Magento Vulnerability Let Attackers Inject Backdoor On E-commerce Websites
A sophisticated vulnerability within the Magento ecommerce platform has been unveiled, posing a significant threat to online merchants and shoppers alike.
The vulnerability, identified as CVE-2024-20720, allows attackers to inject a persistent backdoor into Magento...
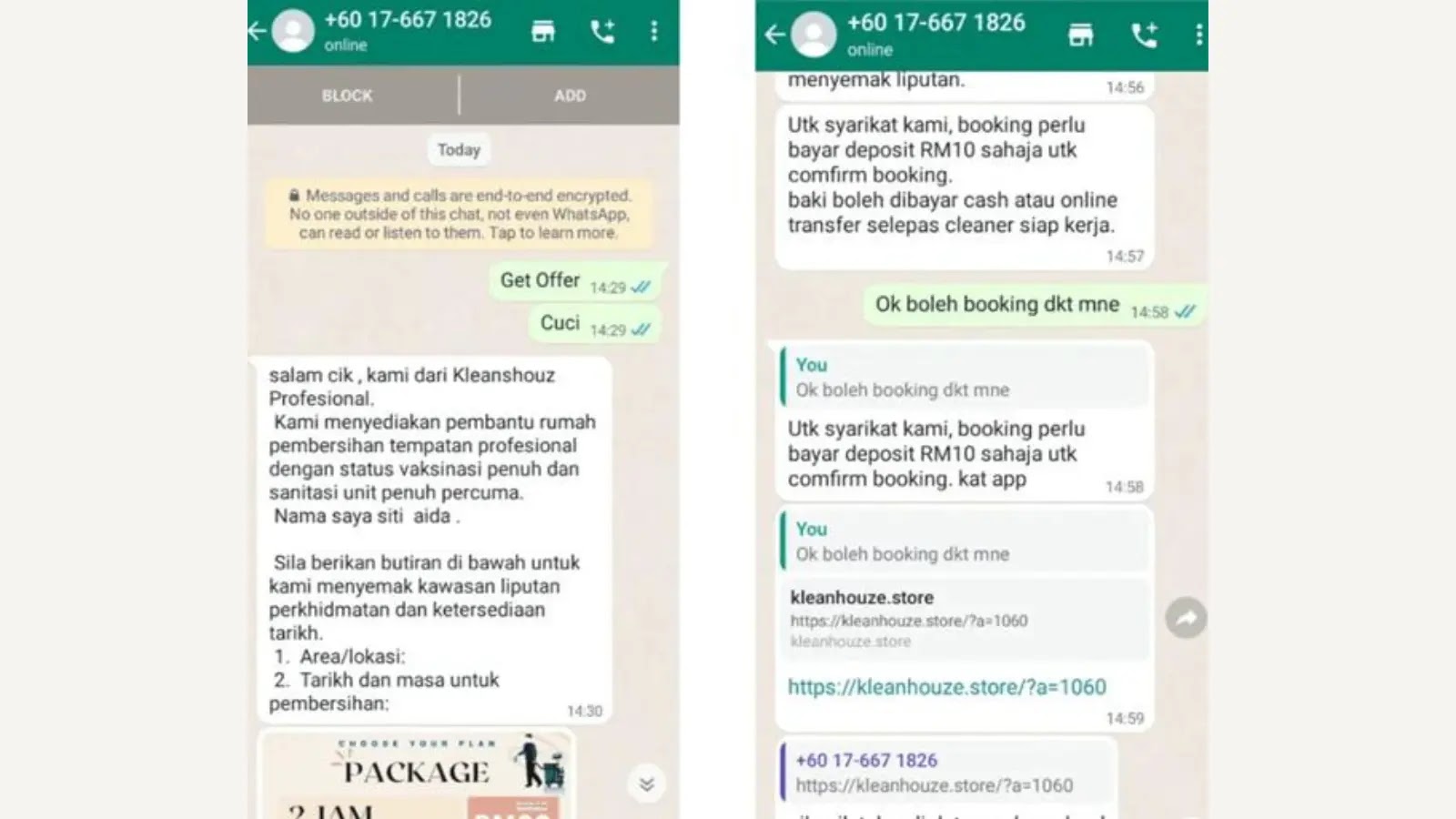
New Fake E-Shopping Attack Hijacking Users Banking Credentials
A fake e-shop scam campaign has been targeting Southeast Asia since 2021, as CRIL observed a surge in activity in September 2022, with the campaign expanding from Malaysia to Vietnam and Myanmar.
The attackers use...
Rhadamanthys Stealer Using Weaponized PDF Files To Attack Oil And Gas Sector
Hackers use weaponized PDF files as they have the ability to incorporate malicious codes or scripts within a well-known and trusted form of PDF which is often not detected by security measures.
If the person...
Researchers Unveil The Attackers Behind The Agent Tesla Campaign
Check Point Research has exposed a recent wave of cyberattacks utilizing the infamous Agent Tesla malware. This campaign targeted organizations in the United States and Australia.
First appearing in 2014, Agent Tesla masquerades as legitimate software...
