The notorious hacking group BianLian, known for its sophisticated cyber attacks, has shifted its focus to extortion-only operations following the release of a decryptor by Avast in January 2023.
GuidePoint’s Research and Intelligence Team (GRIT) has been closely monitoring BianLian’s activities and, together with their Digital Forensics and Incident Response (DFIR) team, has uncovered a new method of attack involving the exploitation of TeamCity servers.
Initial Breach: TeamCity Vulnerabilities Exploited (CVE-2024-27198 and CVE-2023-42793)
The attackers exploited vulnerabilities identified as CVE-2024-27198 and CVE-2023-42793 to gain initial access, although the specific CVE used remains undetermined due to unavailable logs.
Are you from SOC and DFIR teams? – Join With 400,000 independent Researchers
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data If you want to test all these features now with completely free access to the sandbox:
This initial foothold allowed the threat actors to create users and execute malicious commands under the TeamCity service account.
TeamCity Server Exploitation
Upon gaining access, the attackers conducted reconnaissance using native Windows commands and discovered additional infrastructure, including two build servers ripe for further exploitation.
They deployed legitimate Winpty files to facilitate command execution. They used BITSAdmin to deploy a malicious PowerShell script, web.ps1, and other communication tools with their command and control (C2) server.
In a recent breach, GuidePoint’s DFIR team detected malicious activity within a client’s network that originated from a compromised TeamCity server.
After several unsuccessful attempts with their standard GO backdoor, BianLian pivoted to a PowerShell implementation, providing similar functionality. The PowerShell backdoor was obfuscated but not beyond deconstruction.
The GRIT team managed to decrypt and analyze the script, revealing its true nature as a backdoor with capabilities akin to BianLian’s GO trojan.
Deeper Analysis
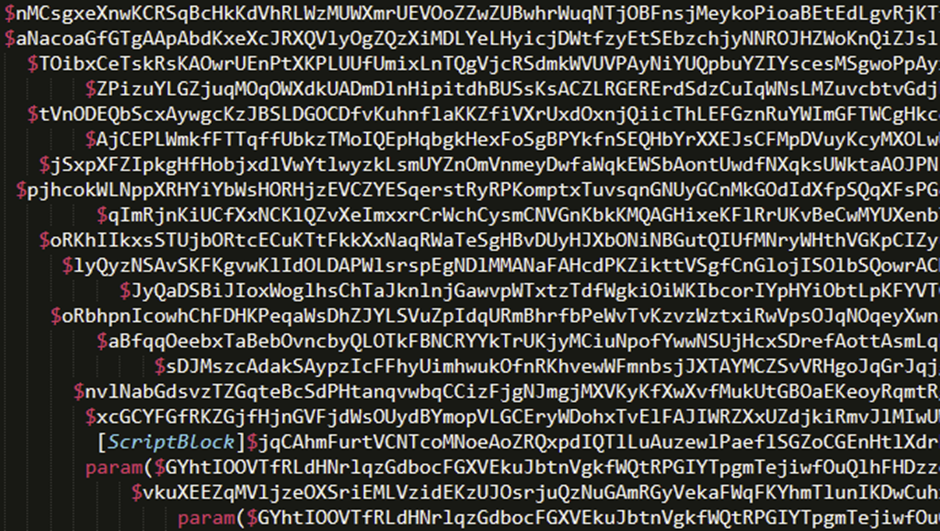
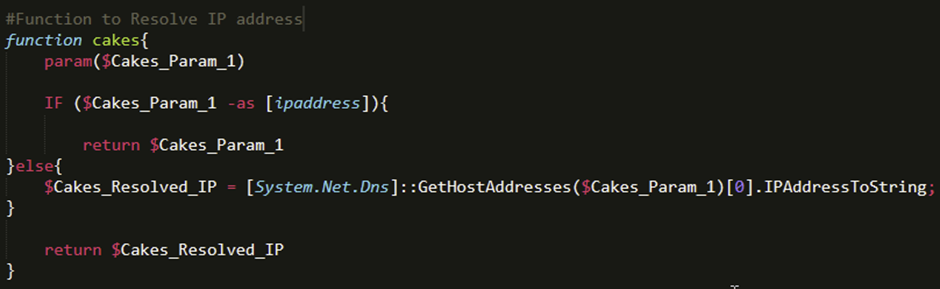
The deobfuscated script revealed cakes and cookies functions, with the latter managing network connections and execution.
The script utilized Runspace Pools for efficient asynchronous code execution and established SSL streams for secure communication with the C2 server.
This level of sophistication allows for flexible and stealthy post-exploitation activities.
Attribution to BianLian: Connecting the Dots
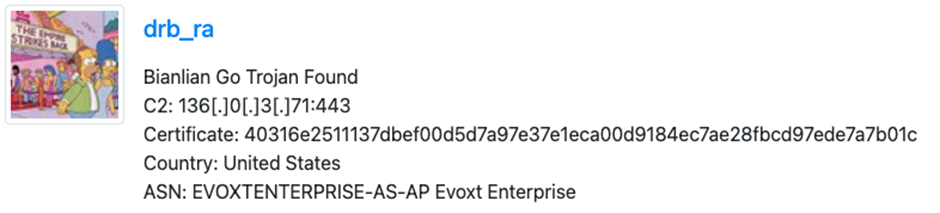
The GRIT team confirmed the backdoor’s association with BianLian by analyzing specific parameters passed to the cookies function and cross-referencing IP addresses with known BianLian infrastructure.
Additionally, detections of the Microsoft AV signature Win64/BianDoor.D provided further evidence linking the PowerShell backdoor to BianLian.
BianLian’s ability to adapt and exploit emerging vulnerabilities highlights the need for organizations to prioritize patching, incident response planning, and threat intelligence-informed penetration testing.
A proactive security posture, combined with effective response capabilities, is essential to defending against BianLian’s and other cyber threat actors’ evolving tactics.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.


.webp)


.webp)