An unpatched security vulnerability was found in the domain name system (DNS) component of a popular C standard library in many well-known IoT products.
Researchers from Nozomi Networks Labs said, “The flaw was caused by the predictability of transaction IDs included in the DNS requests generated by the library, which may allow attackers to perform DNS poisoning attacks against the targeted devices”.
The flaw affects the DNS implementation of two popular C libraries called uClibc and uClibc-ng that are used for developing embedded Linux systems.
uClibc is used by major vendors such as Linksys, Netgear, and Axis, or Linux distributions such as Embedded Gentoo. It is one of the possible C standard libraries available and specifically focuses on embedded systems.
uClibc-ng is a fork particularly designed for OpenWRT, a common OS for routers possibly deployed throughout various critical infrastructure sectors.
Researchers say that a “flaw affecting a C standard library can be a bit complex since there would be hundreds or thousands of calls to the vulnerable function in multiple points of a single program and the vulnerability would affect an indefinite number of other programs from multiple vendors configured to use that library”.
Poisoning Attack
In a DNS poisoning attack, an attacker is capable to trick a DNS client into accepting a forged response, as a result inducing a certain program into performing network communications with an arbitrarily defined endpoint, and not the legitimate one.
The successful exploitation of the flaw could allow a Man-in-the-Middle attack since the attacker, by poisoning DNS records, is capable of rerouting network communications to a server under their control.
The attacker might then steal and/or manipulate information transmitted by users, and perform other attacks against those devices to completely compromise them.
Technical Analysis of the Issue
The experts from Nozomi Networks Labs noticed the trace of DNS requests performed by a connected device using the uClibc library and found some weirdness caused by an internal lookup function.
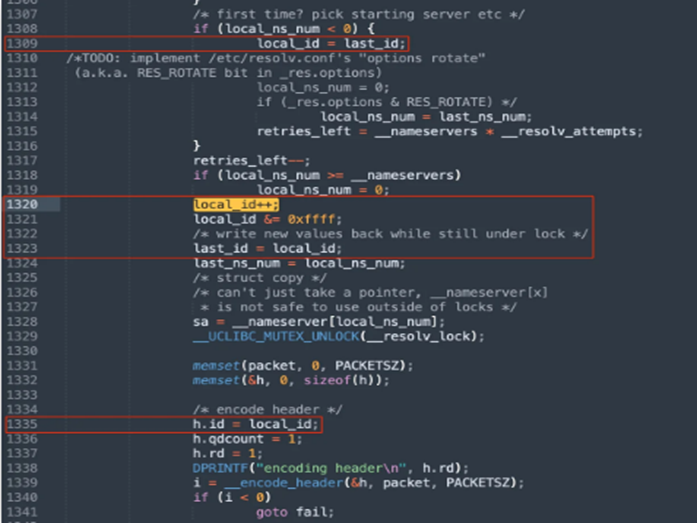
Experts discovered that the DNS lookup request’s transaction ID was predictable and a DNS poisoning attack might be possible under these circumstances.
Mitigation
According to the researchers, devices from more than 200 vendors are currently at risk of DNS poisoning or DNS spoofing attack. Therefore, it is recommended to increase your network visibility and security in both IT and OT environments.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.