A sophisticated malware campaign dubbed Shadow Vector is actively targeting users in Colombia through malicious Scalable Vector Graphics (SVG) files that act as decoys for deploying dangerous remote access tools.
The campaign distributes spear-phishing emails impersonating trusted Colombian institutions, particularly the judicial system, delivering SVG attachments that appear as urgent court notifications to unsuspecting recipients.
These deceptive emails leverage SVG smuggling, a technique recently added to the MITRE ATT&CK framework, which allows attackers to hide malicious content within seemingly benign image files.
The SVG files render cleanly in browsers and often bypass traditional email security controls, making them particularly effective in phishing operations.
Once opened, they direct users to download and extract password-protected archives hosted on public file-sharing platforms like Bitbucket, Dropbox, and Discord.
Acronis Threat Research Unit (TRU) identified the ongoing campaign, noting that it reflects a high level of operational flexibility and evolving technical maturity among threat actors targeting Latin America.
“Shadow Vector blends traditional social engineering, public infrastructure abuse, and stealthy execution techniques,” Acronis researchers observed in their analysis published on June 18, 2025.
.webp)
The malware payloads include remote access tools (RATs) such as AsyncRAT and RemcosRAT, both delivered through advanced techniques like DLL side loading and driver-based privilege escalation.
These RATs enable comprehensive system compromise, allowing attackers to capture keystrokes, steal banking credentials, and gain full remote control of infected systems.
The immediate focus of the campaign appears to be data theft, targeting both individuals and organizations. However, Acronis researchers warn that the established access could potentially be leveraged for more destructive actions such as ransomware deployment in future attacks.
Sophisticated Infection Chain
The infection mechanism employed by Shadow Vector demonstrates significant technical sophistication. When a victim opens a malicious SVG attachment, they are prompted to download a password-protected archive.
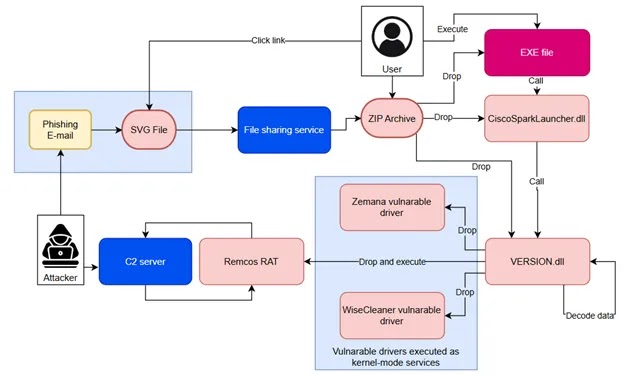.webp)
Inside this archive is a legitimate-looking executable alongside several DLL files, one of which contains the malicious RAT payload.
The attack utilizes DLL side loading, where a legitimate application invokes a function from a specific library, but Windows instead loads a malicious version placed in the same directory.
For example, in one variant, the initial executable calls the BrotliEncoderCreateInstance() function from a weaponized ‘libbrotlicommon.dll’ file.
“The malicious DLL employs several anti-analysis techniques, including inserting additional bytes before the PE header to disrupt automated parsing,” notes the Acronis report.
This manipulation causes errors in PE detection and decompilation tools, effectively acting as a lightweight anti-analysis mechanism.
After loading, the malware creates a legitimate process (AddInProcess32.exe) in a suspended state and performs process hollowing to inject and execute the malicious module.
This technique involves a series of Windows API calls including NtAllocateVirtualMemory, GetProcessHeap, and NtResumeThread, allowing the malware to run under the context of a trusted system binary to evade detection.
Recent iterations of the campaign have evolved to include a more modular approach, deploying a loader associated with Katz Stealer.
This loader features advanced capabilities such as UAC bypass, process injection, and optional persistence mechanisms, with payloads sometimes hidden as Base64 within text or image files retrieved from the Internet Archive.
The Superior Council of Judicature in Colombia has issued public advisories warning judicial employees and citizens about these phishing attempts, encouraging verification procedures and reporting of suspicious communications to institutional channels.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free trial






.webp?w=100&resize=100,70&ssl=1)


