Spoofing is a malicious practice that disguising as a legitimate source to gain sensitive information, or to gain access to victims’ devices. An attacker can trick you into believing that he is from the source by spoofing.
Spoofing is a type of attack where, “what we see will look like it, but it is not”.
Types of Spoofing
Email Spoofing:
About 90% of Cyber Attacks are carried out through emails. Email spoofing is something where the attacker sends an email posing as a legitimate sender by spoofing the “From:” address. The Victim will not notice the sender’s address and falls for the attacker.
Prevention: Check the sender’s address if an unwanted email is received and do not download attachments unless the sender is verified. Verify the email header and make sure the header is not modified.
Call Spoofing:
Call Spoofing is a strange practice in which attackers make a call in half of the reputable organizations and seeking personal information such as credit card and debit card details, bank details and other personal information.
Prevention: Do not give away sensitive information such as credit card details, bank account details, or social security number over the phone.
Website Spoofing: This attack is technically called Phishing where the attacker creates a website and tricks us into entering credentials.
Prevention: Always check the website URL before entering credentials. If the URL does not match the original website URL do not enter credentials.
ARP Spoofing: Expanded as Address Resolution Protocol Spoofing. This Spoof is of two types,
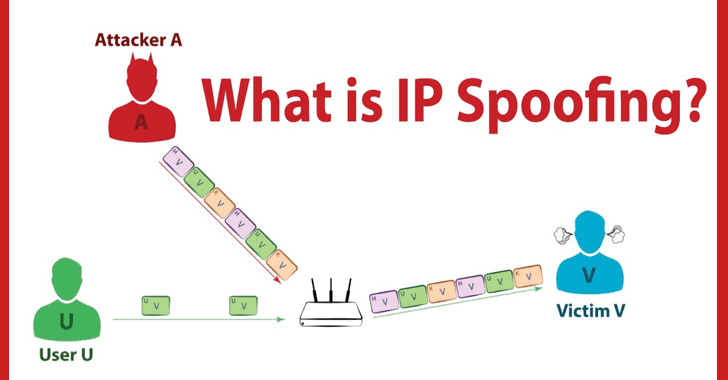
- IP Spoofing: The attacker finds the private IP address, and tricks the router in believing he is also from the same network. Usually, this attack is done to gain access to a server that is only accessible for specified systems inside a network.
Prevention: Decreasing the Subnet and Clearing the log of empty IP addresses will reduce this type of attack.
- MAC Spoofing: All of us know that MAC Address is the permanent address given by the manufacturer. And the attacker can spoof the MAC address of a particular system inside a network to gain illegitimate access to a server.
Prevention: Installing Packet Filters or Dynamic ARP Inspections will reduce these type of Spoofing Attacks.
Spoofing Infographics