Home Search
tools - search results
If you're not happy with the results, please do another search
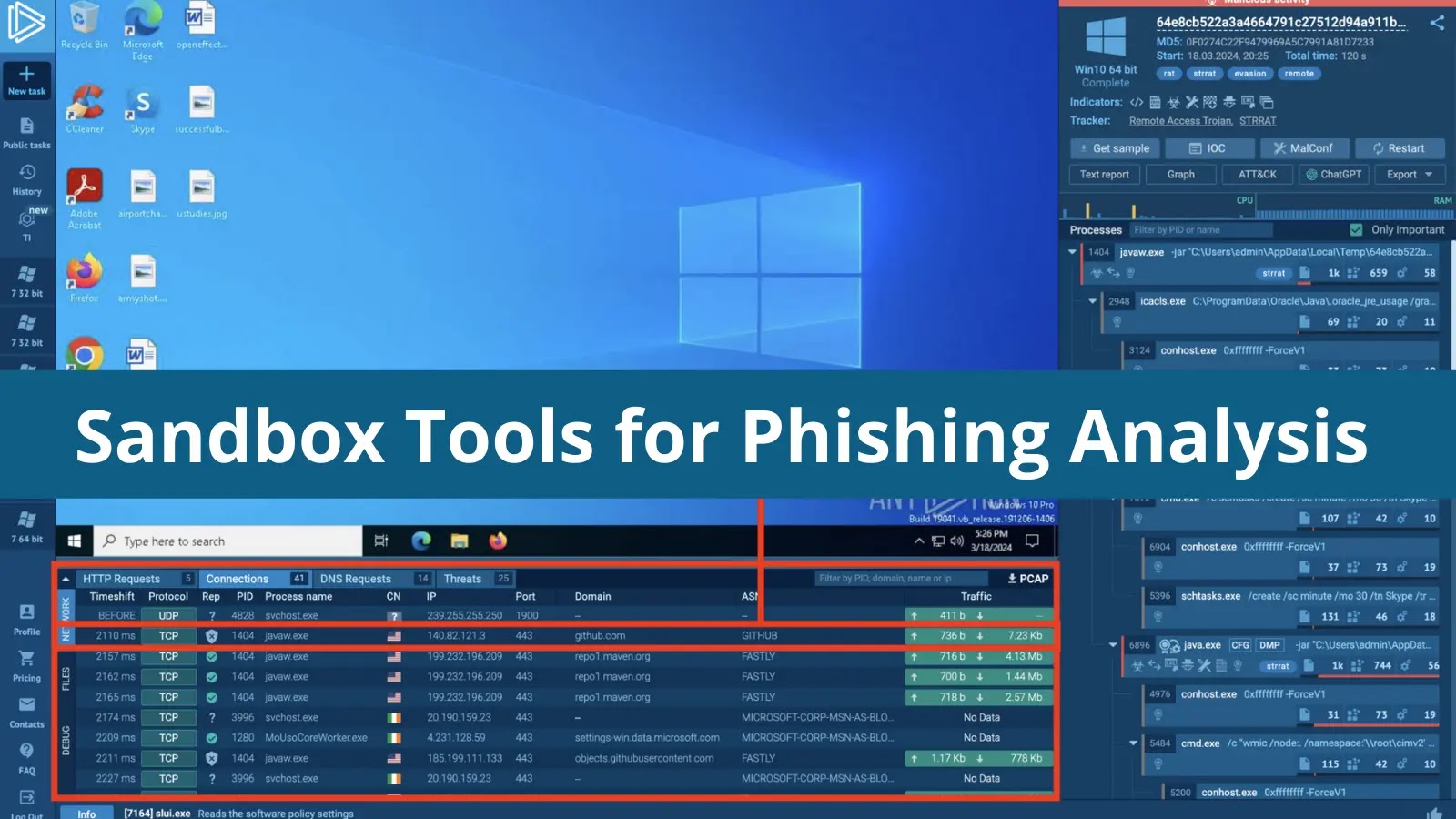
5 Sandbox Tools for Phishing Analysis in 2024
There is a wide variety of solutions one can use to investigate phishing attacks. Yet, in most cases, analysts can do with just one,...
Earth Hundun’s Hackers Employ Waterbear And Deuterbear Tools For Advanced Cyber Attacks
Hackers always keep evolving their tools to stay ahead of defense systems and exploit new vulnerabilities.
Cybersecurity researchers at Trend Micro reported that the Earth...
Fortinet Vulnerability Exploited To Deploy RMM tools And PowerShell Backdoors
Threat actors have been discovered exploiting a Fortinet Forticlient EMS vulnerability to install unauthorized RMM tools and PowerShell backdoors on the targeted systems.
The vulnerability...
Microsoft Adds 5 New AI Tools to be Added with Azure AI
Microsoft has unveiled a suite of new tools within its Azure AI Studio.
These innovations are designed to address the growing concerns around prompt...
Agent Tesla’s Added New Tools & Tactics to Its Arsenal
The persistent search for money and the threat actors increasingly becoming more sophisticated are driving the alarming rate of malware change.
Every day, new types...
How to Quickly Remove White Backgrounds From Images With the Help of Online Tools
A white image background is often confused with a transparent one. After all, no specific color is distracting you from the main object. Also,...
12 Best Vulnerability Management Tools 2024
Vulnerability Management Tools play a significant role in detecting, analyzing, and patching vulnerabilities in web and network-based applications.
Vulnerability, risk, and threat are the...
6 Best Free Malware Analysis Tools to Break Down the Malware Samples – 2024
The malware analysis tools simply allow us to quickly and effectively determine what actions a threat takes in the system.
This method easily collects...
Kali Linux 2024.1 Released with New Hacking Tools – What’s New!
Kali Linux 2024.1 was released, marking the year's first release with new hacking tools, visual elements, and updates.
Kali Linux, a Debian-derived OS by...
CyberSec Firm i-Soon Leak Exposes The Tools Used By Chinese Hackers
A cybersecurity company data breach could be extremely damaging as it not only compromises sensitive client information but also corrupts the trust in the...




.png)


-1.webp)





.webp)