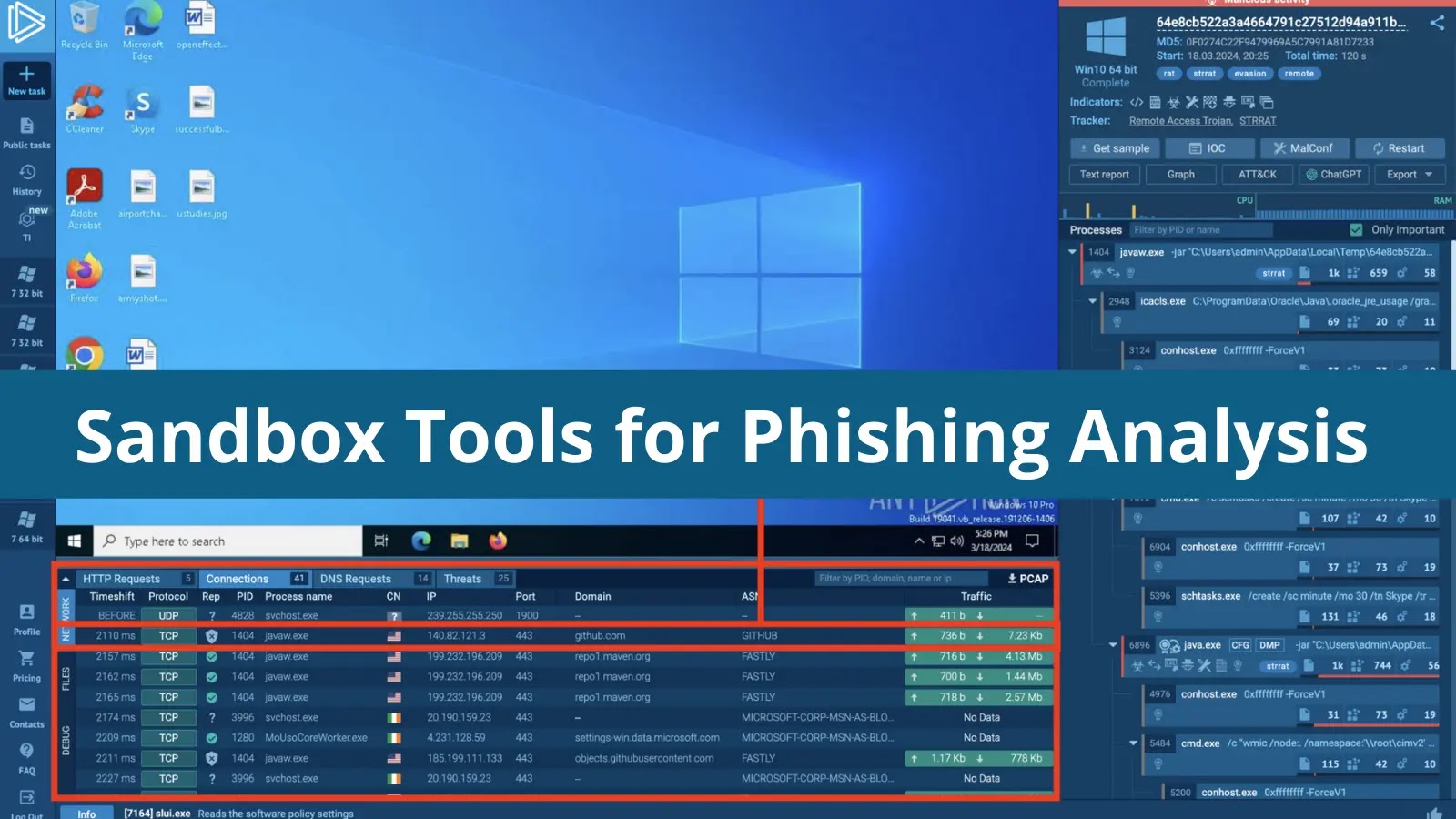
What is Malware Packers? How To Analyse With ANY.RUN Sandbox – SOC/DIFR Guide
Antiviruses can quickly detect malicious executable files, but attackers can bypass this by using packers to compress and obfuscate the code, making it difficult for antivirus software to analyze.
Packers are similar to compression...
Hackers Exploit Google Ads Tracking Feature To Deliver Malware
Google Ads is a big platform with a wide user base, which makes it attractive to threat actors who want to reach many targets at once.
These malicious ads can also be created or...
Vultur Android Malware mimic As McAfee Security App To Attacks Users
Vultur, Android banking malware, has been observed incorporating new technical features, which allow the malware operator to remotely communicate with the victim's mobile device.
Additionally, Vultur has begun disguising more of its harmful behavior by...
Hackers Attack macOS Using Infostealer To Steal Sensitive Data
Over the past year, macOS users, particularly those in the cryptocurrency sector, have been increasingly targeted by infostealers. These malicious programs aim to harvest credentials and data from crypto wallets.
amf Threat Labs has been...
Agent Tesla’s Added New Tools & Tactics to Its Arsenal
The persistent search for money and the threat actors increasingly becoming more sophisticated are driving the alarming rate of malware change.
Every day, new types of malware are created and put into circulation at an...
Hackers Using Weaponized PDF Files to Deliver Mispadu Banking Malware
Mispadu, a banking trojan initially targeting Latin America, has expanded its attacks to Europe, stealing credentials through phishing emails and malicious URLs.
The attackers utilize stolen credentials for further phishing attacks, making it a significant...








%20(1).webp)