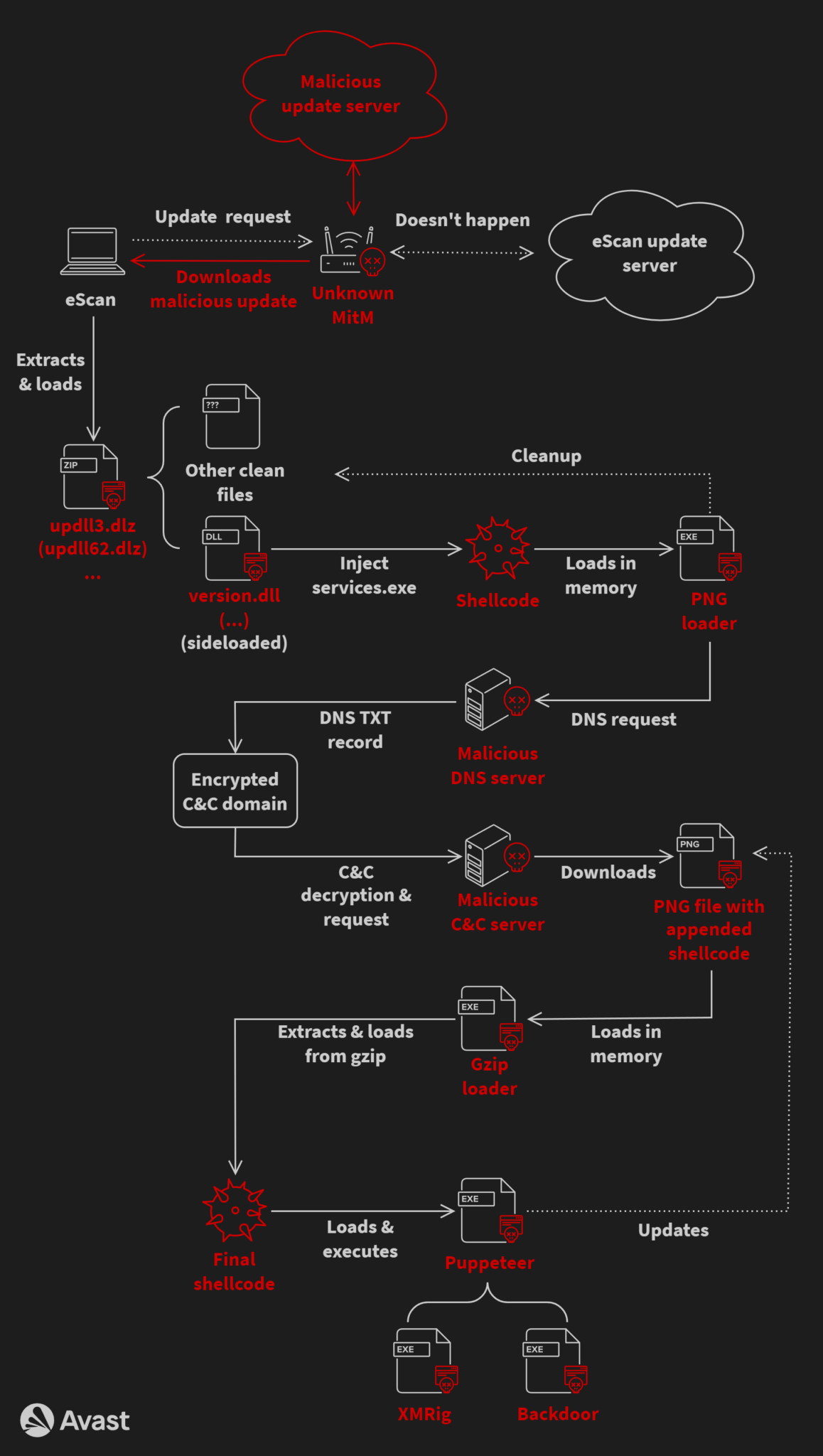
GuptiMiner leverages a man-in-the-middle attack to exploit vulnerabilities in the update process of the eScan antivirus, a product of an Indian cybersecurity firm.
By hijacking this process, the attackers have been able to distribute their malware to unsuspecting users stealthily.
Avast’s investigation led to the discovery of the issue, which was promptly reported to eScan and India’s Computer Emergency Response Team (CERT). On July 31, 2023, eScan confirmed that the vulnerability had been addressed and resolved.
GuptiMiner Operation
The GuptiMiner campaign is not limited to a single type of malware but includes a variety of tools designed to breach large corporate networks.
Two distinct backdoors have been identified, each with the capability to provide attackers with remote access to infected systems.
Additionally, the campaign’s final payload involves deploying XMRig, a well-known cryptocurrency mining software, which harnesses the processing power of infected machines to mine Monero (XMR).
Since 2018, GuptiMiner has undergone significant evolution, with its developers continuously enhancing its capabilities. The malware exhibits a complex infection chain and employs advanced techniques such as:
- DNS requests to attacker-controlled servers
- Sideload malicious payloads
- Extracting executable code from seemingly benign images
- Utilizing a custom trusted root anchor certification authority to sign payloads
These sophisticated methods not only demonstrate the attackers’ high level of expertise but also highlight the persistent threat posed by such malware campaigns.
The GuptiMiner campaign represents a severe security threat, particularly for large organizations that rely on antivirus solutions to protect their networks.
Hackers’ ability to use a trusted update process as a delivery mechanism for malware is a concerning development in the cybersecurity landscape.
In the GuptiMiner operation, the attackers used advanced techniques such as DNS requests to the attacker’s DNS servers, sideloading, extracting payloads from images, and signing payloads with trusted root anchor certification authority.
Avast immediately mitigated the threat upon discovery by disclosing the vulnerability to the affected parties.
The swift response from eScan and the subsequent resolution of the issue has prevented further exploitation of the vulnerability.
Users are advised to ensure their antivirus software is up to date and to remain cautious of any unusual system behavior that could indicate a compromise.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP.





